Supermicro’s January 2025 advisory addressed three vulnerabilities in its Baseboard Management Controller (BMC) firmware validation logic, including CVE-2024-10237 a design flaw that allowed malicious firmware updates by manipulating the signature verification process.
Despite vendor patches introducing offset and attribute checks, researchers at Binarly demonstrated an effective bypass, resulting in CVE-2025-7937.
A subsequent analysis uncovered CVE-2025-6198 in other Supermicro products, revealing a distinct exploitation technique that also undermines Root of Trust (RoT) protections.
Incomplete Fix Leads to CVE-2025-7937
Supermicro’s BMC update process consists of three steps: extracting the embedded RSA-4096 public key and image signature, parsing the fwmap table to identify signed regions, and computing a SHA-512 hash over concatenated signed segments for signature verification.
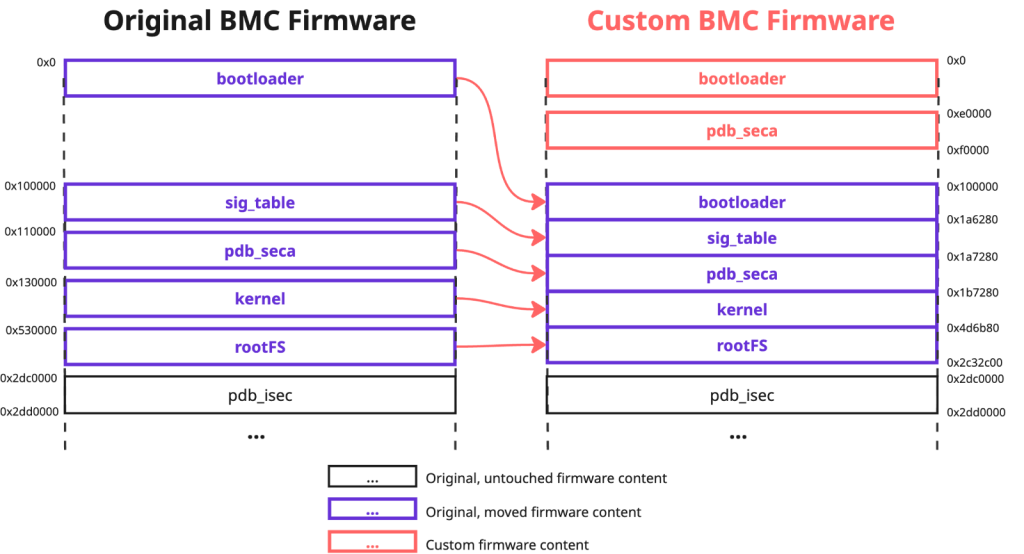
CVE-2024-10237 exploited the fact that attackers could inject a custom fwmap table entry ahead of the original, remapping all signed regions into a single contiguous block while relocating legitimate bootloader data to reserved space.
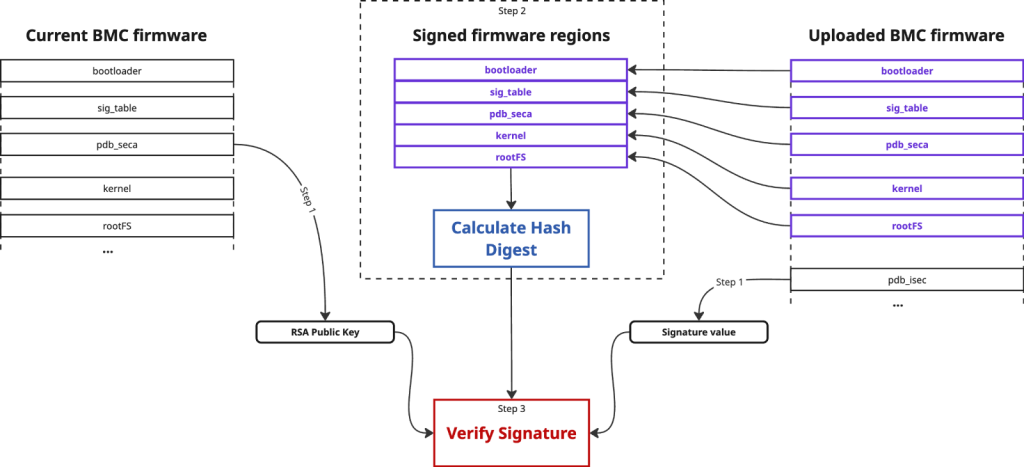
The patch added fwmap_offset_check and fwmap_attr_check to restrict entry offsets and enforce a whitelist of recognized regions. However, Binarly’s proof-of-concept placed a rogue fwmap entry at the approved offset 0x100000 using the “bootloader” identifier, encompassing all signed segments.
This entry passed offset and attribute checks, enabling the arbitrary replacement of the bootloader and persistent code execution in the BMC context. Supermicro PSIRT confirmed the bypass as CVE-2025-7937 after reviewing the provided PoC firmware image.
Sig_Table Manipulation Yields CVE-2025-6198
While examining the X13SEM-F motherboard’s BMC signed update logic within the OP-TEE environment, Binarly found similar weaknesses in the alternative sig_table format. This table, located at offset 0x100000, defines six regions: bootloader, sig_table, pdb_seca, kernel, and two rootFS parts.
Because sig_table resides entirely within the uploaded image, it can be modified alongside other segments.
In the PoC, researchers altered 0x200 bytes of the kernel at offset 0x1c5600, split the original kernel data into two fragments, and updated the sig_table entries to include both fragments, as well as the genuine segments.
The computed digest matched the original signature, allowing the compromised image to flash. UART debugging confirmed injection of custom kernel code during boot, demonstrating that RoT only authenticates the bootloader stage and neglects downstream components.
Both CVE-2025-7937 and CVE-2025-6198 highlight the insufficiency of single-stage signature checks and the importance of layered validation throughout the firmware and boot process.
Administrators must apply the latest firmware updates, verify SHA-256 hashes against vendor-published values, and enable hardware RoT features (e.g., Aspeed AST2600). Continuous BMC monitoring and regular security audits are crucial for detecting unauthorized modifications.
The Binarly Transparency Platform offers code-level detection and proactive analysis to identify such low-level threats before deployment. Continuous monitoring of BMC behavior and routine security audits are also crucial for detecting unauthorized modifications.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates