Cybersecurity researchers at Tier Zero Security have unveiled a dangerous new Beacon Object File (BOF) tool that exploits a critical vulnerability in Microsoft Teams’ cookie encryption system.
The tool, called teams-cookies-bof, enables attackers to steal user chat messages and sensitive communications without needing elevated administrator privileges.
This discovery highlights a significant security gap between Microsoft Teams and modern Chromium-based browsers like Chrome and Edge.
The Vulnerability Behind the Attack
The core issue lies in how Microsoft Teams protects its encryption keys compared to contemporary browsers.
While Chrome and Edge use a COM-based IElevator service that runs with SYSTEM privileges to secure encryption keys, Microsoft Teams relies on the current user’s Data Protection API (DPAPI) master key.
This weaker protection mechanism creates an opportunity for attackers operating at standard user-level privileges to decrypt cookies and access sensitive data.
Microsoft Teams utilizes msedgewebview2.exe, a Chromium-based component, to display browser content within the application.
When users authenticate, Teams stores cookies in a SQLite database similar to regular web browsers.
However, the encryption key protecting these cookies can be accessed through the user’s DPAPI master key, making extraction significantly easier for threat actors compared to modern browser implementations.
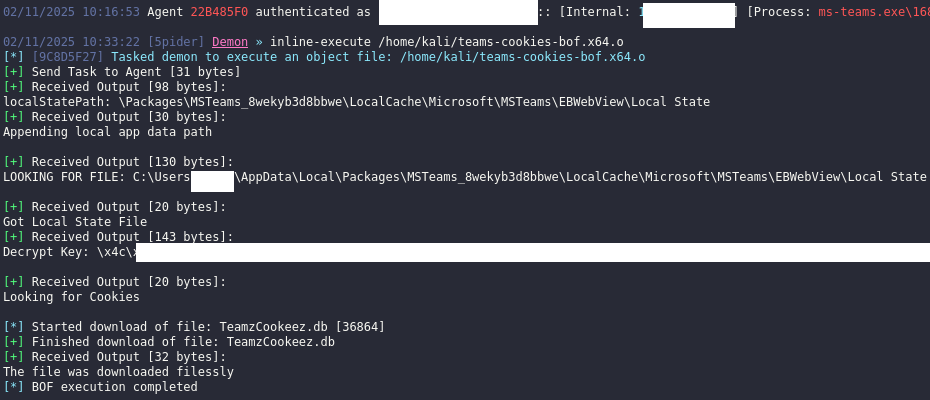
The teams-cookies-bof tool represents a modified version of the Cookie-Monster-BOF framework, specifically adapted to target Microsoft Teams vulnerabilities.
The attack methodology operates within the ms-teams.exe process context, searching for the web view child process that maintains an open handle to the cookies file.
Previous Teams cookie theft attempts faced a major limitation: the cookies file remained locked while the Teams application was running.
Researchers discovered that the new BOF approach circumvents this obstacle by operating within the process itself through techniques like DLL or COM hijacking, eliminating the need to terminate the Teams process entirely.
The tool takes no arguments and can run within any Command and Control framework supporting BOF execution.
The attack process involves duplicating the file handle, reading the cookie file content, and decrypting the encryption key using the current user’s DPAPI master key.
Importantly, the decryption logic remains identical to the original Cookie-Monster-BOF tool, ensuring compatibility with various C2 frameworks.
Once attackers obtain decrypted cookies, they gain access to authentication tokens enabling interaction with Teams, Skype, and Microsoft Graph APIs.
This access allows threat actors to read existing Teams messages, send messages impersonating victims, and potentially access other Microsoft 365 resources within the user’s organizational scope.
Stolen tokens can be leveraged with post-exploitation tools like GraphSpy to expand attacks across Microsoft’s entire ecosystem.
Organizations using Microsoft Teams should prioritize implementing endpoint detection and response solutions capable of monitoring unusual process behavior, handling duplicate activities, and unauthorized access attempts to Teams cookie databases.
Security teams should also consider restricting user-level access to sensitive data and implementing additional authentication controls for Microsoft 365 applications.
The compatibility of this tool with multiple C2 frameworks makes it easily adoptable by various threat actors and red team operators, emphasizing the urgency of deploying comprehensive security measures across Microsoft Teams deployments.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today