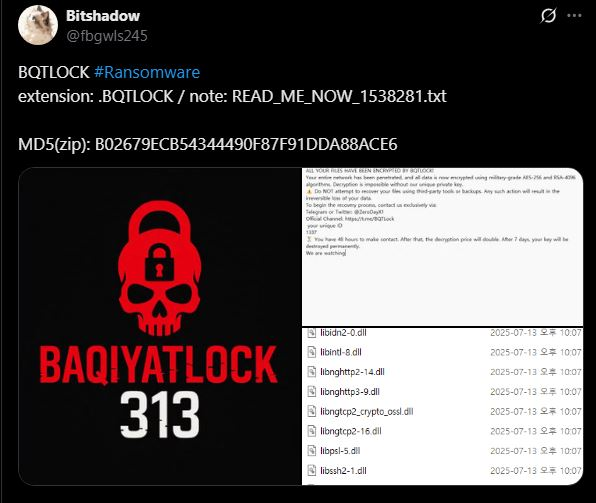
A newly identified ransomware strain called Bqtlock has emerged in the cybercrime landscape, operating under a Ransomware-as-a-Service (RaaS) model since mid-July 2025.
The malware is associated with ZerodayX, the alleged leader of the pro-Palestinian hacktivist group Liwaa Mohammed, who has previously been linked to the Saudi Games data breach.
Bqtlock follows the standard double extortion methodology, demanding payments ranging from 13 to 40 XMR ($3,600 to $10,000) based on the severity of the attack.
The ransomware threatens victims with a 48-hour deadline to establish contact via Telegram or X platforms.
Suppose victims fail to respond within this timeframe, the ransom demand doubles, and after seven days. In that case, the decryption keys are permanently deleted, while the stolen data is sold on the attackers’ website.
Technical Analysis and Capabilities
The malware is distributed as a ZIP archive containing Update.exe, which encrypts local files and appends the .bqtlock extension.
Bqtlock implements sophisticated anti-analysis techniques, including string obfuscation, debugger detection through IsDebuggerPresent() API, and virtual machine evasion capabilities.
The ransomware performs process hollowing by targeting explorer.exe for stealthy payload execution. It conducts comprehensive system reconnaissance, collecting computer names, usernames, IP addresses, hardware IDs, and disk space information.
The malware establishes persistence by creating a local administrator account named “BQTLockAdmin” with the password “Password123!” and adds this account to the Administrators group.
For data exfiltration, Bqtlock abuses Discord webhooks to transmit collected system information in JSON format. The malware captures desktop screenshots and stores them as C:\Windows\Temp\bqt_screenshot.png using BitBlt and GdipCreateBitmapFromHBITMAP APIs.
Enhanced Evasion and Persistence
To prevent system recovery, Bqtlock executes anti-recovery commands that disable Windows recovery mechanisms.
The ransomware terminates specific security processes using the CreateToolhelp32Snapshot API and establishes persistence through Windows Scheduled Tasks named “Microsoft\Windows\Maintenance\SystemHealthCheck.”
The malware employs hybrid encryption, utilizing AES-256 with RSA-4096, to generate random 32-byte AES keys and 16-byte initialization vectors. All critical components, including ransom notes, file extensions, wallpaper images, and Discord C2 URLs, are embedded in Base64 format.
An updated variant discovered in August 2025 includes additional anti-debugging checks, UAC bypass methods using CMSTP, fodhelper.exe, and eventvwr.exe, as well as credential-stealing capabilities targeting Chrome, Firefox, Edge, Opera, and Brave browsers.
The RaaS offers three subscription tiers with customizable features, including ransom notes, wallpapers, file extensions, and anti-analysis options.
Despite claims of being fully undetectable, security researchers have identified questionable promotional tactics and limited actual deployment evidence, suggesting the threat may be overhyped by its developers.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates