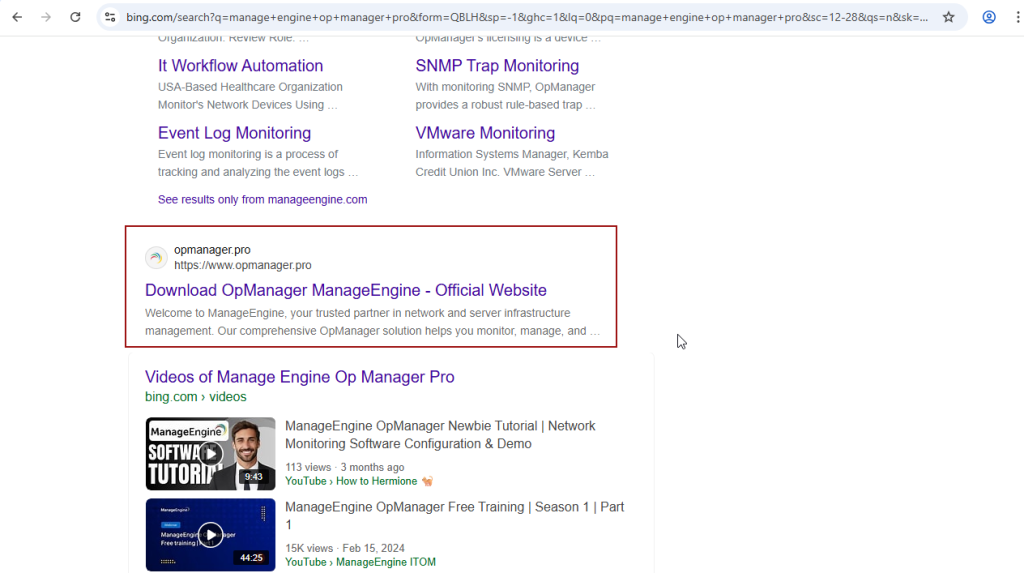
A sophisticated malware campaign leveraging the notorious Bumblebee loader has targeted enterprise environments by exploiting Bing search results for popular IT tools, most notably “ManageEngine OpManager”.
The campaign, using SEO poisoning, delivers Trojanized installers to unsuspecting administrators, leading to full-scale ransomware incidents.
SEO Poisoning Delivers Initial Access to Bumblebee
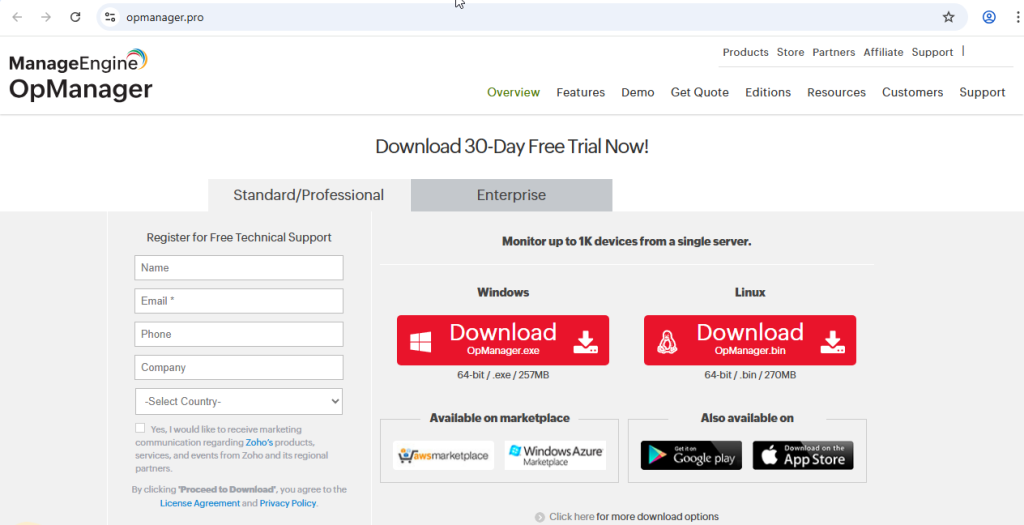
The attack begins when a user searches for “ManageEngine OpManager” on Bing and clicks on a search result leading to a malicious domain (opmanager[.]pro).
There, a seemingly legitimate MSI installer, ManageEngine-OpManager.msi, is offered for download. Executing this file installs the genuine software, but in the background, it side-loads msimg32.dll into consent.exe, a technique that effectively loads the Bumblebee malware onto the system.
Researchers confirmed that Bumblebee established command and control using distinctive DGA (Domain Generation Algorithm) domains and C2 IPs such as 109.205.195[.]211 and 188.40.187[.]145. Crucially, the campaign specifically targeted privileged IT and Active Directory administrator accounts, granting threat actors expansive access after just one compromised host.
Rapid Escalation: Credential Theft, Lateral Spread, and Ransomware
Within hours, the attackers used Bumblebee to deploy secondary payloads, such as an AdaptixC2 beacon, for more robust persistence and post-exploitation.
Armed with administrative credentials, harvested through NTDS.After performing the dump (via wbadmin.exe) and LSASS memory scraping (using rundll32.exe with comsvcs.dll), the intruders moved laterally via RDP sessions and newly created high-privilege domain accounts.
Persistence was ensured by installing legitimate-looking remote access utilities, like RustDesk, and setting up SSH tunnels to external servers for covert operations.
Internal reconnaissance and data staging followed: tools like SoftPerfect Network Scanner (renamed n.exe) scanned the network, and credentials from Veeam backup databases were dumped using psql.exe. Exfiltration activities included SFTP transfers of staged data to external drop servers.
The ultimate payload was Akira ransomware (locker.exe), which was deployed to encrypt both local data and remote network shares, halting business operations.
In several cases, attackers returned days later, using established persistence to re-encrypt systems in additional domains, dramatically increasing the disruptive impact.
Industry-Wide Impact and Defensive Recommendations
Multiple organizations, including confirmed victims in Europe, have been hit by this campaign throughout July 2025. Incident response teams report “time to ransomware” (TTR) as low as nine hours from initial access in some cases, underscoring the need for urgent detection and response.
Security experts advise:
- Restrict installation of admin tools to verified sources.
- Monitor for unexpected MSI installations, abnormal system reconnaissance, and privilege escalation events.
- Hunt for known indicators of compromise such as malicious MSI hashes, suspicious DGA DNS activity, and the creation of new admin accounts.
This campaign serves as a stark reminder of the potent risks posed by SEO poisoning, the lure of IT tool downloads, and the agility of modern ransomware operations leveraging loaders like Bumblebee.
Indicators of Compromise (IOCs)
Domains:
ev2sirbd269o5j.org (Bumblebee DGA domain)
2rxyt9urhq0bgj.org (Bumblebee DGA domain)
DFIR Report:
opmanager[.]pro (Malicious site for trojanized installer)
angryipscanner.org (Malicious site for trojanized installer)
axiscamerastation.org (Malicious site for trojanized installer)
Swisscom B2B CSIRT:
ip-scanner[.]org (Malicious site for trojanized installer)
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates