A global surge in Android device infections has been traced to PlayPraetor, a sophisticated Remote Access Trojan (RAT) distributed by Chinese-speaking threat actors leveraging a Malware-as-a-Service (MaaS) model.
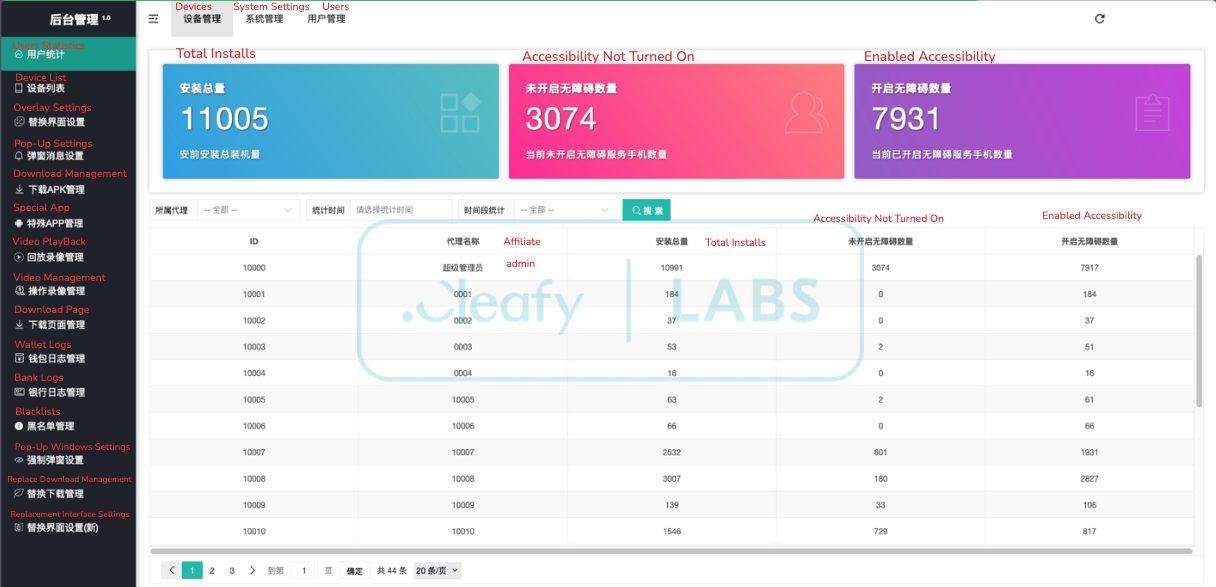
Investigations by Cleafy Labs reveal that, in under three months, PlayPraetor infected more than 11,000 Android devices worldwide.
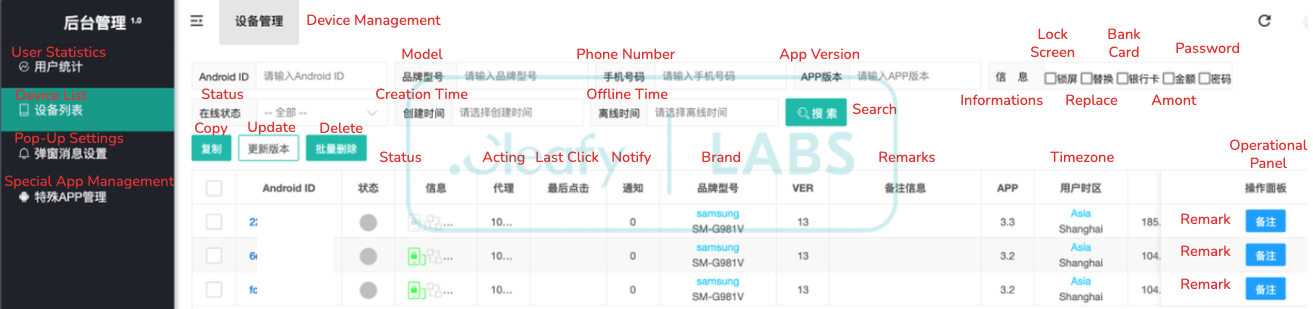
The operation’s scalability is powered by a Chinese-language Command and Control (C2) panel, designed with a multi-tenant architecture that enables multiple affiliates to independently manage campaigns and victim pools.
This model supports aggressive expansion, with over 2,000 new infections occurring weekly—driven by automated tools that allow attackers to rapidly create convincing, malicious app download pages mimicking legitimate Google Play Store sites.
The approach has drastically lowered barriers for cybercriminals, allowing even those with limited expertise to orchestrate complex fraud operations on a global scale.
Targeted Expansion: Europe & Hotspots at Risk
Analysis of the botnet’s C2 infrastructure and infection data reveals a calculated strategy, rather than indiscriminate spread.
Europe is currently the epicenter, accounting for 58% of infections, with high concentrations in Portugal, Spain, and France.
Other hotspots include Morocco in Africa, Peru in Latin America, and Hong Kong in Asia. PlayPraetor’s affiliate network is hierarchical, dominated by two principal operators who control nearly 60% of active infections, especially among Portuguese-speaking targets.
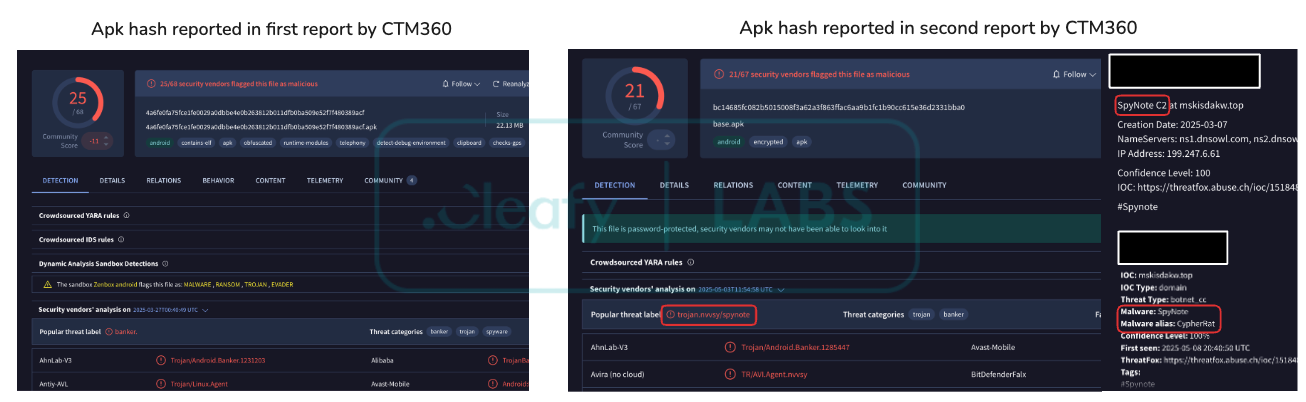
However, recent weeks have seen a pronounced shift in focus: infections among Portuguese speakers are flattening, while incidents targeting Spanish and French-speaking users have dramatically increased.
The skew is evidenced by the botnet’s weekly surge of new infections in Spanish- and French-speaking regions, signaling a strategic pivot and an escalating risk to financial institutions and their customers in these markets.
- Europe accounts for 58% of all PlayPraetor infections, with Portugal, Spain, and France most heavily targeted.
- Morocco has become a hotspot in Africa, with Peru and Hong Kong also seeing significant infection rates.
- Two main affiliates control almost 60% of active infections, focused heavily on Portuguese-speaking victims.
- Recent weeks show rapid growth in infections among Spanish- and French-speaking users, marking a major shift in targeting.
- This evolution poses a rapidly increasing risk to banks and financial customers across these emerging regions.
Tech Sophistication: Device Takeover to Rapid Campaigns
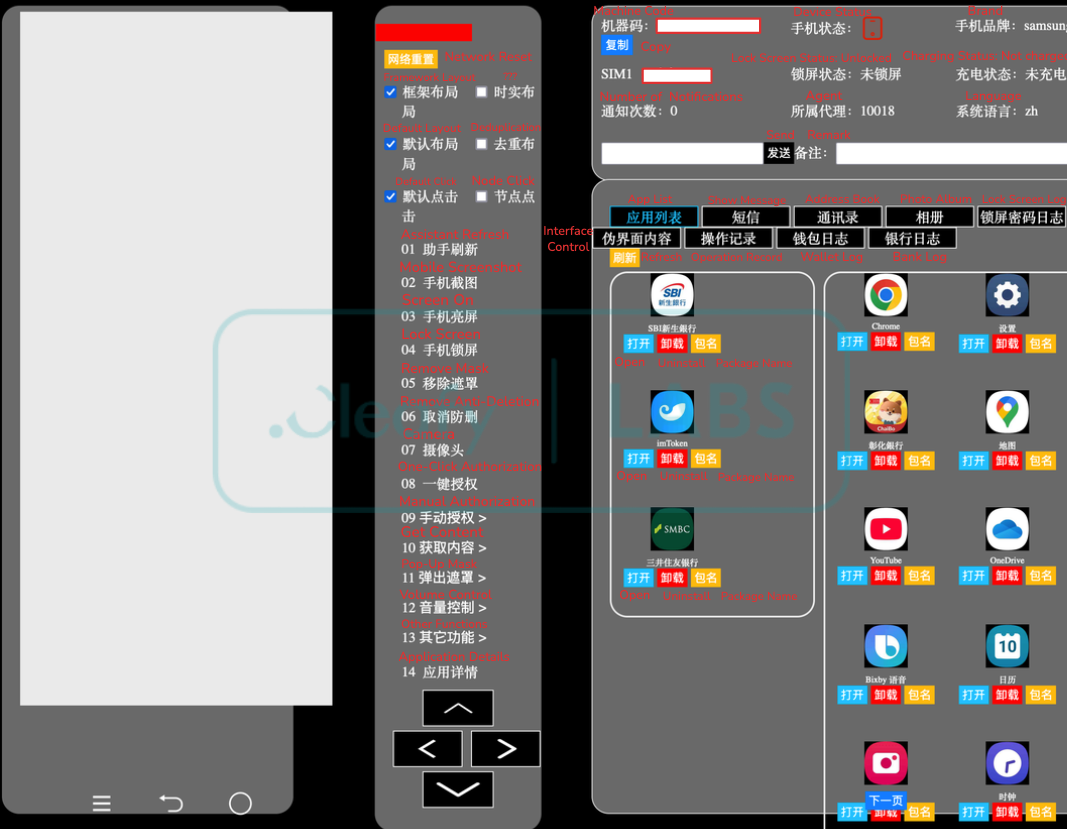
PlayPraetor’s strength lies not only in scale but its advanced capabilities. The RAT abuses Android’s Accessibility Services to gain real-time control over compromised devices—enabling attackers to perform fraudulent transactions, harvest credentials, intercept SMS, and capture screenshots.
Its communication utilizes multiple protocols: resilient HTTP/HTTPS for initial contact, WebSocket for immediate operator commands, and RTMP for live screen streaming of victims’ devices.
Its campaign is marked by relentless innovation: the malware’s command set was recently streamlined, with legacy functions pruned while new capabilities—such as expanded device control and streamlined campaign creation—were introduced.
Central to this crimeware is the C2 panel, written in Chinese and built to empower affiliates with everything needed for orchestrating fraud, including on-demand generation of phishing pages that convincingly impersonate trusted brands.
This aligns with a broader trend in recent financial malware, exemplified by overlapping campaigns like ToxicPanda and SuperCard X, both orchestrated by Chinese-speaking actors and targeting banking institutions across continents.
PlayPraetor marks a significant escalation in Android banking threats, combining an adaptive, multi-affiliate infrastructure with technical sophistication and aggressive expansion.
Its relentless innovation and modular tactics exemplify the threat posed to global financial systems by the modern cybercriminal ecosystem.
Indicators of Compromise (IOCs)
| Malware Sample Hash | App Name |
|---|---|
| 1b022ac761a077f0116bb427b6cf8315a86aa654ae0cd55a6616647bbeb769c4 | Nielsen |
| d392372928571662e4e59b0e3ff52a0e39a8f062633a4f5bdafc681bcdcdcf22 | Google Chrome |
| C2 Infrastructure | Description |
|---|---|
| mskisdakw[.]top | Bot Communications Domain |
| fsdlaowaa[.]top | Bot Communications Domain |
| 199.247.6[.]61 | Bot Communications IP |
| Delivery Page Domain |
|---|
| djp[.]center |
| kmyjh[.]top |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates