A consolidated intelligence report attributes a series of sophisticated espionage operations against global telecommunications infrastructure to Salt Typhoon, an advanced persistent threat group aligned with China’s Ministry of State Security (MSS).
Active since at least 2019, Salt Typhoon has weaponized zero-day and publicly known vulnerabilities in enterprise routers, VPN gateways, and firewalls to implant custom firmware rootkits.
Operators employ living-off-the-land binaries, such as certutil and rundll32.exe, to fetch stealthy payloads over encrypted HTTPS channels, masquerading as routine firmware updates.
Implant beacons are configured with randomized intervals between twelve and thirty-seven minutes, a tactic designed to bypass standard hourly anomaly detection and maintain undetected persistence for months.
Contractor Ecosystem and Domain Infrastructure
Salt Typhoon’s industrial-scale operations are enabled by a network of front companies and pseudo-private contractors, most notably Sichuan Juxinhe Network Technology and Beijing Huanyu Tianqiong Information Technology.
These entities provision ProtonMail-registered domains, examples including cloudprocenter[.]com and requiredvalue[.]com, using fabricated U.S. personas such as Shawn Francis and Monica Burch.
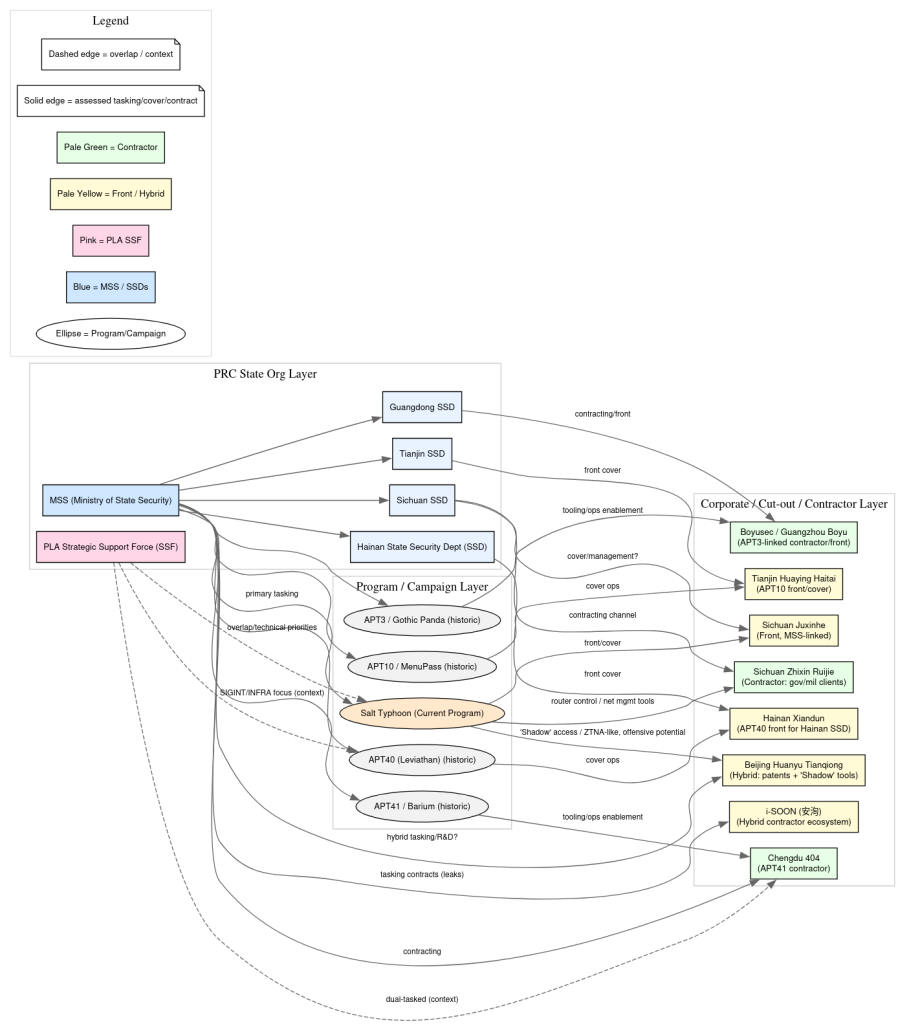
Between 2020 and 2025, more than 45 domains were registered via centralized pipelines linked to i-SOON (Anxun Information Technology Co., Ltd.), each secured with domain-validated SSL certificates issued by GoDaddy Secure and Sectigo.
Despite these operational security lapses, the contractor-driven model facilitated rapid scaling of command-and-control infrastructure, blending the appearance of legitimate service portals with covert staging environments.
Targeting Profile and Data Exfiltration
The group’s primary targets include lawful intercept systems, VoIP configuration databases, and subscriber metadata repositories within major telecom providers.
During a late-2024 breach, Salt Typhoon hijacked firewall management interfaces at AT&T, Verizon, and T-Mobile, duplicating lawful intercept pipelines and exfiltrating millions of call detail records along with session metadata.
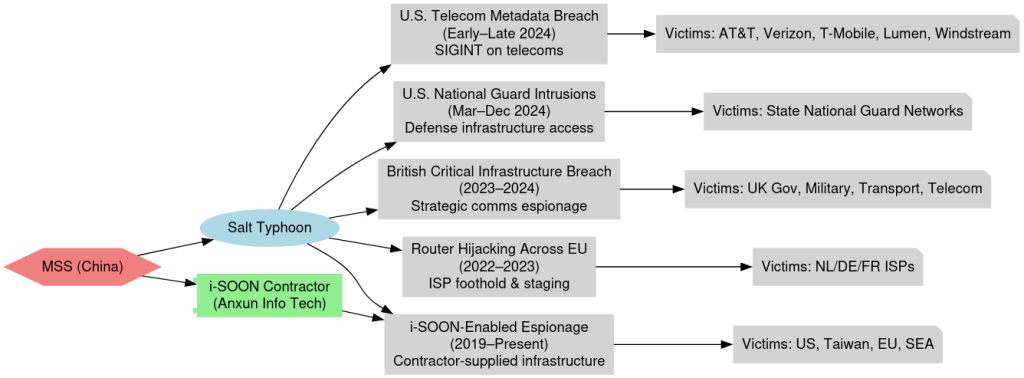
In parallel, state National Guard VPN portals were compromised, resulting in the exposure of network diagrams, credentials, and incident response documentation.
Similar tactics were observed against European ISPs in the Netherlands, Germany, and France, where custom router implants and backdoored firmware updates facilitated passive SIGINT collection.
These operations underscore Salt Typhoon’s strategic emphasis on long-term metadata harvesting to inform both peacetime espionage and wartime communications disruption planning.
Named Operators and Legal Actions
U.S. Department of Justice indictments have named Yin Kecheng of Sichuan Juxinhe as the technical architect responsible for implant deployment and command routing.
Zhou Shuai, alias “Coldface,” formerly of Shanghai Heiying Information Technology and an i-SOON consultant, faces charges for brokering stolen data resale and orchestrating domain infrastructure.
Their distinct roles, one focusing on hands-on exploitation and the other on strategic logistics, reflect Salt Typhoon’s layered adversary structure, which mirrors corporate operational design.
Strategic Mitigation Strategies
Defenders can counter Salt Typhoon’s infrastructure by tracking passive DNS clusters associated with OrderBox and MonoVM name servers, fingerprinting GoDaddy and Sectigo SSL certificates for anomalous patterns, and auditing firmware integrity on edge devices.
Implementing multi-factor authentication on management portals and segmenting networks to isolate lawful intercept systems can further hamper unauthorized access.
Sharing domain registration IOCs and operational patterns among telecom providers, CERTs, and intelligence agencies will be essential to disrupting the group’s next wave of contractor-enabled campaigns before they mature into active operations.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates