Cybersecurity researchers at IBM X-Force identified a new wave of cyberattacks orchestrated by the China-aligned threat actor Hive0154.
The campaign leverages the Pubload malware, distributed via spear-phishing emails that exploit sensitive topics relevant to the Tibetan community.
This activity coincides with heightened global attention on Tibet, particularly surrounding the Dalai Lama’s 90th birthday and recent international events focused on Tibetan sovereignty.
Hive0154’s latest campaign is characterized by the use of lure documents and filenames referencing high-profile Tibetan issues.
Notably, phishing emails have referenced the 9th World Parliamentarians’ Convention on Tibet (WPCT) held in Tokyo, China’s education policy in the Tibet Autonomous Region (TAR), and the Dalai Lama’s recent publication “Voice for the Voiceless.”
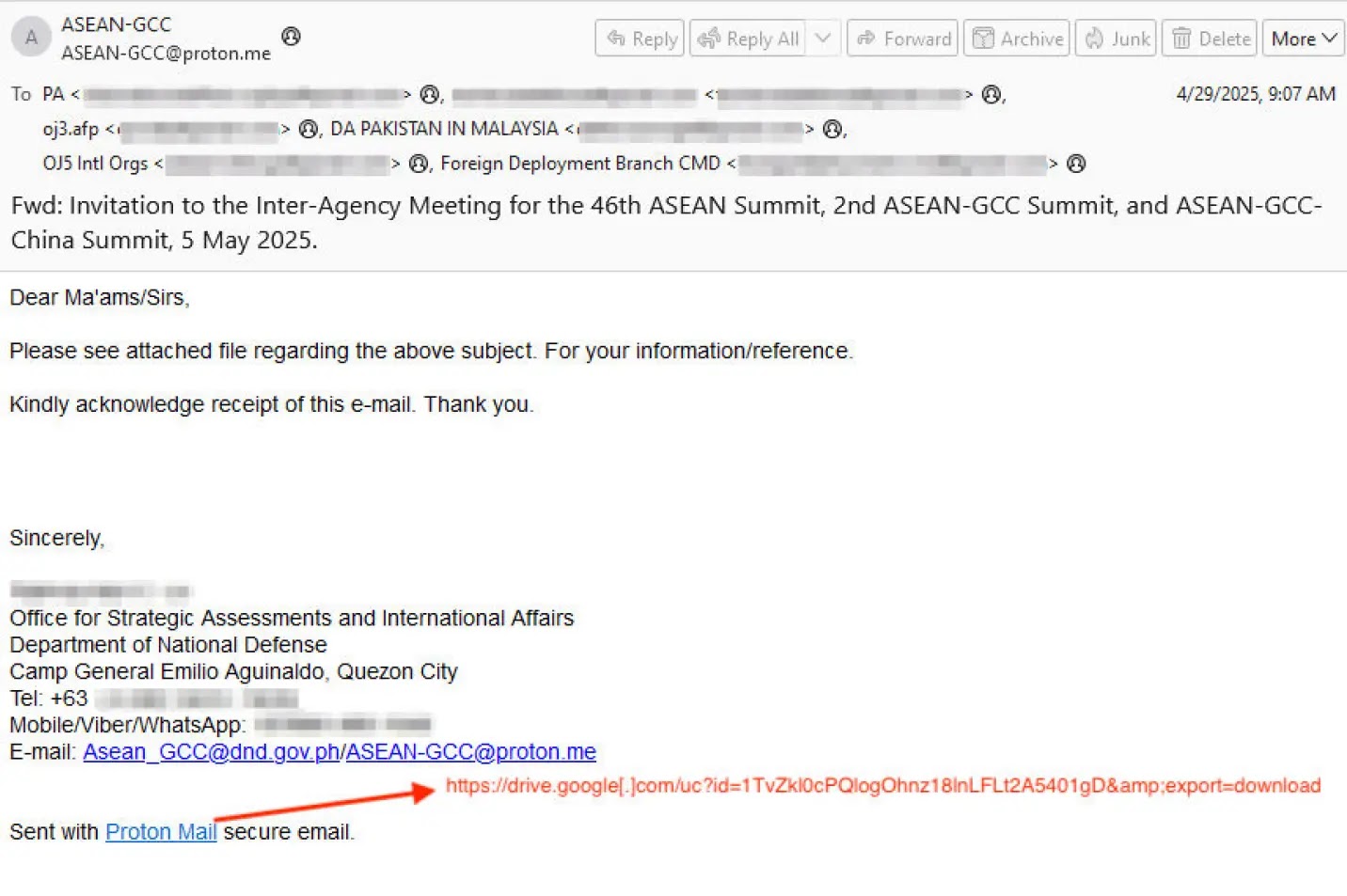
According to IBM X-Force Report, these lures are designed to increase the likelihood of engagement from recipients within the Tibetan community and their supporters.
The phishing emails typically contain links to Google Drive-hosted archives, which, when downloaded, include both benign documents and malicious executables.According to IBM X-Force
The malicious files are often disguised with filenames identical to legitimate documents or images, such as “9th WPCT Region-Wise Action Plans on Tibet.exe” or “Voice for the Voiceless photos.exe.” This tactic increases the risk of accidental execution by unsuspecting users.
Pubload Infection Chain
The infection chain begins with the delivery of a weaponized archive containing a benign executable vulnerable to DLL sideloading and a malicious Claimloader DLL.
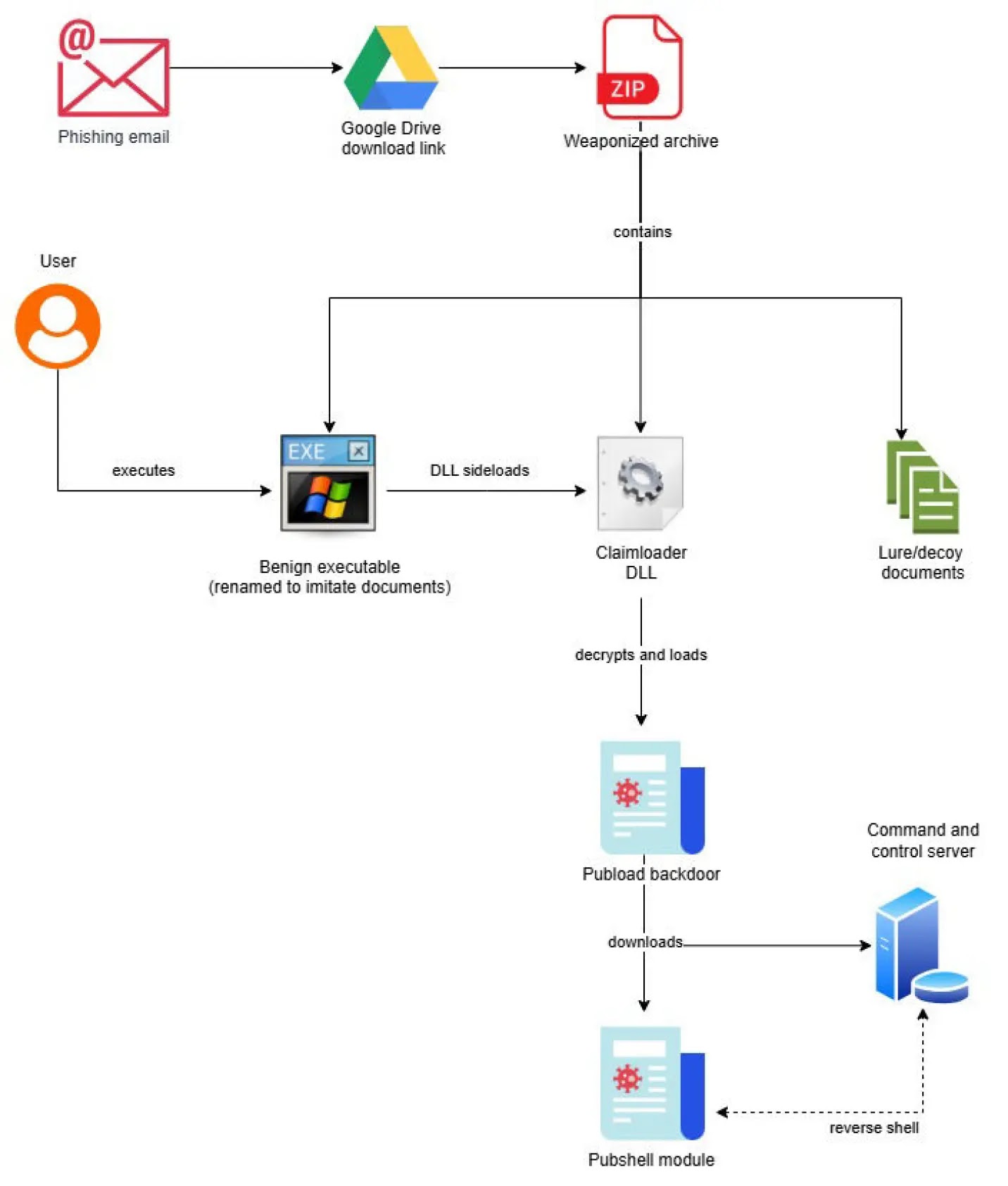
Once executed, Claimloader establishes persistence by creating a mutex and relocating itself to a concealed directory, such as C:\ProgramData\AdobeLicensingPlugin\. It then modifies the Windows registry to ensure execution upon user login.
The loader decrypts and injects an embedded Pubload payload using TripleDES encryption and dynamically resolves API imports.
After a series of timed delays, the shellcode is executed in memory, leading to the deployment of the Pubload backdoor.
Pubload, in turn, downloads additional payloads such as the Pubshell module, which provides attackers with a reverse shell for immediate remote access.
Broader Targeting
While the primary focus of this campaign is the Tibetan diaspora, Hive0154 has also targeted entities in the United States, including files referencing U.S. Navy Pacific Fleet working groups and strategic mineral policy discussions.
The group’s phishing tactics are highly adaptive, with filenames and lure content tailored to the geopolitical interests of their intended victims.
Hive0154, also tracked as Mustang Panda, Stately Taurus, and other aliases, is known for its extensive malware arsenal and persistent targeting of government, policy, and advocacy organizations.
The group’s use of custom loaders, backdoors, and USB worms underscores its sophistication and ongoing evolution.
Security experts advise organizations, especially those involved in Tibetan advocacy or related geopolitical matters, to exercise extreme caution with unsolicited emails, particularly those containing download links or archives.
Network defenders should monitor for suspicious file activity, persistence mechanisms in the registry, and unusual outbound connections especially those involving TLS 1.2 packets without a preceding handshake, which may indicate Pubload or related malware activity.
Indicators of Compromise (IOC)
| Indicator | Type | Context |
|---|---|---|
| 2bd60685299c62abe500fe809f03a627a1567059ce213d7c0cc762fa32552d7 | SHA256 | Claimloader DLL |
| c80dfc678570bde7c19df21877a15cc7914d3ef7a3cef5f99fce26fcf696c444 | SHA256 | Claimloader DLL |
| 93f1fd31e197a58b03c6f5f774c1384ffd03516ab1172d9b26ef5a4a32831637 | SHA256 | Claimloader DLL |
| 3e7384c5e7c5764258947721c7729f221fb47ef53d447a7af5db5426f1e7c13d | SHA256 | Claimloader DLL |
| 8cd4324e1e764aafba4ea0394a82943cefd7deeee28a6cbd19f2ba69de6a5766 | SHA256 | Claimloader DLL |
| 7979686bf73c2988ab5d57f9605dcef2231ca87580f6ecedc75b2cbe81669ba0 | SHA256 | Weaponized archive |
| ea991719885b2fe91502218ff3be12c9f990a24c7e007e4ffb5a5c5c52b3a0b5 | SHA256 | Weaponized archive |
| 6e408aada775eaf19c524792344cabca0b406247154e2b03ed03a929e0feee5a | SHA256 | Weaponized archive |
| 57770ede7015734e2d881430423bcc76c160b90448f5e67334e56b9747ff874c | SHA256 | Weaponized archive |
| fb33f222b3d4d5edc9b743e64282de561ef51e42db150dd8086203c53b25ff79 | SHA256 | Weaponized archive |
| 218.255.96[.]245:443 | IPv4 | Pubload C2 server |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates