Kaspersky researchers uncovered a sophisticated cyberespionage campaign in March 2025 that leveraged a powerful Chrome zero-day vulnerability to deploy previously unknown commercial spyware.
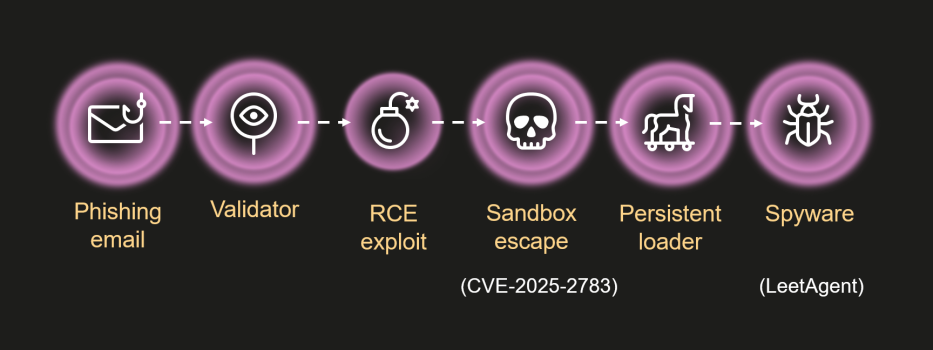
The attack, dubbed Operation ForumTroll, targeted Russian media outlets, universities, research centers, government organizations, and financial institutions through personalized phishing emails disguised as invitations to the Primakov Readings scientific forum.
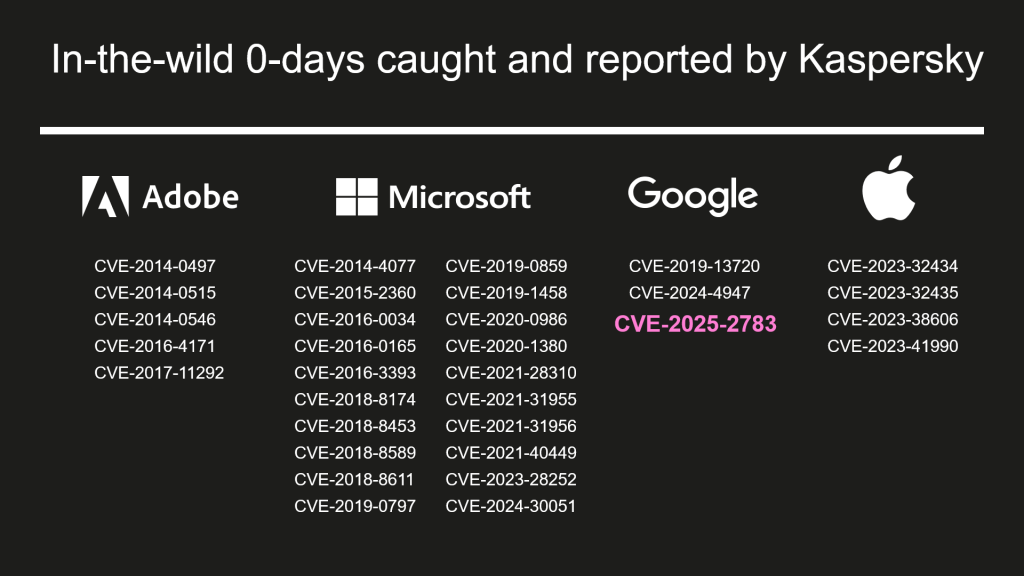
The campaign exploited CVE-2025-2783, a Chrome sandbox escape vulnerability that allowed attackers to bypass browser security protections without performing obviously malicious actions.
Simply clicking a malicious link and visiting the weaponized website using Google Chrome or any Chromium-based browser was sufficient to trigger the infection.
No additional user interaction was required. Kaspersky reported the vulnerability to Google, which released patches in Chrome version 134.0.6998.177/.178. Mozilla subsequently identified similar weaknesses in Firefox and patched them under CVE-2025-2857.
Sophisticated Sandbox Escape Through Windows Quirk
The CVE-2025-2783 exploit is one of the most intriguing sandbox-escape techniques discovered by Kaspersky researchers. The vulnerability exploited an obscure Windows operating system quirk involving pseudo handles returned by the GetCurrentThread and GetCurrentProcess API functions.
Instead of returning actual handles, these functions return special constants that the kernel interprets as references to the current thread or process.
Chrome’s interprocess communication code already checked for the -1 pseudo handle constant associated with GetCurrentProcess, but failed to validate the -2 constant returned by GetCurrentThread.
When the exploit sent an ipcz RelayMessage containing the -2 pseudo handle through Chrome’s IPC broker, the DuplicateHandle API function converted it into a genuine handle to a thread in the browser process.
Attackers then used this handle to execute code gadgets by suspending the thread, modifying register values with SetThreadContext, and resuming execution to deploy their malware loader.
Connection to Italian Spyware Vendor
Kaspersky’s investigation traced the malware back to 2022 and revealed connections to commercial spyware called Dante, developed by Italian company Memento Labs, formerly known as Hacking Team.
The researchers discovered that Operation ForumTroll deployed LeetAgent spyware, which included commands written in leetspeak and capabilities such as keylogging, file stealing, and remote command execution.
In related attacks, investigators identified the more sophisticated Dante spyware, which employed extensive anti-analysis techniques including VMProtect obfuscation, anti-debugging checks, and anti-hooking mechanisms.
Code similarities between the exploit, loader, and Dante spyware, combined with shared infrastructure and tactics, led Kaspersky to conclude that Operation ForumTroll was conducted using tools developed by Memento Labs.
The company had rebranded from Hacking Team in 2019 after acquiring the controversial surveillance vendor. It publicly announced the Dante platform at the 2023 ISS World MEA conference for law enforcement and intelligence agencies.
Indicators of compromise
Kaspersky detections
Exploit.Win32.Generic
Exploit.Win64.Agent
Trojan.Win64.Agent
Loader
7d3a30dbf4fd3edaf4dde35ccb5cf926
3650c1ac97bd5674e1e3bfa9b26008644edacfed
2e39800df1cafbebfa22b437744d80f1b38111b471fa3eb42f2214a5ac7e1f13
LeetAgent
33bb0678af6011481845d7ce9643cedc
8390e2ebdd0db5d1a950b2c9984a5f429805d48c
388a8af43039f5f16a0673a6e342fa6ae2402e63ba7569d20d9ba4894dc0ba59
Dante
35869e8760928407d2789c7f115b7f83
c25275228c6da54cf578fa72c9f49697e5309694
07d272b607f082305ce7b1987bfa17dc967ab45c8cd89699bcdced34ea94e126
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates