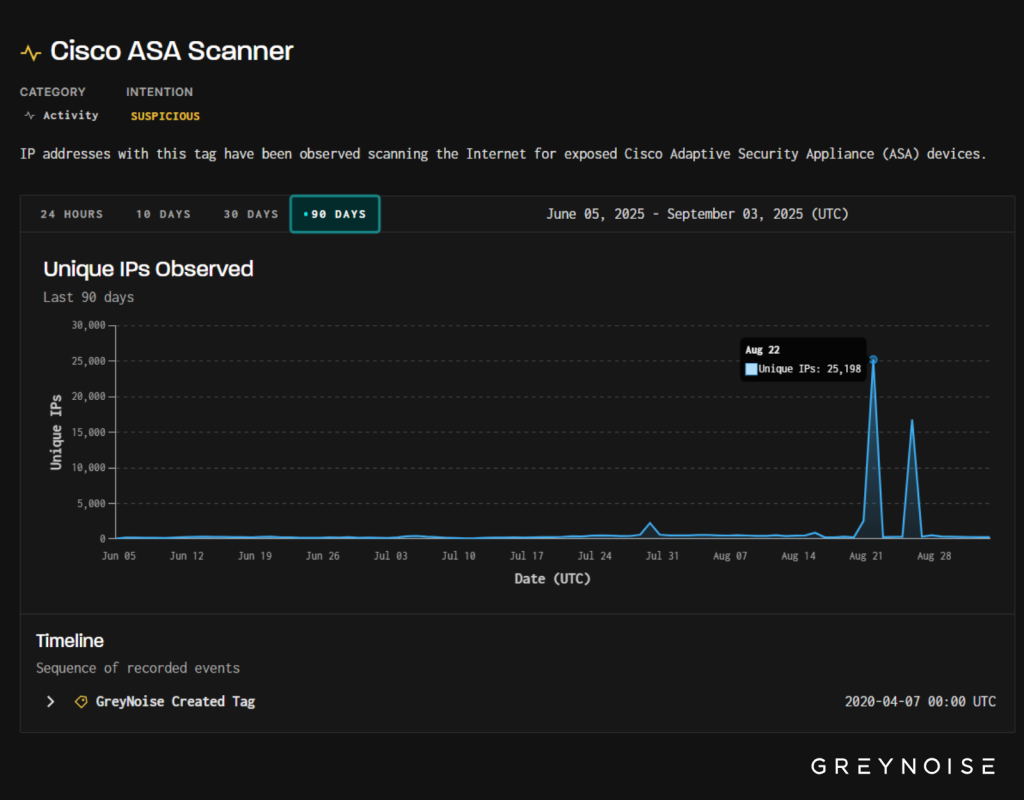
Late August witnessed two significant spikes in reconnaissance activity targeting Cisco Adaptive Security Appliance (ASA) devices, with scans surging far above baseline levels.
Security intelligence provider GreyNoise recorded over 25,000 unique source IPs probing the ASA web login path (/+CSCOE+/logon.html) in the first burst, followed days later by a smaller—but methodologically consistent—wave of scans.
Normally, daily scan volumes against ASA devices register below 500 IPs, making these events especially notable.
Coordinated Botnet Campaign Drives Brazil-Sourced Spike
Analysis of the event reveals a concentrated botnet cluster in Brazil as the primary driver.
By isolating a distinctive client fingerprint and reviewing two months of telemetry, GreyNoise identified that 16,794 unique IPs participated in ASA probes that day, 14,000 of which (over 80 percent) shared the same TLS and TCP signature set—confirming a unified scanning infrastructure.
The remaining 2,858 IPs represented less coordinated activity but still targeted Cisco ASA devices alongside IOS Telnet/SSH endpoints, indicating a campaign focused on Cisco platforms rather than random Internet-wide scanning.
Shared traits such as spoofed Chrome-like user-agents and overlapping client signatures underscore the use of a single toolkit across both August surges.
Targeting concentrated on the ASA web login portal, a known reconnaissance marker for exposed management interfaces.
Subsets of the same IP cohorts also engaged GreyNoise’s Cisco Telnet/SSH and ASA software personas, suggesting attempts to exploit weak or default credentials via automated brute-force or session hijacking techniques.
Geographically, source traffic triggering GreyNoise’s Cisco ASA Scanner tag originated predominantly from Brazil (64 percent), with Argentina and the United States each contributing 8 percent.
Targets were overwhelmingly in the United States (97 percent), followed by the United Kingdom (5 percent) and Germany (3 percent).
Note that target percentages may sum beyond 100 percent due to some IPs scanning multiple countries.
GreyNoise research into Early Warning Signals has demonstrated that scanning spikes often precede the public disclosure of new CVEs affecting the scanned platform.
Historical data shows similar surges in ASA scanning shortly before zero-day announcements.
The late-August bursts may thus foreshadow an imminent ASA vulnerability disclosure.
Even fully patched organizations can benefit from proactively blocking identified malicious IPs to reduce the risk of being targeted by exploit campaigns once a CVE is published.
Real-world precedents underline the stakes: the ArcaneDoor espionage campaign exploited two ASA zero-days (Line Dancer, Line Runner) to breach government networks, while ransomware groups like Akira and LockBit have incorporated ASA flaws into their playbooks.
The global weaponization of CVE-2020-3452 within days of disclosure further exemplifies the rapid exploitation window.
Defender Takeaways
- Avoid exposing ASA web portals, Telnet, or SSH interfaces directly to the Internet.
- Implement patches promptly upon CVE publication—historical abuse timelines are short.
- Enforce multi-factor authentication for all remote access.
- Monitor GreyNoise’s Cisco ASA Scanner tags for real-time scanning indicators: Cisco ASA Scanner, ASA CVE-2020-3259 Information Disclosure, ASA XSS Attempt, and Arbitrary File Retrieval Attempt.
Concentrated reconnaissance bursts like those observed in August should be treated as early warning signals.
Organizations are urged to contact their GreyNoise support team for JA4+ signature details and ongoing updates.
Find this Story Interesting! Follow us on Google News, LinkedIn and X to Get More Instant Updates