Google’s Threat Intelligence Group (GTIG) and Mandiant have issued an urgent warning about a sophisticated cyberattack campaign by the CL0P ransomware group targeting Oracle E-Business Suite (EBS) environments through a zero-day vulnerability.
The attack, which began as early as August 9, 2025, has affected numerous organizations worldwide through the exploitation of CVE-2025-61882, a critical vulnerability that remained unpatched for months.
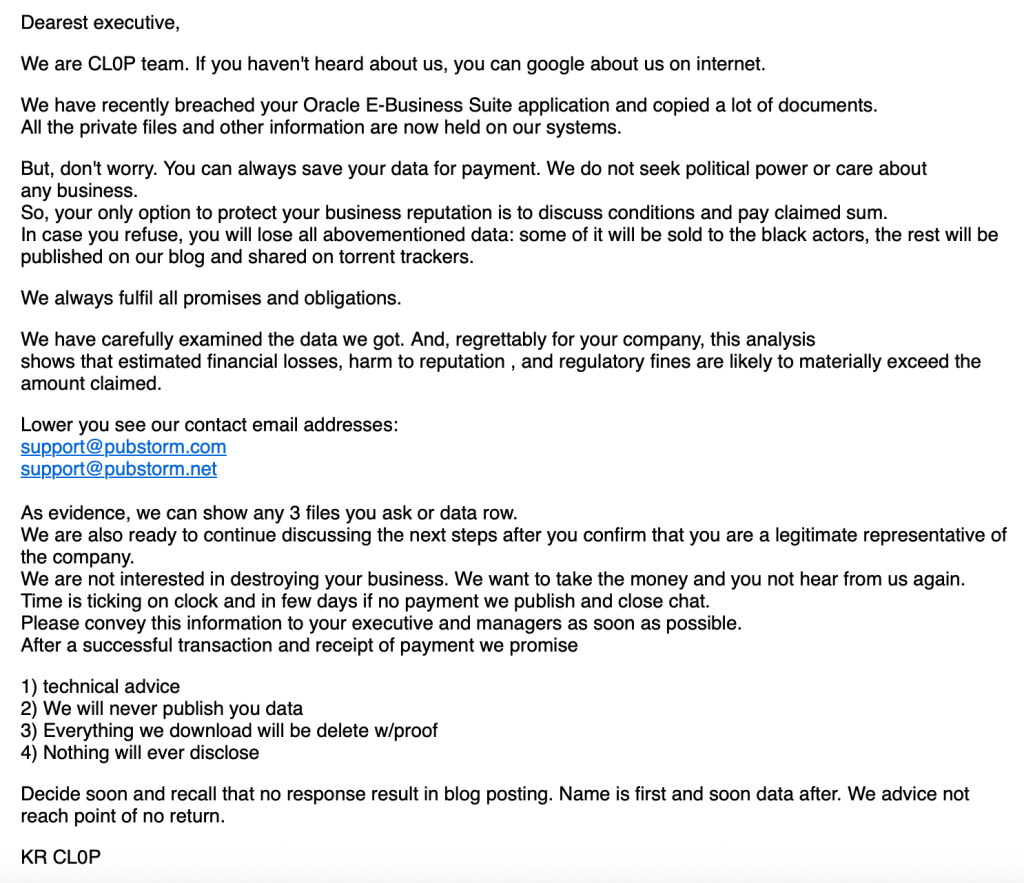
The threat actors launched a large-scale extortion campaign on September 29, 2025, sending thousands of emails to corporate executives claiming to have stolen sensitive data from their Oracle EBS systems.
These emails, sent from compromised third-party accounts likely obtained from infostealer malware logs, contained legitimate file listings from victim environments dating back to mid-August 2025.
The extortion messages included contact addresses [email protected] and [email protected], which have been associated with the CL0P data leak site since May 2025.
Zero-Day Exploitation Campaign Targets Enterprise Systems
Oracle initially reported the vulnerability exploitation on October 2, 2025, and recommended that customers apply the July 2025 critical patch updates.
However, the company was forced to release emergency patches on October 4, 2025, specifically addressing CVE-2025-61882 after discovering the threat actors had been exploiting it as a zero-day vulnerability for weeks.
The vulnerability combines multiple attack vectors, including Server-Side Request Forgery (SSRF), Carriage-Return Line-Feed (CRLF) injection, authentication bypass, and XSL template injection to achieve remote code execution on Oracle EBS servers.
Google’s analysis revealed two distinct exploitation chains targeting different servlet components within the EBS infrastructure.
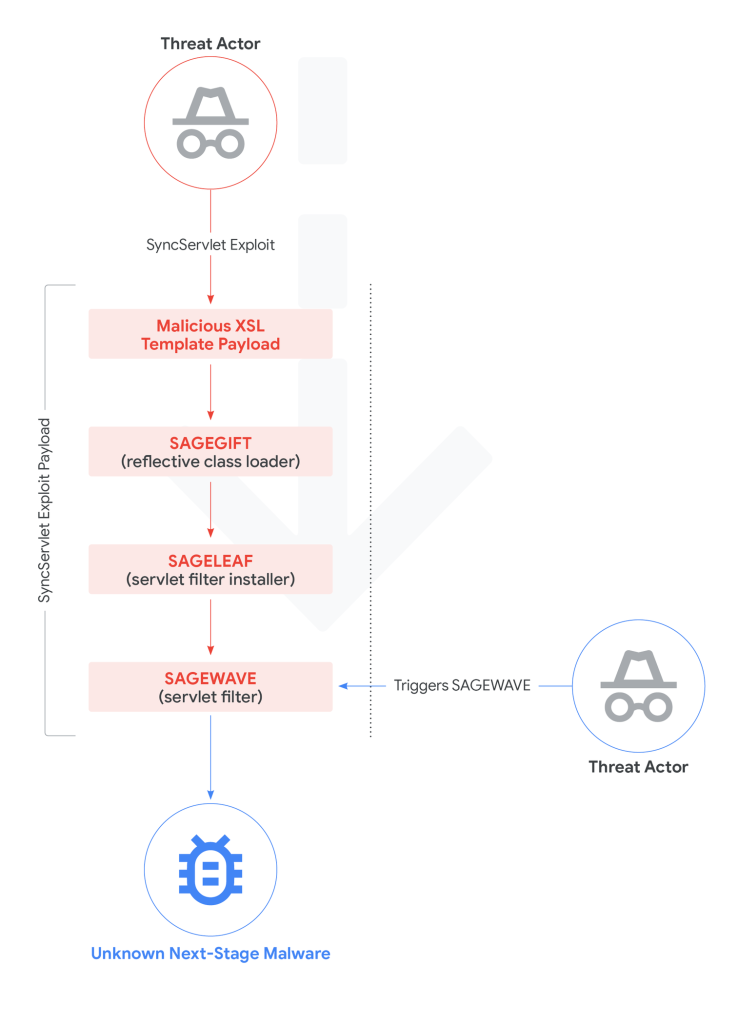
In August 2025, attackers began exploiting the SyncServlet component, initiating attacks with POST requests to /OA_HTML/SyncServlet.
The threat actors used the XDO Template Manager functionality to create malicious templates within the EBS database, then triggered payloads through the Template Preview functionality.
Advanced Java Implant Framework Deployed
These malicious templates, stored in the XDO_TEMPLATES_B database table, consistently used prefixes “TMP” or “DEF” with template types set to XSL-TEXT or XML.
The attackers deployed a sophisticated multi-stage Java implant framework including GOLDVEIN.JAVA, a downloader that communicates with command-and-control servers disguised as TLSv3.1 handshakes.
Additional payloads included the SAGE infection chain, featuring SAGEGIFT (a custom Java reflective class loader), SAGELEAF (an in-memory dropper), and SAGEWAVE (a malicious servlet filter for deploying encrypted ZIP archives containing Java classes).
Following successful exploitation, threat actors conducted reconnaissance using commands such as “cat /etc/fstab,” “df -h,” “ip addr,” and established reverse shells to IP address 200.107.207.26.
The attack pattern mirrors previous CL0P campaigns that exploited zero-day vulnerabilities in managed file transfer systems, suggesting continuity in the group’s operational methods.
Security experts recommend immediately applying Oracle’s October 4 emergency patches, hunting for malicious database templates, restricting outbound internet access from EBS servers, and monitoring for suspicious requests to UiServlet and SyncServlet endpoints.
Organizations should query XDO_TEMPLATES_B and XDO_LOBS database tables to identify templates with suspicious naming conventions, as the threat actors store payloads directly within the EBS database infrastructure.
Indicators of Compromise
The following indicators of compromise are available in a Google Threat Intelligence (GTI) collection for registered users.
| Type | Indicator | Description |
| Network | 200.107.207.26 | IP address observed in exploitation attempts targeting the UiServlet and SyncServlet components. |
| Network | 161.97.99.49 | IP address observed in exploitation attempts targeting the UiServlet component |
| Network | 162.55.17.215:443 | GOLDVEIN.JAVA C2 |
| Network | 104.194.11.200:443 | GOLDVEIN.JAVA C2 |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates