Microsoft Threat Intelligence reports a surge in ClickFix social engineering attacks, with campaigns targeting thousands of enterprise and consumer devices globally every day.
The technique exploits users’ tendency to resolve minor technical issues by tricking them into executing malicious commands disguised as legitimate troubleshooting steps.
Sophisticated Attack Chain Bypasses Security Controls
ClickFix attacks begin with phishing emails, malvertising, or compromised websites that redirect users to convincing landing pages.
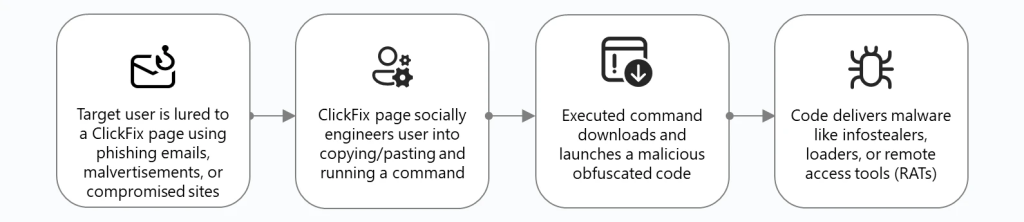
These pages often impersonate trusted services like Cloudflare Turnstile, Google reCAPTCHA, or even Discord servers to establish credibility.
The attack’s effectiveness lies in its human-centric approach. Rather than exploiting software vulnerabilities, threat actors present fake error messages or verification prompts that instruct users to copy malicious commands and paste them into the Windows Run dialog (Win + R), PowerShell, or Terminal.
This user interaction element allows attacks to bypass conventional automated security solutions.
Microsoft has observed threat actors like Storm-1607 and Storm-0426 deploying sophisticated obfuscation techniques, including Base64 encoding, string concatenation, and nested execution chains.
Commands often abuse living-off-the-land binaries (LOLBins) such as powershell.exe, msbuild.exe, and regasm.exe to execute fileless payloads directly in memory.
The technique delivers diverse malware families, including Lumma Stealer infostealer, remote access tools like AsyncRAT and NetSupport, loaders such as Latrodectus, and even modified versions of the r77 rootkit for persistence.
Cross-Platform Expansion to macOS Systems
In a significant evolution, ClickFix campaigns expanded to target macOS users in June 2025, delivering Atomic macOS Stealer (AMOS).
The macOS variant uses sophisticated social engineering, prompting users for system passwords before downloading payloads and bypassing macOS security features using stolen credentials and the xattr -c command.

The malicious macOS command chain includes password validation through dscl . -authonly, payload download via curl, quarantine removal, and execution of the AMOS stealer capable of harvesting browser credentials and cryptocurrency wallet data.
Underground Economy and Protection Strategies
Cybercriminals are commercializing ClickFix through builder kits sold on hacker forums for $200-$1,500 monthly subscriptions. These kits offer customizable landing pages, anti-VM detection, and multi-language support while promising to bypass security solutions.
Microsoft Defender XDR provides comprehensive protection through SmartScreen warnings, AMSI scanning for PowerShell and HTA scripts, and network protection that blocks malicious domains.
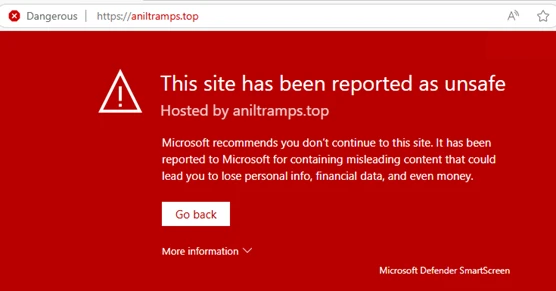
Organizations can enhance defense by monitoring RunMRU registry entries for suspicious LOLBin execution and implementing user education programs focused on recognizing social engineering tactics.
The ClickFix technique represents a concerning shift toward human-targeted attack vectors that exploit trust and technical illiteracy rather than software vulnerabilities, requiring organizations to adapt their security strategies accordingly.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates