Cybersecurity researchers have uncovered a large-scale malware campaign abusing at least 26 code-signing certificates over the past seven years to disguise malicious software as legitimate productivity tools.
The malware, dubbed BaoLoader, has been distributed under the guise of applications such as AppSuite-PDF, PDF Editor, ManualFinder, and OneStart, often marketed as free PDF utilities or browser enhancements.
Abuse of Code-Signing Certificates
Code-signing certificates are meant to authenticate software developers, ensuring that applications come from trusted publishers.
Threat actors behind BaoLoader evade this trust mechanism by registering businesses in jurisdictions such as Panama, Malaysia, and the United States, obtaining fresh certificates from legitimate Certificate Authorities (CAs).
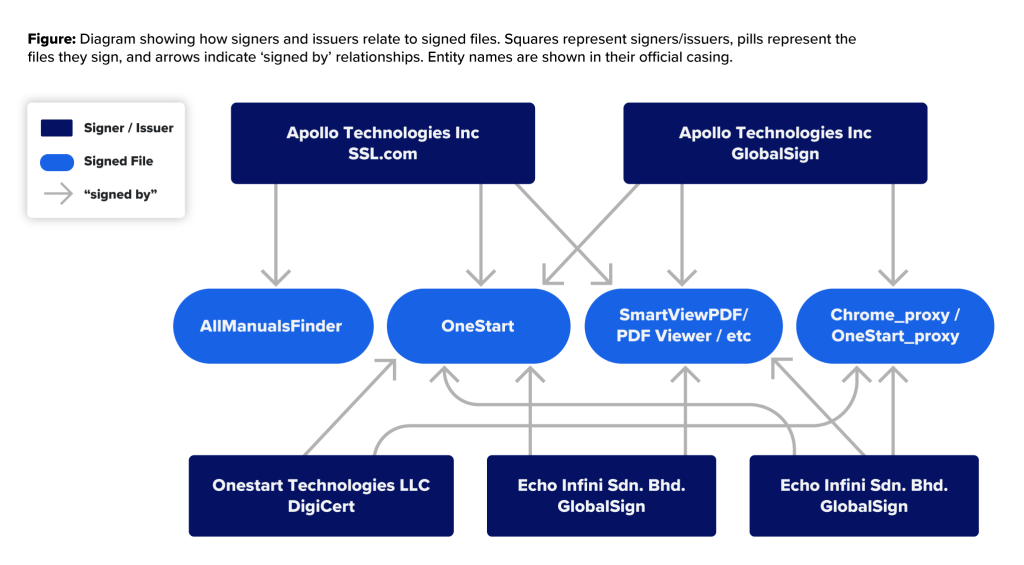
What makes this campaign particularly notable is the consistent reuse of signer names across multiple certificate providers, an unusual pattern in cases of abuse.
In total, the actors cycled through certificates for companies, including Apollo Technologies Inc., Echo Infini Sdn. Bhd., Summit Nexus Holdings LLC, and Glint Software Sdn. Bhd..
Each was used to sign different variants of fake applications, ensuring their software appeared authentic to both end-users and security tools. When one certificate was revoked, the group quickly obtained a new one under another registered entity.
Analysis by CertCentral.org highlights the unusual consistency of issuer-country combinations: 15 certificates from Panama-based firms, five from Malaysia, and a series tied to U.S.-registered shell companies.
Researchers confirm that, unlike typical certificate reselling operations, these actors procure certificates directly, indicating organizational sophistication and long-term planning.
Malicious Payloads Hidden Behind PUPs
At first glance, the distributed applications function as basic PDF editors or file utilities, but their real purpose is far more insidious. Security teams at Expel and G DATA note that installations drop persistent JavaScript loaders executed via node.exe and scheduled tasks.
These loaders reach out to domains such as mka3e8[.]com and other rotating infrastructure to fetch secondary payloads.
While categorized initially as Potentially Unwanted Programs (PUPs), recent incidents prove the malware includes backdoor capabilities, covert communication mechanisms, and in some cases, proxy hijacking features.
Victims’ systems may be silently transformed into residential proxies, leveraged for fraud or further distribution of malicious traffic.
Researchers also stress that BaoLoader is distinct from other malware families such as Chromeloader or TamperedChef, despite frequent mislabeling. The key difference lies in its unique certificate abuse patterns and consistent thematic disguise as PDF utilities.
Why It Matters
This campaign demonstrates how systematic certificate abuse undermines one of the core trust mechanisms of modern computing.
Security researchers warn that the scale of this operation, seven years of sustained malicious distribution using dozens of certificates, suggests a well-organized group that is difficult to disrupt.
Organizations are urged to monitor certificate irregularities, block known malicious domains, and implement controls such as AppLocker or application whitelisting to prevent execution of unauthorized software.
Without stronger scrutiny around code-signing, BaoLoader-like operations could continue to exploit trust mechanics at a global scale.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates