Zscaler ThreatLabz has uncovered a sophisticated new malware loader dubbed CoffeeLoader, which emerged in September 2024.
This advanced threat actor tool is designed to download and execute second-stage payloads while evading detection by endpoint security products.
Advanced Evasion Techniques Deployed
CoffeeLoader employs a range of cutting-edge techniques to bypass security solutions, including a specialized GPU-based packer, call stack spoofing, sleep obfuscation, and the utilization of Windows fibers.
The malware’s initial dropper component performs an installation routine, copying itself to specific system directories and establishing persistence through Windows Task Scheduler.
CoffeeLoader’s main module implements numerous evasion tactics, such as call stack spoofing to mask the origin of function calls and sleep obfuscation to encrypt code and data while dormant.

Similarities with SmokeLoader and Potential Evolution
CoffeeLoader shares several characteristics with the notorious SmokeLoader malware, including stager functionality, bot ID generation methods, and network traffic encryption techniques.
While the exact relationship between the two remains unclear, these similarities suggest a possible evolution or inspiration from SmokeLoader’s codebase.
The malware’s command and control (C2) infrastructure leverages HTTPS communication with certificate pinning to prevent man-in-the-middle attacks.
A domain generation algorithm (DGA) serves as a backup communication channel if primary C2 servers become unreachable.
ThreatLabz researchers have observed CoffeeLoader being used to deploy Rhadamanthys shellcode, indicating its potential as a versatile tool for threat actors.
CoffeeLoader’s advanced features, such as its ability to inject and run shellcode, executables, and DLLs in target processes, make it a formidable threat in the crowded malware loader market.
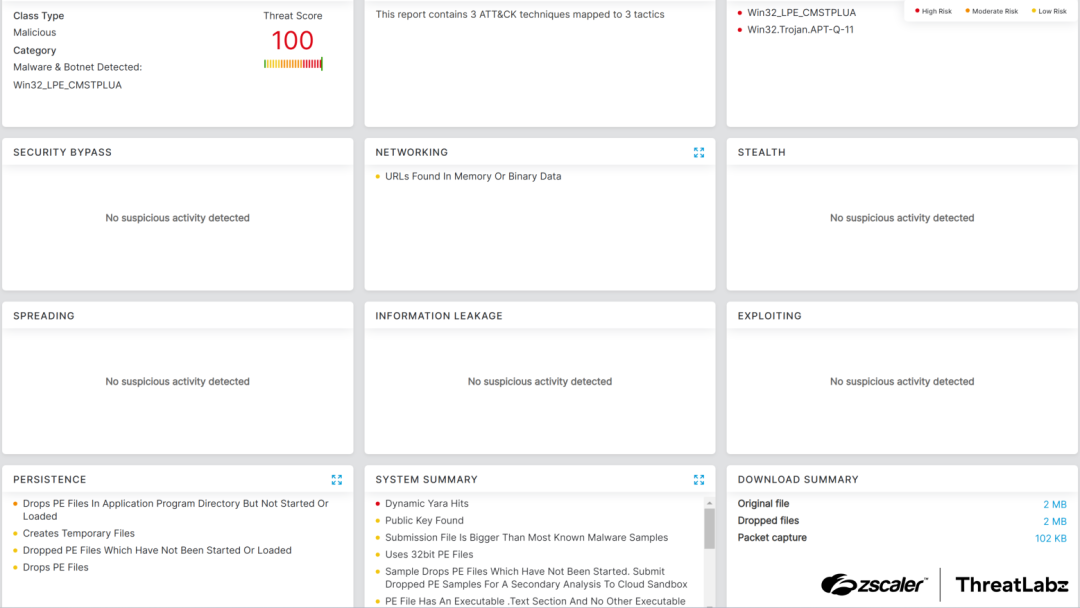
The integration of innovative red team concepts like call stack spoofing and sleep obfuscation demonstrates the malware author’s commitment to evading detection by antivirus software, EDR solutions, and malware sandboxes.
As CoffeeLoader continues to evolve, security teams must remain vigilant and adapt their defenses to counter its sophisticated evasion techniques.
The emergence of this new loader underscores the ongoing arms race between threat actors and cybersecurity professionals in the ever-changing landscape of digital threats1.
Find this Story Interesting! Follow us on LinkedIn, and X to Get More Instant Updates