The construction industry has entered 2025 as an increasingly attractive target for cyber adversaries. Threat actors ranging from ransomware operators and financially motivated criminal groups to state‑sponsored APTs from China, Russia, Iran, and North Korea are exploiting weak digital defenses within the building sector.
Their primary objective is to acquire remote network access credentials, such as VPN, RDP, and Citrix logins, which are then traded across underground forums.
Expanding Attack Surface through Digitalization
A surge in connected construction technology has significantly widened the attack surface. Firms now rely heavily on IoT‑enabled equipment, Building Information Modeling (BIM) platforms, and cloud‑based project management tools. These systems improve collaboration but also introduce exploitable entry points.
Compromised IoT sensors, unpatched smart cranes, and insecure site networks often serve as initial footholds. Attackers then pivot laterally through interconnected systems to harvest sensitive data, including project blueprints, contractor records, and financial details.
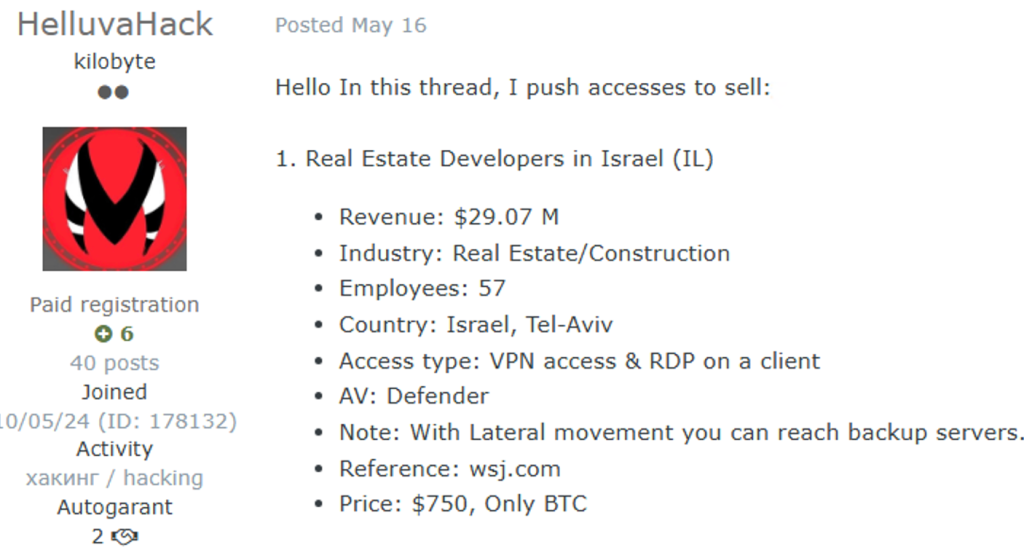
BIM repositories, which centralize design and scheduling information, are particularly high‑value targets; unauthorized logins can expose the entire project architecture. Cybercriminals monetize this access by selling corporate entry points on dark‑web marketplaces.
Listings advertising VPN, RDP, or cPanel credentials for construction companies have become increasingly common, with prices determined by organization size, domain privileges, and network complexity.
Social Engineering and Vendor Compromise
Social engineering remains the most effective infiltration method. Phishing campaigns impersonate executives, project managers, or suppliers to request urgent payments or login verification. Attackers frequently distribute malware‑laden attachments disguised as blueprints or invoices.
In other cases, they weaponize legitimate platforms such as compromised accounts in project management tools to host phishing payloads that evade email filters.
The construction workforce’s distributed nature compounds the threat. Employees operating from multiple job sites often lack real‑time access to security support, making them more susceptible to fraudulent communications and credential theft.
Meanwhile, smaller contractors with minimal cybersecurity budgets serve as weak entry points into larger enterprise ecosystems.
Supply Chain and Third‑Party Exposure
Complex supply chains magnify risk. Dozens of subcontractors and technology vendors exchange data across loosely secured channels, and a single compromised endpoint can cascade through an entire project.
Breaches increasingly stem from compromised updates, weak vendor authentication, or the reuse of stolen credentials across partner systems.
Security experts urge construction firms to implement continuous vendor assessments, enforce multi‑factor authentication for remote access, and segregate IoT devices from corporate networks.
As cyber adversaries refine techniques to monetize access sales and launch ransomware attacks, proactive digital hygiene and cross‑partner threat visibility have become essential for safeguarding project continuity and operational resilience.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates