A novel email campaign attributed to the Lone None threat actor group is leveraging copyright infringement takedown notices to distribute two families of information stealers: Pure Logs Stealer and the newly observed Lone None Stealer (also known as PXA Stealer).
Since November 2024, Cofense Intelligence has tracked multiple iterations of this campaign, which has spoofed legal firms worldwide to trick recipients into executing a malicious payload.
Initially written in at least ten languages using machine translation or AI tools, these lures typically reference authentic Facebook accounts operated by the victims, lending false credibility to the takedown requests.
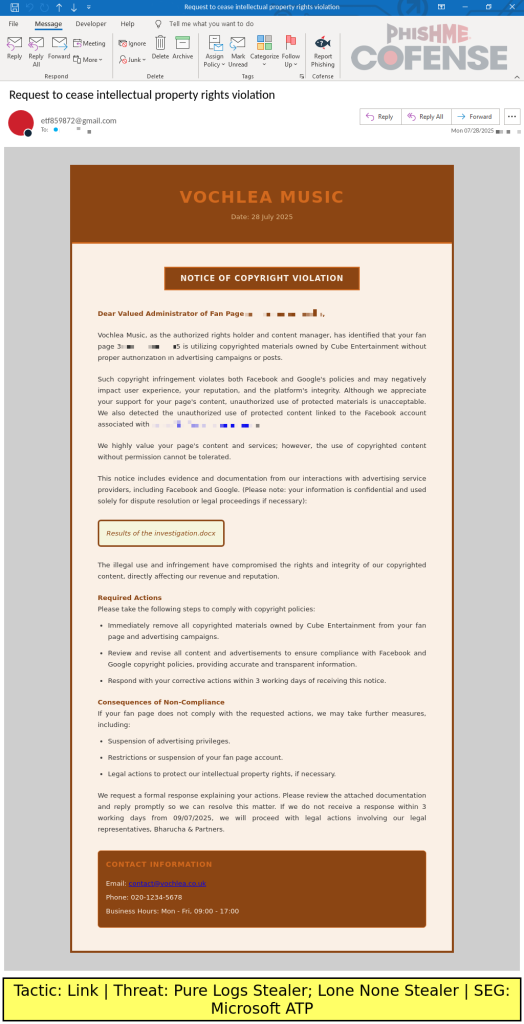
The campaign’s emails contain embedded links that are often shortened via t[.]ee or g[.]su and redirect to free file-hosting services such as Dropbox and MediaFire. Recipients who follow the link download an archive file masquerading as a PDF reader installer.
In reality, the archive bundles a repurposed Haihaisoft PDF Reader executable, a malicious DLL acting as a Python installer, legitimate PDF and Office documents, and files with mismatched extensions.
Emerging Stealer and Evolving Delivery Techniques
Upon execution, the loader uses Windows certutil.exe to decode an archive file disguised as a PDF, saving it under a different extension. A bundled WinRAR executable (renamed “images.png”) then extracts the decoded archive into C:\Users\Public.
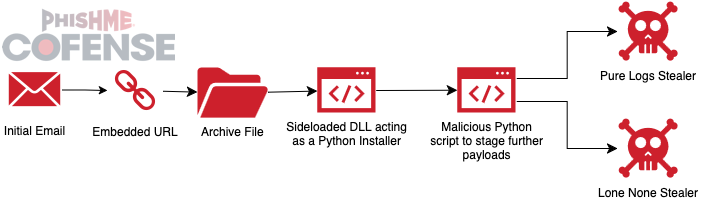
The malicious DLL spawns a staged Python interpreter (named svchost.exe) to install Python into the same directory and execute an obfuscated Python script passed the argument “MRB_NEW_VER_BOT,” which specifies a Telegram bot profile page for command-and-control communication.
This Telegram profile serves as an unconventional C2 channel, storing part of a paste [.]rs URL in its bio. The staged Python script reconstructs the URL (e.g., paste[.]rs/RWqFD) and retrieves a secondary script that contacts 0x0[.]st for final payloads.
Typically, one payload delivers Pure Logs Stealer while the other fetches Lone None Stealer. Both payloads employ multiple layers of text encoding (Base64 or Base85) and AES encryption to evade sandbox detection.
Lone None Stealer specifically targets cryptocurrency by monitoring the Windows clipboard for strings matching cryptocurrency address regular expressions. When a match is found, it silently replaces the address with an actor-controlled wallet and alerts the Telegram bot C2 of the replacement.
Wallet addresses observed include Bitcoin (1DPguuHEophw6rvPZZkjBA3d8Z9ntCqm1L), Ethereum (0xd38c3fc36ee1d0f4c4ddaeebb72e5ce2d5e7646c), and Solana (GQwKEEi49iKywE8ycnFsxRhxJTVf6YsoJb2vAFigc8), among others.
Earlier campaign variants delivered additional RATs and information stealers, such as XWorm and DuckTail. Still, recent samples have streamlined to focus on Pure Logs Stealer’s built-in RAT capabilities and the specialized cryptocurrency theft functionality of Lone None Stealer.
Persistence is achieved through a registry Run key that points to the staged Python interpreter and script.
Defenders should look for a clandestine Python installation under C:\Users\Public\Windows, a startup task in HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run referencing a Python interpreter named svchost.exe, and anomalous executions of certutil.exe and WinRAR with renamed executables.
Ultimately, user awareness remains the most vigorous defense; training to recognize suspicious takedown notices and avoiding unauthorized installations can thwart this sophisticated malware campaign.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates