Russian-linked cybercriminals have introduced an advanced malware loader, dubbed CountLoader, in a series of phishing attacks against Ukrainian targets.
Delivered via a fake Ukrainian police PDF lure, CountLoader is available in three flavors: .NET, PowerShell, and JScript, each exhibiting sophisticated persistence and payload delivery mechanisms.
Silent Push Threat Analysts attribute deployment of Cobalt Strike and AdaptixC2 beacon payloads to LockBit, BlackBasta, and Qilin affiliates, underscoring CountLoader’s integration into modern ransomware toolkits.

Weaponized PDF Lure and Initial Deployment
The latest campaign employed a ZIP archive vymoha_na_yavku.zip containing a PDF purportedly issued by Ukraine’s National Police.
When users open the document, an embedded script invokes mshta.exe to fetch the JScript-based CountLoader from a cluster of domains, including ms-team-ping[.]com
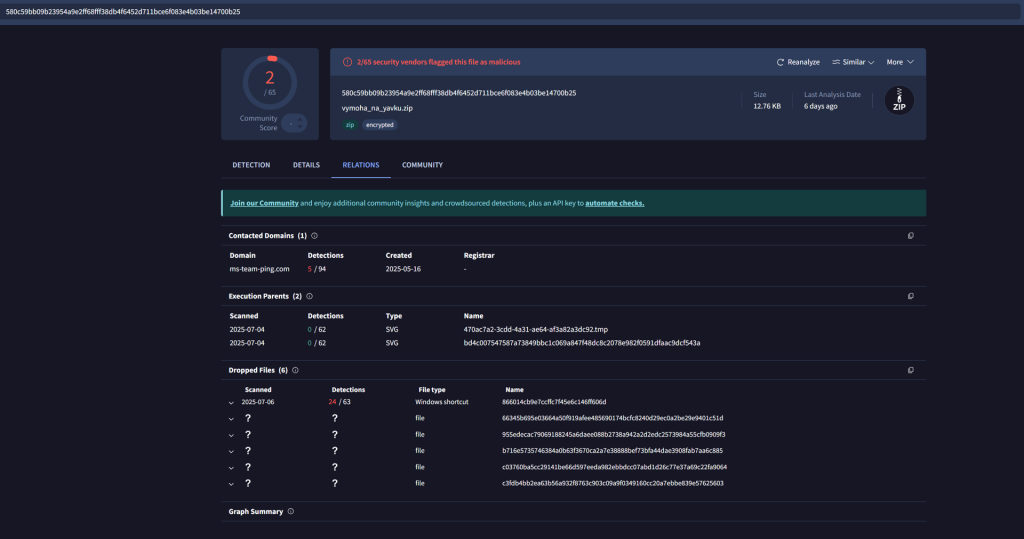
CountLoader’s robust fingerprinting combines proprietary HHV and SSL.CHV hashes with JARM TLS indicators enable it to evade traditional detection by retrying connections to a rotating list of up to ten C2 domains until successful authentication via an XOR-encrypted, Base64-encoded “success” message.
Upon initial execution, CountLoader collects system and domain metadata, generating a GUID-style victim identifier from user names, processor IDs, and disk serial numbers.
It then schedules a persistent task named “GoogleUpdaterTaskSystem135.0.7023.0<vFlawedGUID>,” impersonating Chrome’s update service to launch mshta with a /start parameter after ten minutes.
Registry modifications to MaxScriptStatements and a Run key entry (OneDriver) ensure repeated C2 polling and stage downloads from the victim’s Music folder.
Modular Payload Delivery and Ransomware Linkages
CountLoader’s loader loop authenticates to /connect and retrieves a C2 password, then posts periodic getUpdates requests. Returned tasks specify an ID, URL, and taskType, dictating execution via WMI, RunDLL32, msiexec, or direct process creation.
Notably, domain-joined machines also receive a taskType 5 query to enumerate domain groups, reflecting an emphasis on enterprise compromise.
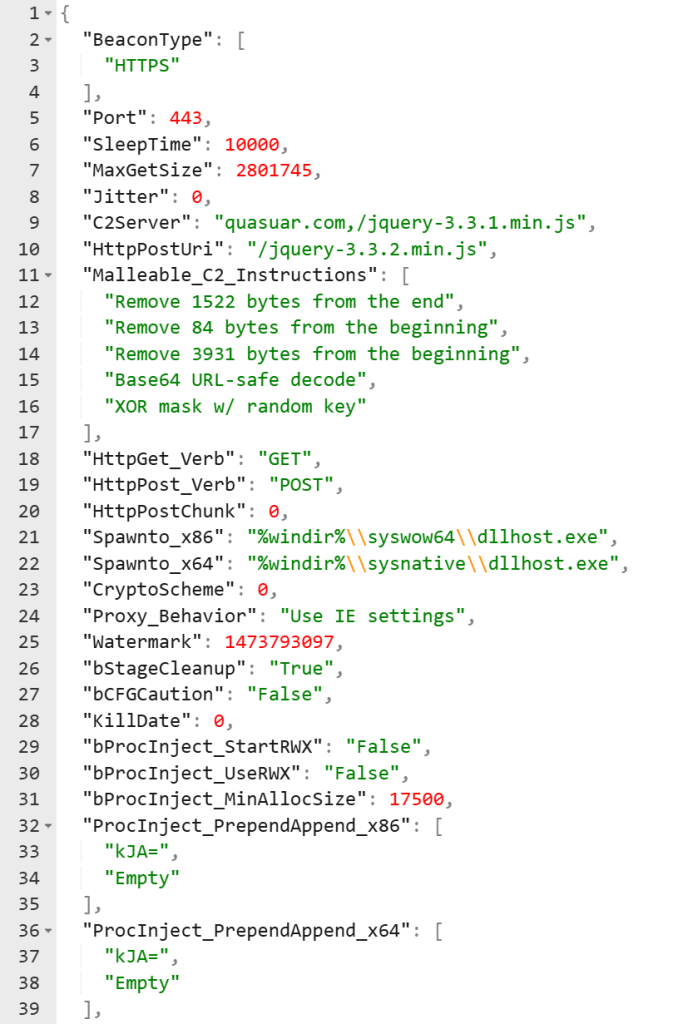
Analysis of two Cobalt Strike beacon payloads yielded watermark 1473793097, linked to both Qilin and BlackBasta incidents. One sample, observed June 20, 2025, communicated with quasuar[.]com (45.61.150.76), while another, dated August 29, 2024, used CloudFront fronting.
Shared SSL fingerprints between these and misctoolsupdate[.]com (180.131.145.73) further corroborate a unified infrastructure. AdaptixC2 implants (SHA-256 EA4108… and B86ADC…) were also deployed, alongside PureHVNC and Lumma Stealer binaries on non-domain hosts.
A .NET variant (twitter1.exe, SHA-256 17bfe3…) mirrors JScript logic but supports only ZIP and EXE tasks, and features a May 12, 2025, kill-switch that crashes the binary post-expiry.
PowerShell CountLoader (20 lines) replicates core C2 loops and in-memory execution, as previously documented by Kaspersky.
Organizations facing Russian threat actors and ransomware affiliates should incorporate Silent Push’s Indicators Of Future Attack (IOFA) feeds for CountLoader into their security stacks and audit scheduled tasks, run keys, and unusual HTA executions to detect and disrupt this evolving loader framework.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates