A critical security vulnerability has been disclosed in AWS Amplify Studio’s UI generation framework, with researchers releasing a proof-of-concept exploit demonstrating remote code execution capabilities.
The vulnerability, tracked as CVE-2025-4318, affects the package and has been assigned a CVSS score of 9.5, marking it as a critical-severity issue that could compromise entire development environments and CI/CD pipelines.
The vulnerability affects versions 2.20.2 and earlier of the @aws-amplify/codegen-ui package, a core component of AWS Amplify Studio’s visual UI development platform.
The vulnerability stems from improper input sanitization of JavaScript property expressions during the build and render process, allowing attackers to execute arbitrary code on systems processing malicious component definitions.
AWS Amplify Studio enables developers to visually create React components through a drag-and-drop interface, with dynamic expressions often used in component properties such as labels, placeholders, and values.
The vulnerability exploits this functionality by injecting malicious JavaScript code into component JSON files, which are then executed without proper validation or sandboxing.
The attack vector requires minimal user interaction, typically occurring when a developer loads a compromised component or when automated build systems process tainted configuration files.
This makes the vulnerability particularly dangerous in collaborative development environments where component schemas might be shared between team members or sourced from external repositories.
AWS Amplify Studio Vulnerability
Security researchers have identified the root cause as the unsafe use of JavaScript evaluation functions including eval(), new Function(), and vm.runInNewContext() on user-controllable input.
The vulnerable code treated component property expressions as trusted JavaScript, executing them directly within the Node.js runtime context without any security constraints.
A proof-of-concept exploit has been developed that demonstrates how attackers can craft malicious component JSON files containing JavaScript expressions designed to execute arbitrary shell commands.
The exploit leverages Node.js’s child_process.execSync function to execute system commands, potentially allowing attackers to access sensitive information, modify files, or establish persistent access to compromised systems.
The vulnerability is particularly concerning in CI/CD environments where it could lead to exposure of AWS tokens, environment secrets, and other sensitive credentials.
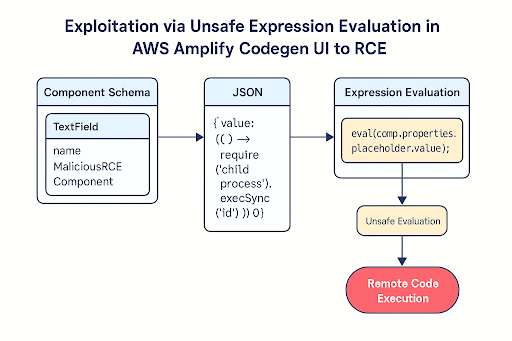
The exploit breaks fundamental security boundaries in web-based low-code platforms by enabling users to execute system-level commands on server infrastructure.
Enhanced Security Controls
AWS has responded to the disclosure by releasing version 2.20.3 of the @aws-amplify/codegen-ui package, which implements comprehensive security fixes to eliminate the unsafe evaluation practices.
The patch introduces a new sandbox layer that replaces direct eval() calls with a safer evaluation mechanism using the Function() constructor within a restricted execution context.
The security improvements include implementation of a keyword blacklist that blocks dangerous JavaScript functions and Node.js core modules such as require, process, and child_process.
Additionally, the patch enforces strict input validation and fails fast when suspicious expressions are detected.
AWS security teams have advised developers to immediately upgrade to version 2.20.3 or later and audit all existing component schemas for potentially unsafe expressions.
The incident highlights the critical importance of implementing secure coding practices in low-code development platforms where user input directly influences code generation and execution processes.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates