Qilin ransomware group maintained its position as the most active operator for the fourth consecutive month, claiming responsibility for 104 victim organizations in August 2025, according to Cyble’s global threat landscape report.
This total nearly doubles that of second-place Akira, which targeted 56 organizations during the same period, and underscores a fourth straight monthly increase in ransomware incidents, with 467 recorded globally.
Qilin’s Enduring Dominance and Sector Targets
Since April, Qilin has claimed 398 victims, 18.4 percent of the 2,164 total ransomware attacks recorded, outpacing Akira by more than 70 percent.
Qilin’s continued success is attributed to its robust affiliate incentives, streamlined ransomware-as-a-service operations, and specialized payload featuring fileless execution leveraging PowerShell and living-off-the-land binaries for evasion.
The group’s campaigns have spanned critical infrastructure, manufacturing, and healthcare, exploiting remote desktop protocol (RDP) and weak VPN credentials to gain initial access.
Sinobi’s Meteoric Rise and Technical Profile
Emerging only two months ago, Sinobi surged to third place with 41 claimed victims. Technical analysis reveals shared code constructs in its custom ransomware loader and similarities in its Tor-based data leak site to Lynx, though both groups appear operationally distinct.
Sinobi’s encryption module employs ChaCha20 for symmetric file encryption alongside RSA-4096 for key wrapping.
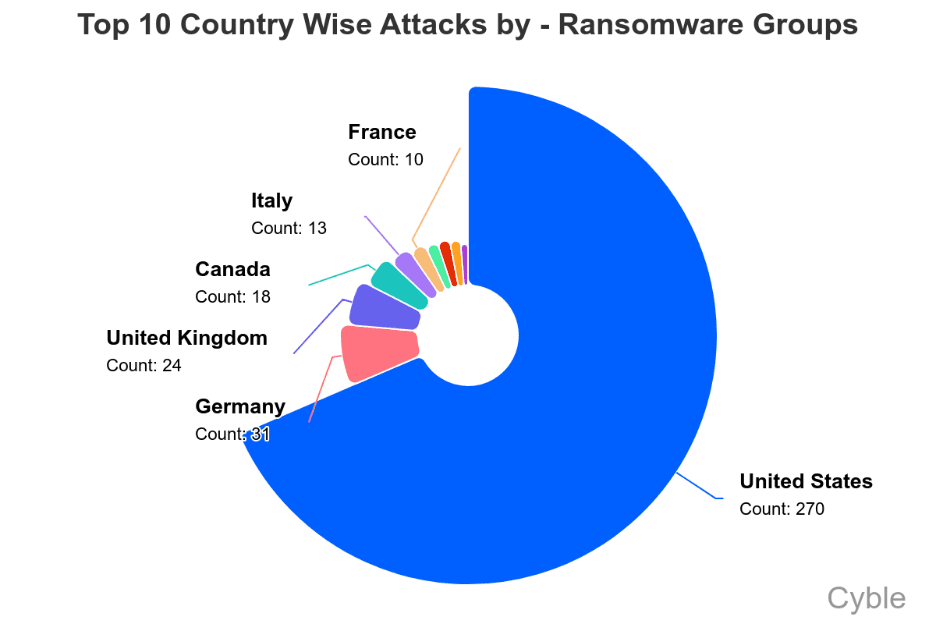
The group’s affiliates have predominantly targeted U.S. organizations 39 of 41 victims across more than ten sectors, including a major U.S. financial institution, indicating a high-scale campaign infrastructure likely supported by automated scanning tools and affiliate portals.
Notably, Sinobi’s activity has waned since August 24, suggesting possible saturation of accessible targets or internal regrouping.
Emerging Threat Actors and Regional Dynamics
Beyond Qilin and Akira, new actors such as The Gentlemen have claimed over 30 victims in September, leveraging a Go-based loader that evades static detection.
Meanwhile, LockBit seeks resurgence with its 5.0 release featuring enhanced anti-analysis measures and multi-threaded encryption. Geographically, the U.S. remains the top target, while Germany and the U.K. have displaced Canada in victim counts.
Sector analysis shows construction, professional services, manufacturing, and healthcare as predominant targets, with IT, automotive, and finance also heavily affected.
In APAC, BlackNevas and Dire Wolf pose significant risks, particularly in South Korea and Japan. In the META regions, INC Ransom complements Qilin’s dominance.
Security teams are urged to adopt zero-trust segmentation, enforce multifactor authentication, deploy behavioral endpoint detection, and maintain immutable, air-gapped backups. Proactive threat hunting and dark web monitoring for leaked credentials can provide early warnings.
At the same time, a well-rehearsed incident response plan remains critical to containing and recovering from sophisticated ransomware extortion campaigns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates