Cybersecurity researchers at Palo Alto Networks’ Unit 42 have uncovered a cluster of malware samples employing advanced obfuscation techniques to evade detection and analysis.
The malware, which includes variants of Agent Tesla, XWorm, and FormBook/XLoader, utilizes a multi-stage approach incorporating AES encryption, code virtualization, and dynamic code loading to conceal its malicious payloads.
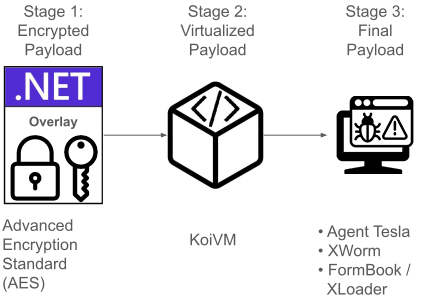
Multi-Stage Payload Delivery and Encryption
The observed malware samples employ a sophisticated three-stage payload delivery system.
In the first stage, the initial payload is encrypted using AES in CBC mode and stored within the PE overlay of the file.
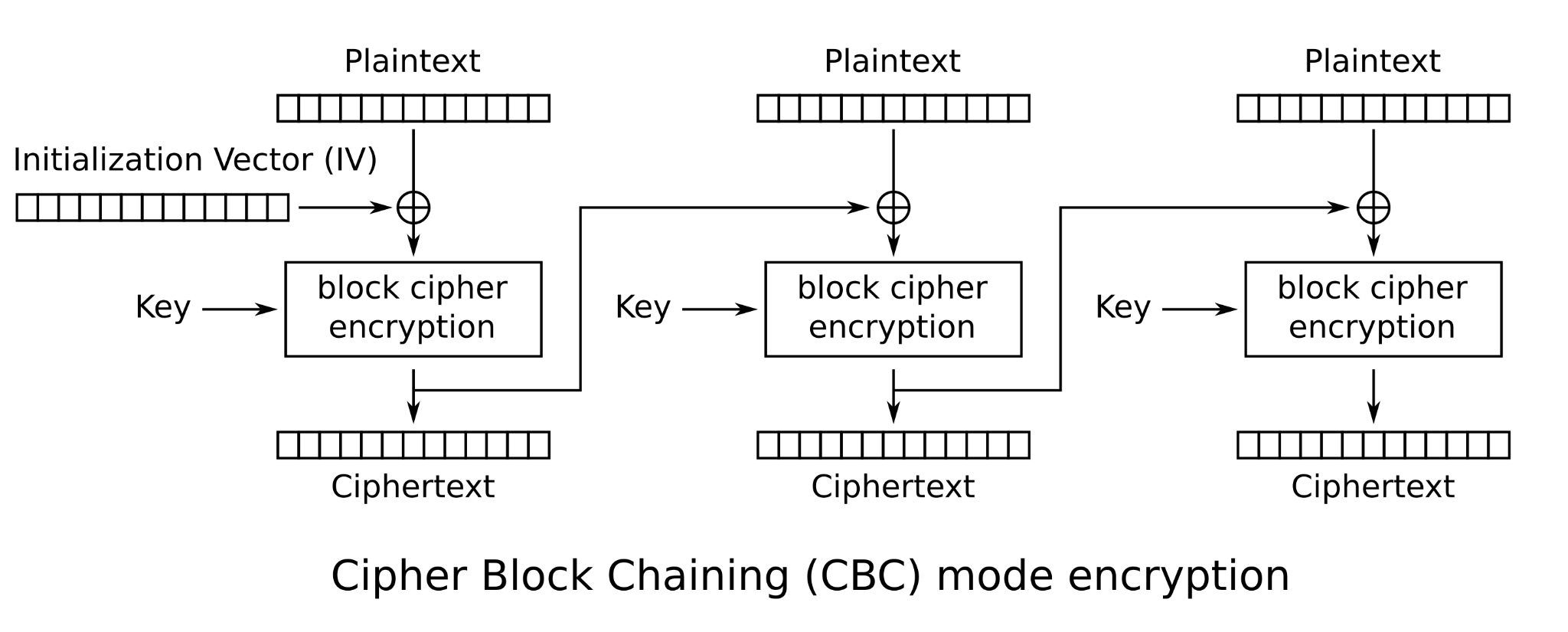
This encrypted payload contains not only the second-stage code but also strings indicative of AMSI bypass capabilities and reflection-based execution.
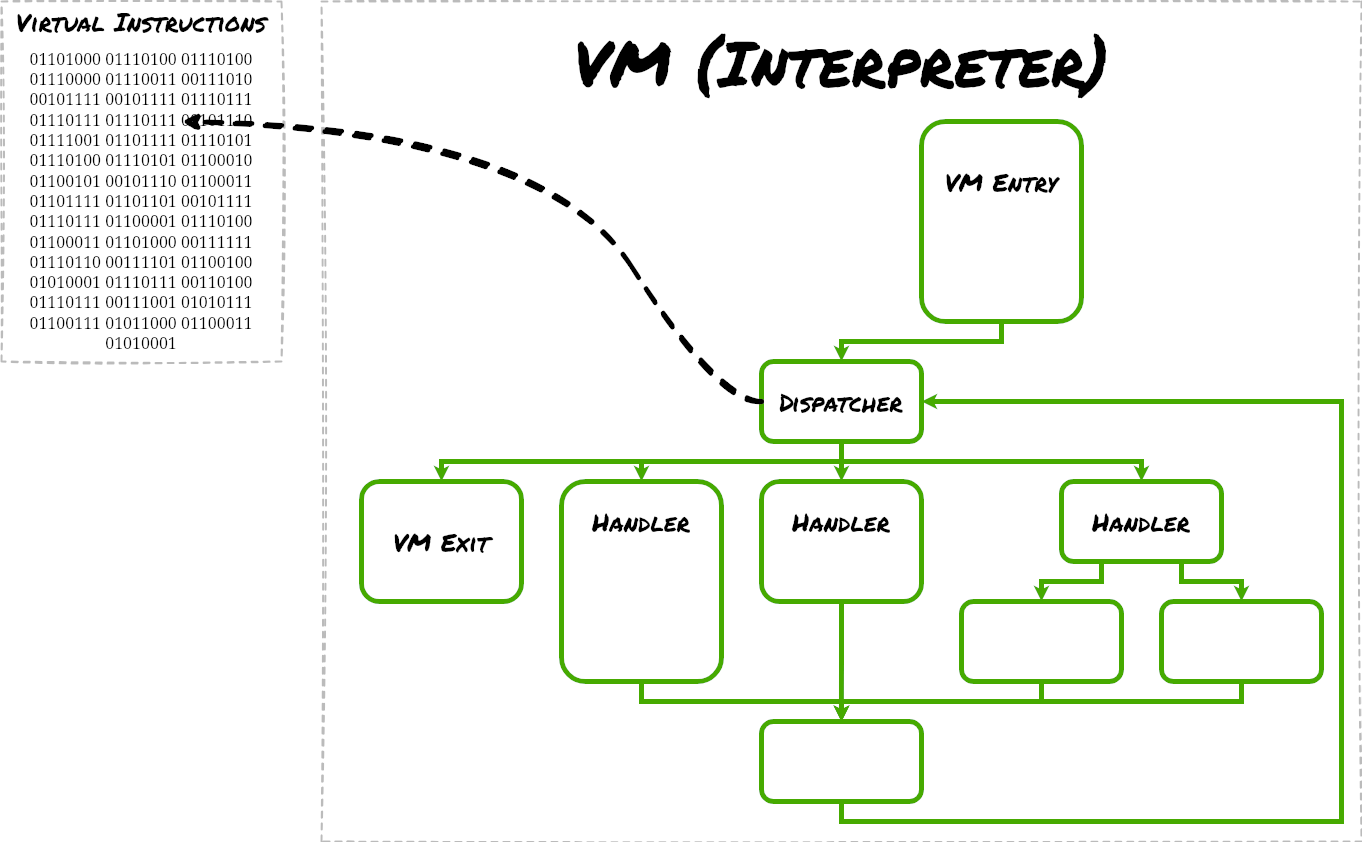
The second stage introduces a more complex obfuscation layer using VM-based protection, specifically KoiVM, a plugin for the ConfuserEx obfuscation tool.
This virtualized payload acts as a dropper, responsible for decrypting and executing the final payload in memory.
The decryption key is encoded in Base64, while the ciphertext exists as an embedded resource.
The final stage payload, typically belonging to the Agent Tesla or XWorm family, is decrypted and executed in memory.
In the case of XWorm samples, even the configuration parameters are further encrypted using AES in ECB mode, with the decryption key stored in a variable named Mutex.
Implications for Cybersecurity
According to Unit 42 researchers, this advanced obfuscation approach presents significant challenges for static analysis and traditional sandbox detection methods.
By combining strong encryption, code virtualization, and fileless execution techniques, threat actors can more effectively distribute malware at scale while evading security mechanisms.
The use of AES encryption, in particular, represents an upgrade from previous variants that relied on simpler XOR encryption.
This shift towards more robust cryptographic protection highlights the ongoing arms race between malware authors and security researchers.
Palo Alto Networks has updated its security products, including Advanced WildFire, Advanced URL Filtering, and Cortex XDR, to better detect and mitigate these threats.
However, the researchers emphasize the need for continued efforts in developing principled approaches to defeat code virtualization protection schemes.
As malware authors continue to refine their obfuscation techniques, the cybersecurity community must remain vigilant and adaptive.
The multi-layered approach observed in these samples underscores the importance of comprehensive security solutions that can address threats at various stages of the attack chain, from initial delivery to final payload execution.