A sophisticated cyberattack targeting a Brazilian enterprise has exposed a troubling escalation in the arms race between cybercriminals and defenders: attackers are now leveraging legitimate, digitally signed drivers to disable antivirus solutions and launch destructive ransomware.
In this latest incident, adversaries employed a Bring Your Own Vulnerable Driver (BYOVD) attack, abusing the ThrottleStop.sys driver designed initially for CPU performance tweaking to bypass system security and deliver the notorious MedusaLocker ransomware.
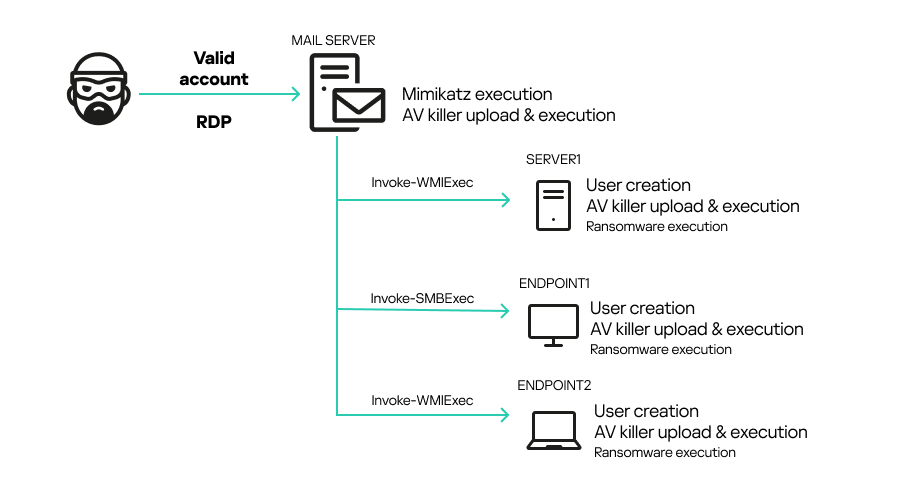
The attackers’ approach exemplifies advanced tactics. They first compromised an SMTP server using valid RDP credentials, extracted further user credentials with Mimikatz, and moved laterally across the network using pass-the-hash methods.
Their primary goal was clear: suppress all security tooling that might obstruct their operation.
Various artifacts, including the AV killer (“All.exe”) and the compromised driver (“ThrottleBlood.sys”, a renamed ThrottleStop.sys), were uploaded and executed, first killing standard antivirus processes, then facilitating the deployment of ransomware.
Technical Analysis: Exploiting Kernel Mode with Trusted Drivers
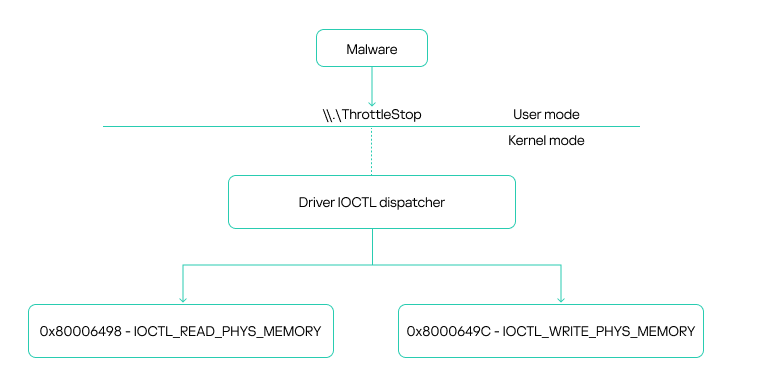
ThrottleStop.sys, meant for legitimate system monitoring, has a critical vulnerability (CVE-2025-7771) allowing any administrator to read and write physical memory via custom IOCTL calls.
Once the attackers installed the driver, their AV killer program connected to this interface and gained the power to modify kernel-mode operations from user mode.
The malware enumerated running processes, compared them with a hardcoded list including all major AV vendors (Microsoft Defender, Kaspersky, Symantec, CrowdStrike, and more), and forcibly terminated each security process in turn using kernel-level commands.
Windows’ built-in self-restoring features, such as those in Defender, proved futile, as the malware looped to kill any revived process instantly.
At the heart of the exploit is a precise abuse of memory: the attackers used the driver’s primitives to locate and hijack kernel functions, injecting code to invoke process-killing routines.
By utilizing undocumented Windows functions like NtQuerySystemInformation, the malware mapped out all loaded modules, determining how to interact with the core kernel code directly.
Recommendations and Lessons Learned
This attack highlights the insufficiency of standalone AV tools and reinforces the need for defense in depth.
Security experts recommend implementing multi-factor authentication, hardening RDP access, segmenting networks, aggressively managing privileges, and deploying solutions with strong self-defense mechanisms capabilities that modern security suites, including Kaspersky’s, have adopted to counter such threats.
As BYOVD attacks become increasingly common, organizations must adapt their strategies to monitor the installation of vulnerable drivers and ensure comprehensive incident detection and response mechanisms are in place.
This latest incident serves as a stark warning: trusted components can become powerful attack tools in the wrong hands.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates