Cybersecurity researchers at Proofpoint have uncovered a sophisticated campaign where threat actors create fake Microsoft OAuth applications to steal user credentials and bypass multifactor authentication (MFA) protections.
The attacks, which began in early 2025, impersonate trusted enterprise applications including RingCentral, SharePoint, Adobe, and DocuSign to lure victims into credential phishing schemes.
Advanced Phishing Techniques Circumvent Security Measures
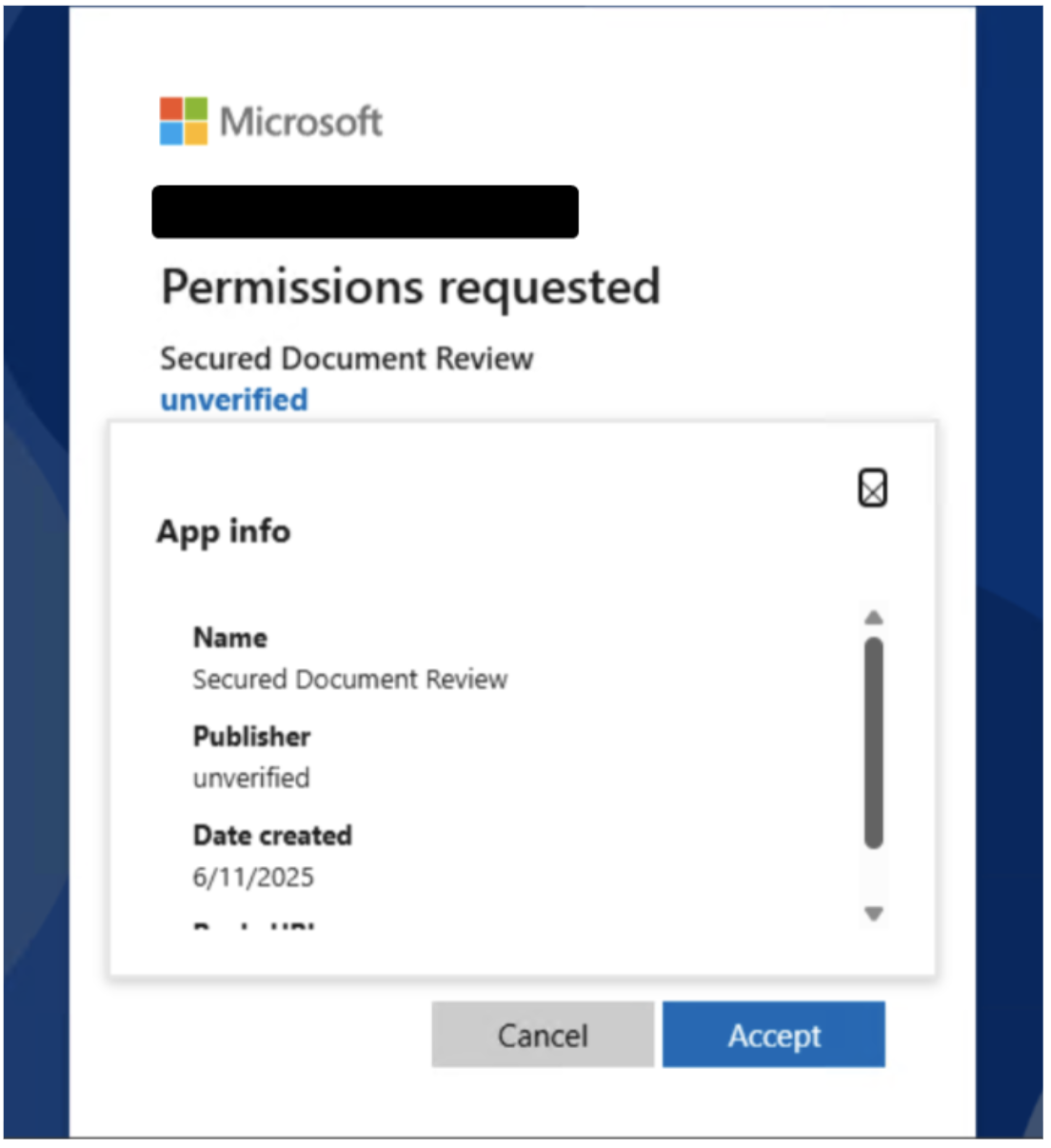
The attack chain leverages Microsoft OAuth application creation combined with attacker-in-the-middle (AiTM) phishing techniques, primarily using the Tycoon phishing-as-a-service platform.
When targets interact with the malicious OAuth applications, whether they accept or cancel the permission request, they are redirected to fraudulent Microsoft authentication pages that harvest both primary credentials and session tokens in real-time.
In one notable campaign targeting the aviation industry, attackers impersonated ILSMart, an inventory locating service for aerospace and defense companies.
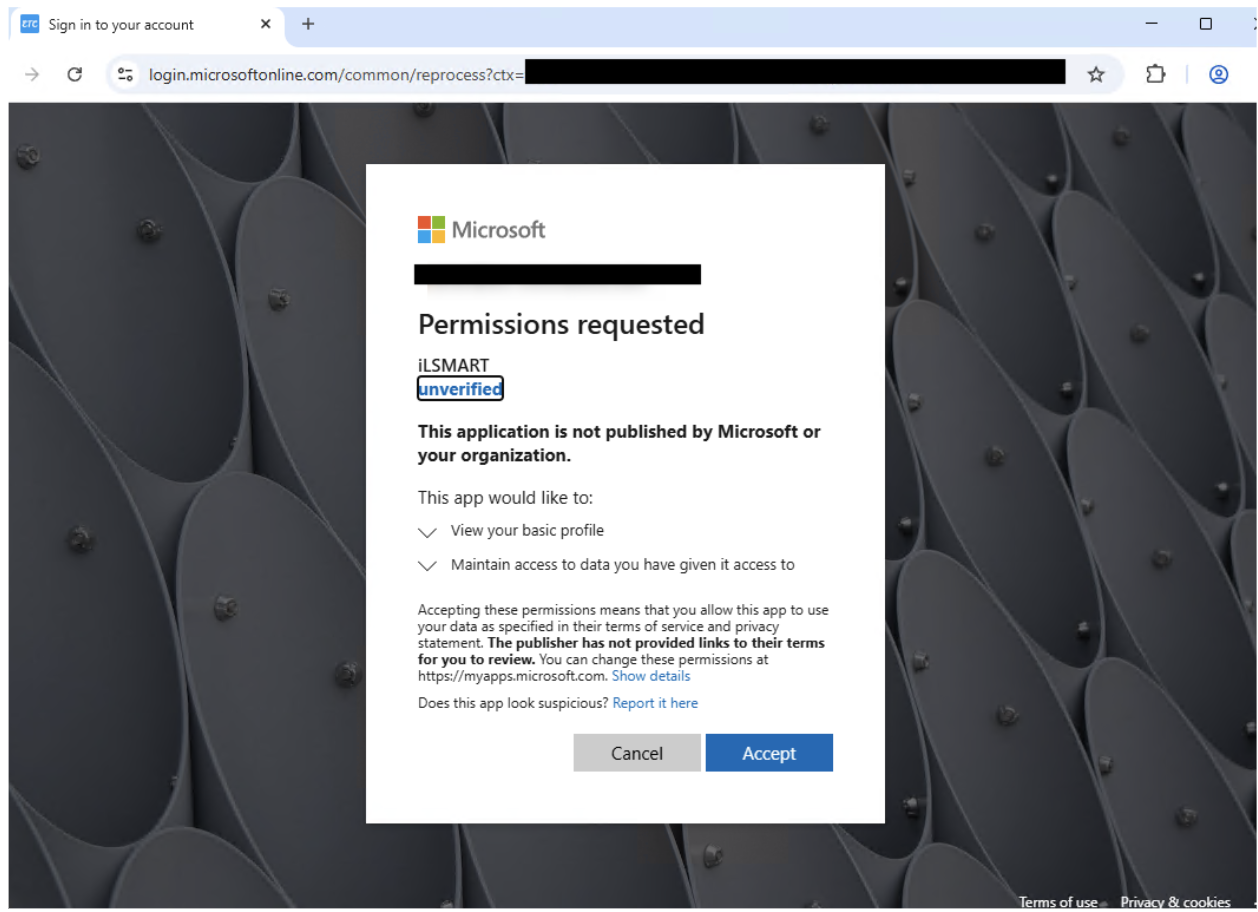
The fake application requested minimal permissions, including “View your basic profile” and “Maintain access to data you have given it access to,” which appear benign but serve as gateways to more sophisticated attacks.
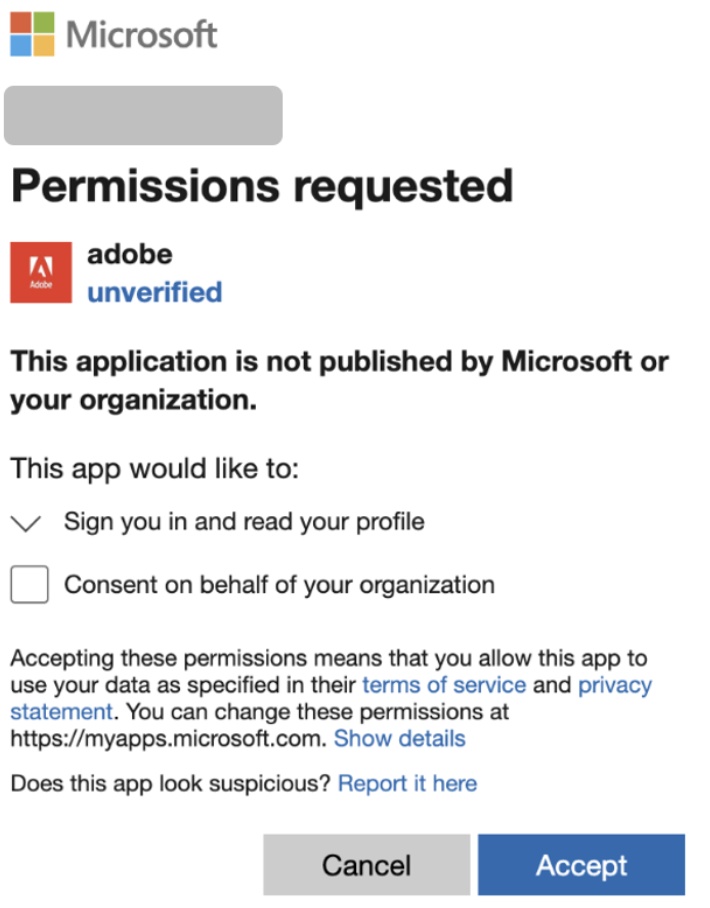
Similarly, a June 2025 campaign impersonating Adobe used SendGrid to distribute phishing URLs that redirected to malicious OAuth “Redirector Apps” on Microsoft Azure.
Widespread Impact Across Multiple Sectors
Proofpoint’s analysis reveals the campaign’s significant scope, with researchers identifying over 50 impersonated applications across multiple email campaigns impacting hundreds of customers.
The attacks have affected nearly 3,000 user accounts across more than 900 Microsoft 365 environments, with a confirmed success rate exceeding 50%.
In cloud tenant infrastructure alone, researchers found more than two dozen malicious applications with consistent patterns in their reply URLs and OAuth scope requests.
The attackers demonstrate tactical adaptability, with some campaigns customized to specific industries based on compromised sender accounts.
Evidence from actual account takeover cases shows attackers using the distinctive user agent string “axios/1.7.9” associated with the Tycoon phishing kit.
Following successful compromises, threat actors typically perform “Security Method Add” actions, indicating attempts to establish persistence within compromised accounts.
Microsoft Implements Defensive Countermeasures
In response to these evolving threats, Microsoft announced in June 2025 that it will update default settings by “blocking legacy authentication protocols and requiring admin consent for third-party app access,” with changes starting mid-July and completing by August 2025.
This update is expected to hamper threat actors utilizing these OAuth application techniques significantly.
Security experts recommend implementing comprehensive email security solutions, cloud security monitoring for account takeovers, web security isolation, security awareness training, and considering FIDO-based physical security keys to defend against these sophisticated hybrid email and cloud threats.
Indicators of Compromises (IoCs):
| Indicator | Description |
|---|---|
| hxxps[:]//azureapplicationregistration[.]pages[.]dev/redirectapp | Redirector to Tycoon |
| hxxps://9b031a44-7158758d[.]yrqwvevbjcfv[.]es/SZgm3kXA/ | Tycoon Landing |
| yrqwvevbjcfv[.]es | Tycoon Landing Domain |
| hxxps://n3xxk[.]gmlygt[.]ru/chai!0jwio | Tycoon Antibot (Example) |
| gmlygt[.]ru | Tycoon Antibot (Example) |
| 2a00:b703:fff2:35::1 | Example of Signin Facing IP for Tycoon |
| hxxps://chikeukohandco[.]com/csi/index.html?redirect_mongo_id=684aaffb62194c1eaec5076d&utm_source=Springbot&utm_medium=Email&utm_campaign=684aaffb62194c1eaec5076e | SendGrid URL to Tycoon Redirector |
| hxxps://chikeukohandco[.]com/saas/Index.html | Redirector to Tycoon |
| pw5[.]haykovx[.]es | Tycoon Landing Domain |
| 14b2864e-3cff-4d33-b5cd-7f14ca272ea4 | Malicious Microsoft OAuth Application ID |
| 85da47ec-2977-40ab-af03-f3d45aaab169 | Malicious Microsoft OAuth Application ID |
| 355d1228-1537-4e90-80a6-dae111bb4d70 | Malicious Microsoft OAuth Application ID |
| 6628b5b8-55af-42b4-9797-5cd5c148313c | Malicious Microsoft OAuth Application ID |
| b0d8ea55-bc29-436c-9f8b-f8829030261d | Malicious Microsoft OAuth Application ID |
| 22c606e8-7d68-4a09-89d9-c3c563a453a0 | Malicious Microsoft OAuth Application ID |
| 31c6b531-dd95-4361-93df-f5a9c906da39 | Malicious Microsoft OAuth Application ID |
| 055399fa-29b9-46ab-994d-4ae06f40bada | Malicious Microsoft OAuth Application ID |
| 6a77659d-dd6f-4c73-a555-aed25926a05f | Malicious Microsoft OAuth Application ID |
| 21f81c9e-475d-4c26-9308-1de74a286f73 | Malicious Microsoft OAuth Application ID |
| 987c259f-da29-4575-8072-96c610204830 | Malicious Microsoft OAuth Application ID |
| db2eb385-c02f-44fc-b204-ade7d9f418b1 | Malicious Microsoft OAuth Application ID |
| f99a0806-7650-4d78-acef-71e445dfc844 | Malicious Microsoft OAuth Application ID |
| fdcf7337-92bf-4c70-9888-ea234b6ffb0d | Malicious Microsoft OAuth Application ID |
| fe0e32ca-d09e-4f80-af3c-5b086d4b8e66 | Malicious Microsoft OAuth Application ID |
| axios/1.7.9 | Axios user agent associated with Tycoon activity |
| axios/1.8.2 | Axios user agent associated with Tycoon activity |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates