In a groundbreaking study conducted by Radware’s research team in 2024, the deep web revealed an alarming rise in cybercrime sophistication, particularly targeting the financial services industry.
Analyzing 46 deep-web hacker forums and over 26,000 threads discussing cybercriminal strategies, the research provided critical insights into emerging threats, including novel malware ecosystems, subscription-based services for stolen credentials, automation of social engineering attacks, and advanced Distributed Denial-of-Service (DDoS) techniques.
Radware’s investigation highlights the development of an underground marketplace revolving around information-stealing malware, known as “infostealers.”
The study uncovered 3-4 unique mentions of “infostealer-as-a-service” daily per forum, illustrating the popularity of modular malware offerings.
Approximately 56% of discussions focused on these customizable services that enable hackers to purchase tailored solutions, compatible with existing toolsets.
The remaining 44% centered on freely shared, breached credentials aiming to bolster sellers’ reputations.
One notable shift within the infostealer economy is the segmentation of services catering to individual actors and Advanced Persistent Threat (APT) groups.
For individual operators, developers offer low-cost subscriptions, user-friendly interfaces, and technical support.
Meanwhile, APT-focused malware, such as Mystic Stealer, is configured to target corporate applications like Microsoft Outlook a platform crucial in organizational communications.
Cybercriminals leveraging Mystic Stealer facilitate initial access to sensitive systems, paving the way for ransomware attacks.

Credential-as-a-Service Platforms: A Subscribable Threat
Another emerging risk is the proliferation of “credential-as-a-service” clouds, subscription-based systems that supply users with freshly breached credentials organized by industry and location.
A prime example, Combo Cloud, experienced a 46% surge in mentions between 2022 and 2024, suggesting a growing reliance on credentials distributed in sophisticated formats rather than basic text files.
These platforms represent an increasingly automated process that reduces the barrier to entry for cybercriminals while raising the stakes for targeted organizations.
OTP Bot Attacks Transforming Social Engineering
The rise of One-Time Password (OTP) bots marks a significant evolution in cybercriminal strategies.
These bots, primarily operated via Telegram, automate social engineering efforts to bypass two-factor authentication (2FA) mechanisms.
Threat actors begin by employing credential stuffing tactics to identify accounts protected by 2FA.
They then leverage pre-recorded or AI-driven voice calls and SMS impersonations through OTP bots to coerce unsuspecting victims into divulging their authentication codes under the guise of fraud prevention or account verification.
Once the 2FA code is acquired, attackers secure unauthorized access to victims’ accounts, changing passwords and recovery settings to lock out the legitimate owners completely.
According to the Report, Radware documented the presence of 38 distinct OTP bot services costing $10-$50 per attack, with mentions increasing by 31% within the research period.

This automated approach dramatically scales these social engineering attacks, making them more efficient and harder to detect.
Distributed Denial-of-Service (DDoS) attacks have undergone significant technological advancements, facilitated by the growth of DDoS-as-a-service ecosystems.
Operators now offer sophisticated tools capable of generating over 35,000 requests per second for as little as $50.
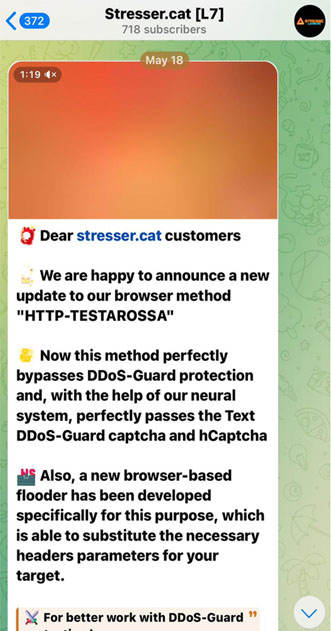
Among these, a concerning innovation is the incorporation of artificial intelligence (AI), as evidenced by “Stressed Cat,” an AI-enabled DDoS tool launched in May 2024.
Unlike traditional DDoS tools, which aim to bypass captchas, “Stressed Cat” employs advanced AI to solve captcha challenges, thus requiring fewer bot sessions and evading detection systems reliant on captcha mechanisms.
This innovation effectively lowers operational costs for attackers while increasing the rate of success for malicious campaigns.
The decentralization of cybercrime showcased by this research highlights the increasing separation between developers of attack tools and their operators.
This fragmentation complicates efforts by law enforcement and security experts to attribute malicious activities to specific actors.
Radware’s findings underscore the necessity for cybersecurity professionals to shift their perspectives from reactive defense strategies to proactive threat intelligence operations.
Monitoring deep and dark web platforms for emerging threats is essential to counter the rapidly advancing capabilities of cybercriminals targeting financial institutions and other industries.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates