The threat landscape targeting financial institutions continues to evolve, with researchers at CyberProof reporting a sharp increase in DarkCloud Stealer infections during August 2025.
The group’s Managed Detection and Response analysts and threat hunters identified phishing campaigns that utilized RAR file attachments as the primary vector.
Once executed, the malware exfiltrates sensitive information, including credentials from browsers, FTP clients, and email applications, and employs advanced persistence and process injection techniques to evade detection.
Delivery via Phishing and Loader Execution
The attack begins with a phishing email carrying the attachment “Proof of Payment.rar” (hash: 0ebc9f70eba3c50c2e6be8307f25e7ca572b1a26a1c37af00b22549f6e0a8129), which contains a malicious VBE file executed by wscript.exe.
Once launched, the script decodes Base64-encoded PowerShell commands designed to download a seemingly benign JPG file “universe-1733359315202-8750.jpg” (SHA256: 89959ad7b1ac18bbd1e850f05ab0b5fce164596bce0f1f8aafb70ebd1bbcf900).
The image carries an embedded .NET DLL loader hidden within its data, extracted and deployed using PowerShell’s [Reflection.Assembly]::Load() method.
This loader maintains persistence by copying JavaScript payloads as wardian.js into the user’s downloads path and creating registry entries to re-execute after reboot.
Further examination exposed additional obfuscated Base64 strings, resolving to remote payload links hosted on compromised domains. The primary payload of DarkCloud is then decrypted in memory, avoiding placement on disk, before being injected into MSBuild.exe and later mtstocom.exe.
Credential Theft and Persistence Techniques
Once executed via process hollowing, DarkCloud performs systematic credential theft by accessing login data from browsers such as Chrome and Microsoft Edge. CyberProof’s telemetry revealed attempts to harvest additional information from Outlook and FTP clients.
Stolen credentials are exfiltrated through FTP and SMTP channels, thereby expanding the operational flexibility of attackers.
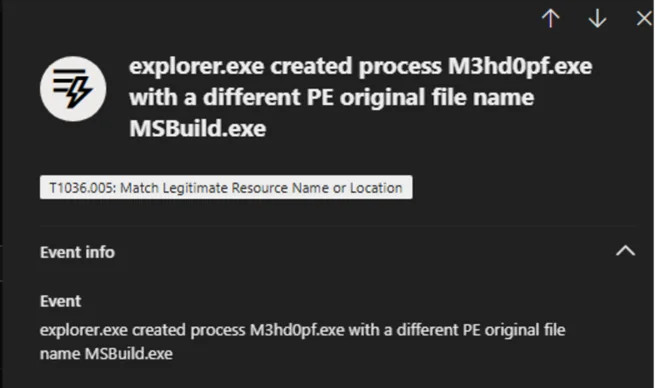
DarkCloud further ensures survival by creating multiple persistence mechanisms, including registry keys under HKCU\Software\Microsoft\Windows\CurrentVersion\Run and dropping masqueraded executables like M3hd0pf.exe in user roaming folders.
Notably, activity extended to dynamic generation algorithm (DGA)-based communications, with outbound connections to suspicious domains such as dmetis[.]xyz, wizwig[.]biz, and financialsecured[.]xyz.
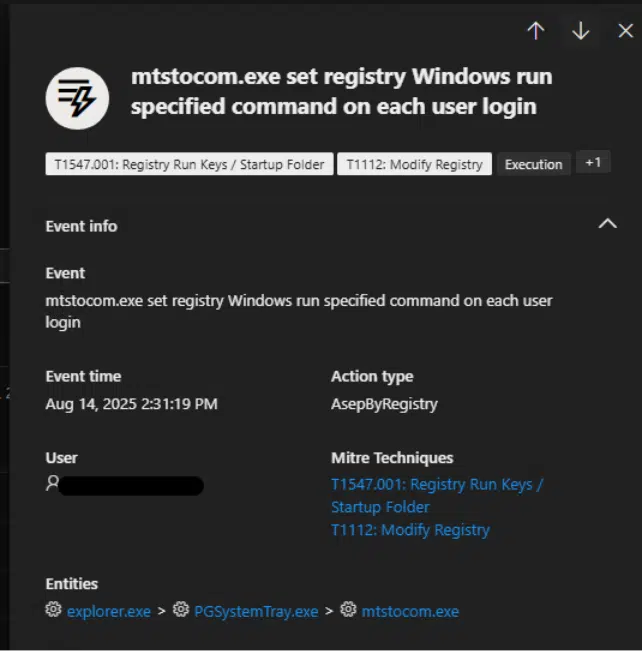
EDR alert analysis highlighted multiple stages of process injections into trusted binaries, which complicates detection. Investigative logs confirmed correlation between credential theft, persistence actions, and network traffic patterns typical of infostealer operations.
Defensive Recommendations
CyberProof urges organizations, especially financial companies, to implement proactive monitoring for malicious attachment indicators, such as unusual RAR or VBE files.
Analysts recommend hunting for anomalous script execution, PowerShell activity with [Reflection.Assembly]:: Load(), and unauthorized access attempts to Chrome or Edge credential databases.
Additionally, restricting outbound connections to high-risk TLDs, including .shop, .xyz, .info, and .net, can reduce exfiltration risks.
The DarkCloud campaign demonstrates how adversaries blend social engineering with fileless execution tactics to maximize stealth.
By releasing this detailed attack analysis and Indicators of Compromise, CyberProof aims to strengthen community detection efforts and build resilience against increasingly sophisticated criminal malware operations.
Indicators of Compromise
- https://archive.org/download/universe-1733359315202-8750/universe-1733359315202-8750.jpg
- http://mycoosin.lovestoblog.com/arquivo_1310f7ed369f46bcbaf688d16fd596b9.txt
- http://mycoosin.lovestoblog.com/arquivo_dd5cdfb7a64340d5940293c44c77ca50.txt
- 0ebc9f70eba3c50c2e6be8307f25e7ca572b1a26a1c37af00b22549f6e0a8129
- 90eefdabd6f33de39071d4bfd540654bfdc60bff3198d5637f82e10b0cabd01d
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates