AUTOSUR, a French company specializing in vehicle inspection and technical control services, has suffered a significant data breach involving the exposure of over 12.3 million customer records.
The breach, first reported on March 16, 2025, by the cybersecurity monitoring platform FalconFeeds, was announced on the cybercrime forum BreachForums.
The leaked dataset includes highly sensitive personally identifiable information (PII), such as names, phone numbers, email addresses, hashed passwords, physical addresses, vehicle details, and license plate numbers.
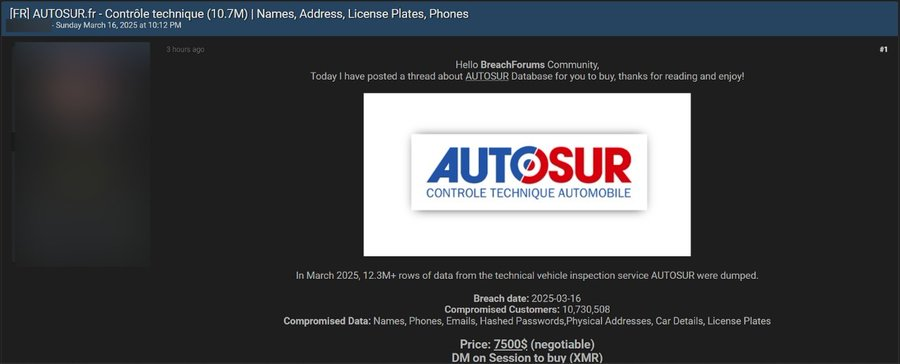
Breach Overview
The compromised data, totaling more than 12.3 million rows, was posted by a BreachForums member under the thread title “[FR] AUTOSUR.fr | Names, Address, License Plates, Phones”.
According to the forum post, the breach includes:
- Full names and residential addresses
- Email addresses and bcrypt-hashed passwords
- Vehicle inspection records and license plate numbers
- Contact phone numbers and car ownership details
The exposed information poses severe risks of identity theft, phishing campaigns, and automotive fraud, particularly through SIM-swapping attacks or targeted social engineering.
AUTOSUR’s Role and Impact
AUTOSUR operates a network of technical control centers across France, mandated to ensure vehicles meet safety and emissions standards.
The breach’s scale suggests attackers gained access to backend systems storing historical customer data, potentially through compromised credentials or unpatched vulnerabilities.
While the exact attack vector remains unconfirmed, the inclusion of bcrypt-hashed passwords indicates potential insider access or database exploitation.
BreachForums’ Involvement
BreachForums, a notorious dark web platform for trading stolen data, has been linked to high-profile breaches, including the 2024 Europol portal leak and the DC Health Link incident.
The forum’s resurgence in 2024 under the new administration highlights its role in enabling cybercriminal collaboration.
The AUTOSUR leak aligns with a broader trend of ransomware groups targeting automotive sectors, as seen in early 2025 attacks on dealerships and supply chains.
Technical Analysis and Risks
The leaked dataset’s structure—organized by customer profiles and vehicle metadata—enables attackers to correlate PII with vehicle histories, creating opportunities for:
- Synthetic identity fraud: Combining real names, addresses, and license plates to bypass KYC checks.
- Phishing lures: Tailored emails referencing vehicle inspection dates or fines.
- Physical theft: Targeting specific car models using registration details.
Cybersecurity experts warn that bcrypt hashing, while robust, is vulnerable to brute-force attacks if weak passwords are used.
Customers reusing credentials across platforms face elevated risks of account takeover.
Regulatory and Industry Implications
Under the EU’s General Data Protection Regulation (GDPR), AUTOSUR could face fines of up to 4% of global revenue for inadequate security measures, mirroring penalties imposed on Dedalus Biologie (€1.5 million) and AXA in prior French breaches.
The breach also underscores systemic vulnerabilities in automotive IT infrastructure, which saw a 78% rise in ransomware attacks in early 2025.
Mitigation Recommendations
Affected users are advised to:
- Reset passwords and enable multi-factor authentication (MFA) on all accounts.
- Monitor credit reports and enable fraud alerts.
- Inspect vehicles for tampering, particularly electronic control units (ECUs).
- Use breach notification services like Have I Been Pwned to track exposures.
For organizations, the incident highlights the need for:
- Zero-trust architecture to limit lateral movement in networks.
- Regular audits of third-party vendors’ security postures.
- Encryption of sensitive data at rest and in transit.
Ongoing Investigations
French authorities, including the National Cybersecurity Agency (ANSSI), are collaborating with Europol to trace the breach’s origin.
No ransomware group has claimed responsibility, though the BreachForums post suggests data may be monetized in dark web marketplaces or leveraged for future attacks.
AUTOSUR has yet to release an official statement, but the breach underscores the critical need for enhanced cybersecurity protocols in industries handling dual physical-digital assets.
As cybercriminals increasingly target operational technology (OT) systems, the automotive sector’s convergence of IoT and customer data remains a high-risk frontier.
Also Read: