Q3 2025 saw a surge in ransomware activity to record levels, driven by Scattered Spider’s announcement of its own RaaS platform and LockBit’s comeback with “LockBit 5.0,” which explicitly targeted critical infrastructure, alongside new strategic alliances among leading operators.
At the same time, the number of active data-leak sites reached an all-time high of 81 as emerging groups expanded into new regions and industries, despite the total number of listed organizations remaining essentially unchanged from Q2.
Scattered Spider’s RaaS Ambitions
In late August, Scattered Spider, known for high-stakes social engineering, hinted at launching ShinySp1d3r, its inaugural RaaS platform. A ransom note image on Telegram proclaimed it would be “the best RaaS to ever live,” promising seamless integration of data exfiltration and file encryption.
Unlike prior collaborations with Russian-speaking services such as DragonForce and ALPHV, ShinySp1d3r signals a bid for independence, uniting Scattered Spider’s MFA-bypass phishing methods, leveraging tools like Evilginx with bespoke encryption payloads optimized for rapid rollout.

Security teams should adapt red-team exercises to reflect ShinySp1d3r’s two-phase assault: initial credential harvesting followed by swift on-site encryption and data theft.
LockBit’s Critical Infrastructure Offensive
On September 3, LockBit reemerged, marking its sixth anniversary of the LockBit affiliate program with the release of LockBit 5.0.
For the first time, its affiliates are expressly permitted to strike critical infrastructure, including nuclear, thermal, and hydroelectric facilities, until an accord with the FBI dictates otherwise.
This departure from pre-2021 caution reflects LockBit’s ambition to retaliate against law enforcement actions following the Colonial Pipeline incident. Operational enhancements include OT-aware ransomware loaders that evade conventional IT-focused endpoint detection and security solutions.
Defenders must enforce rigorous Purdue-Model segmentation, isolate OT domains, and implement application whitelisting to block unauthorized binary execution.
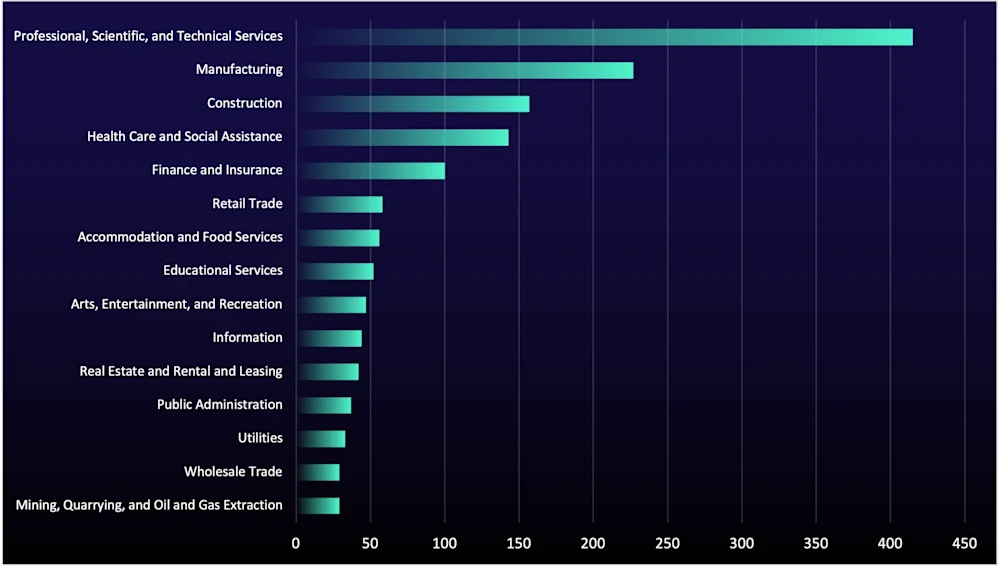
Data-Leak Sites Surge to an All-Time High amid Scattered Spider RaaS and LockBit 5.0
Active data-leak sites climbed from 72 in Q2 to 81 in Q3, fueled by fledgling RaaS outfits such as Devman2, The Gentlemen, and Cephalus.
Devman2 alone drove a 69 percent jump in Thai listings, reflecting a shift toward rapidly digitizing markets. Health care sector exposures jumped 31 percent as smaller actors exploited legacy clinical networks.
Meanwhile, professional, scientific, and technical services saw a 17 percent rise in listings, while manufacturing and construction dipped by 5 percent and 19 percent, respectively.
These dynamics illustrate an industry-wide pivot to double extortion, OT targeting, and localized campaigns in under-defended regions.
As alliances among DragonForce, Qilin, and the revitalized LockBit emerge, organizations face a multifaceted threat.
Beyond patch management and network segmentation, proactive leak-site monitoring, robust file-containment policies against remote SMB encryption, and fortified help-desk protocols to counter advanced social engineering will be essential.
With ShinySp1d3r’s launch on the horizon and LockBit’s pivot to critical infrastructure, Q4 promises further intensification of global ransomware campaigns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates