A newly uncovered botnet leveraging thousands of compromised network devices has been observed distributing malware-laden spam emails by exploiting DNS misconfigurations.
Infoblox Threat Intel reported that the botnet, built on hijacked MikroTik routers, is delivering trojans via spoofed sender domains that bypass standard email authentication mechanisms.
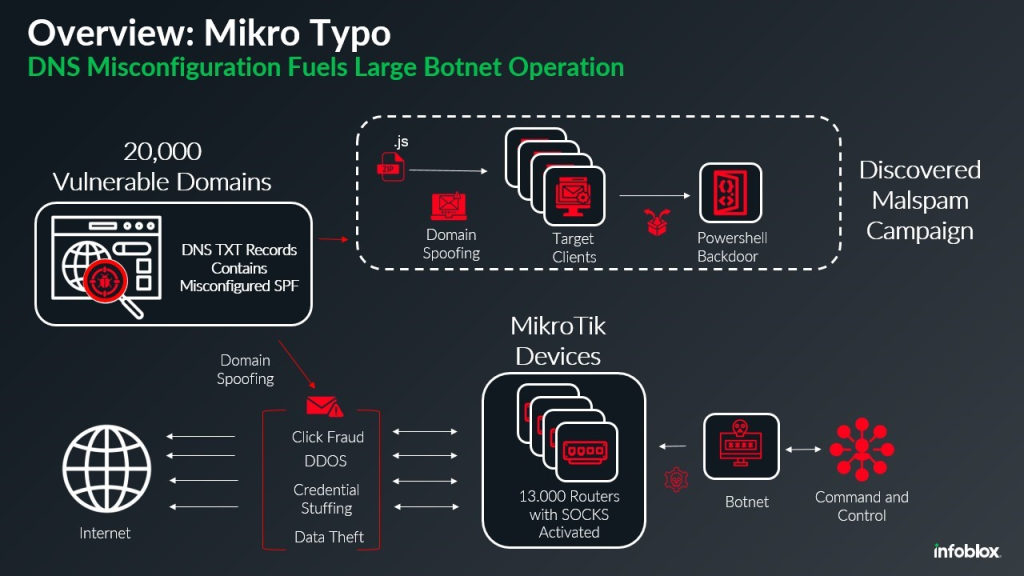
A Botnet on 13,000 Mikrotik Devices
The campaign first surfaced in late November, when researchers discovered malspam emails imitating freight invoices from DHL.
The attachments, disguised as invoice or tracking ZIP files, contained obfuscated JavaScript loaders, which executed PowerShell commands to connect with a command-and-control (C2) server linked to prior malicious activity.
Analysis of email headers revealed infrastructure spanning roughly 13,000 hijacked MikroTik routers across multiple firmware versions.
Despite older routers having well-known vulnerabilities, including a hardcoded “admin” account with a blank password, the compromised fleet also included devices running recent firmware.
The attackers appear to have deployed scripts enabling SOCKS proxies, effectively transforming the devices into traffic relays.
This proxy setup not only anonymizes malicious activity but also opens the devices for abuse by other cybercriminals.
Researchers noted that while the botnet consists of 13,000 routers, its configuration as SOCKS relays potentially allows hundreds of thousands of additional systems to use the network as a cover for malware delivery, phishing, or data exfiltration.
DNS Misconfiguration Enables Email Spoofing
Central to the success of the campaign was the abuse of misconfigured DNS SPF (Sender Policy Framework) records.
SPF is designed to validate which servers are authorized to send email on behalf of a domain, providing a key layer of protection against spoofing. Properly configured records typically use “-all” to reject unauthorized senders.
However, investigators found that nearly 20,000 sender domains contained weakened or misconfigured SPF records, often using “+all.”
This setting effectively authorizes any server to send emails for the domain, nullifying protections and allowing threat actors to spoof legitimate companies.
With these DNS loopholes, malicious emails distributing trojans sailed past filtering systems, reaching targets who were more likely to trust them.
The implications extend well beyond spam delivery. With an arsenal of hijacked routers and a vast pool of spoofable domains, the botnet operator can escalate operations, ranging from distributed denial-of-service (DDoS) attacks to credential stuffing and data harvesting.
Experts stress that enterprises and individuals must regularly audit their DNS configurations, paying special attention to SPF, DKIM, and DMARC records. Secure device management is equally critical, particularly given MikroTik’s history of high-severity vulnerabilities and exposed default credentials.
This incident underscores a troubling reality in cybersecurity: seemingly minor misconfigurations, when scaled across thousands of devices and domains, enable attackers to weaponize the infrastructure of the internet itself.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates