North Korean state-sponsored actors have escalated their cyber operations by infiltrating foreign companies through legitimate remote employment, with recent data leaks exposing the sophisticated methods used by the “Jasper Sleet” threat group to secure positions in Web3, blockchain, and cryptocurrency sectors.
This analysis of leaked email addresses reveals critical patterns that organizations can use to identify fraudulent applicants before granting corporate system access.
Mass Email Operation Targeting Crypto Sector
Two significant data breaches have exposed the operational infrastructure used by DPRK IT workers to establish false identities for overseas employment.
The first leak contained 1,389 email addresses distributed through GoFile, with many overlapping with addresses from Operation Endgame 2.0, where Europol provided 15.3 million victim email addresses to Have I Been Pwned in May 2025.
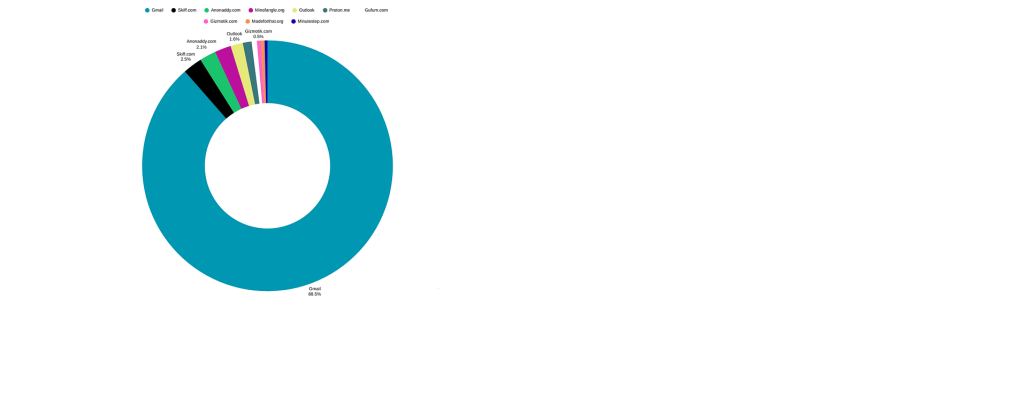
The analysis reveals Gmail dominates their preferred platforms with 1,175 accounts, followed by privacy-focused services like Skiff. Notably, 29 of the 63 identified email providers are temporary email services, indicating sophisticated operational security practices.
The actors demonstrate clear preferences for animal-themed usernames, with “Dragon” appearing in 14 email addresses, alongside frequent use of color codes like “gold” and “blue.”
Technical analysis of the email patterns reveals strategic age manipulation, as 11 addresses contain birth years indicating ages between 23 and 36.
The actors employ development-focused terminology extensively, using combinations like “enthusiastdev,” “uri.dev,” and “cocodev” to align with their target sectors. Four Russian surnames (Morozov, Kozlov, Fedoro, Chow) appear in the dataset, likely for attribution misdirection.
Password Analysis Reveals Operational Patterns
Password analysis from compromised accounts shows standardized patterns, with “123qwe!@#QWE” being the most common, followed by simple sequences like “11111111” and “123123.”
Two unique passwords stand out: “Xiah” appearing six times and “Jay231,” neither of which seems in common password databases. All Gmail accounts utilize Google Authenticator, 2FA, and recovery backup emails, demonstrating security awareness.
Detection and Prevention Strategies
The leaked data reveals extensive use of AI tools and services, with widespread compromise through CutOut Pro breaches in February 2024.
The second leak, discovered by ZachXBT, exposed operational documents showing purchases of SSNs, Upwork/LinkedIn accounts, phone numbers, and VPN services. The group utilizes AnyDesk for remote work execution and employs face-swapping technology for interview screening.
Organizations can implement detection measures by screening for the identified email patterns, implementing anti-deepfake detection tools, and conducting enhanced verification for applicants with Chinese or Russian connections.
The Ethereum wallet address 0x78e1a4781d184e7ce6a124dd96e765e2bea96f2c has been identified for transaction monitoring.
These revelations provide unprecedented insight into DPRK cyber operations, enabling organizations to strengthen their hiring processes against state-sponsored infiltration attempts targeting critical cryptocurrency and blockchain infrastructure.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates