Acronis Threat Research Unit (TRU) has published an extensive analysis of the DragonForce ransomware cartel, a sophisticated continuation of the Conti and LockBit ransomware lineage.
Emerging in 2023 as a Ransomware-as-a-Service (RaaS) operation, DragonForce has rapidly evolved into a cartel model, offering white-labeled payloads, customizable encryptors, and affiliate revenue-sharing effectively expanding its reach while complicating attribution efforts.
From RaaS to Cartel: A New Model for Cybercrime
Initially derived from the leaked Conti v3 code, DragonForce’s operations share notable overlaps with LockBit Green, including similar encryption routines, process handling, and backend configuration structures.
By early 2025, the group officially rebranded as the “DragonForce Ransomware Cartel,” claiming to offer affiliates 80 percent of profits and dedicated infrastructure support.
This affiliate-driven model has led to multiple ransomware offshoots, such as Devman and Mamona (later rebranded as Global), both built from DragonForce’s updated encryptor.
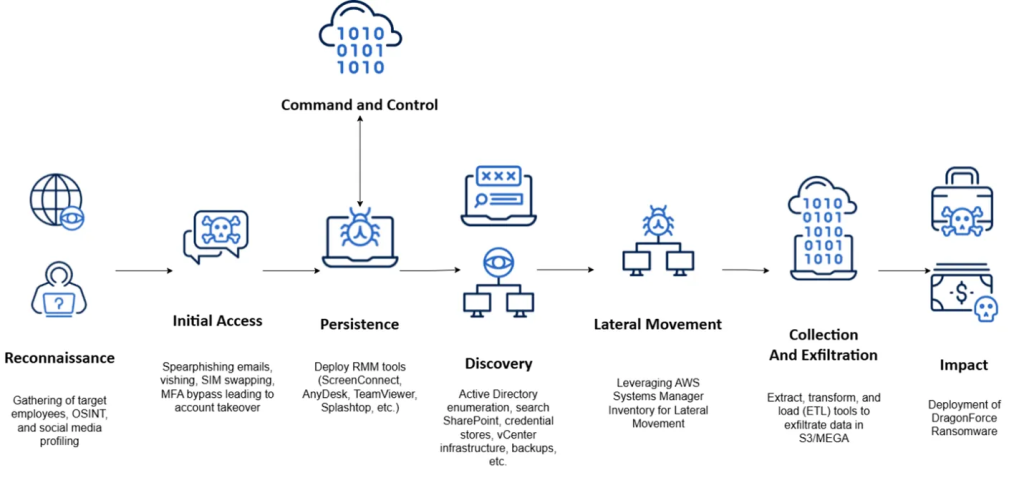
TRU’s report highlights that more than 200 victims across retail, airlines, insurance, and managed service provider (MSP) industries have appeared on DragonForce’s leak site since late 2023.
The group also made headlines for its attack on Marks & Spencer, conducted alongside Scattered Spider an initial access broker involved in phishing, SIM swapping, and MFA bypass activities.
This collaboration is part of a growing trend dubbed “Scattered LAPSUS$ Hunters,” linking DragonForce with threat actors like LAPSUS$ and ShinyHunters in a broader cybercrime coalition.
Technical Dissection: Conti DNA with BYOVD Capabilities
The analyzed DragonForce samples show evident Conti heritage but introduce several modifications. Developers switched to the MinGW toolchain, resulting in larger binaries and unified cross-platform compatibility.
Configuration data within the binaries is encrypted with ChaCha20 and supports customizable extensions, whitelist paths, and encrypted file naming.
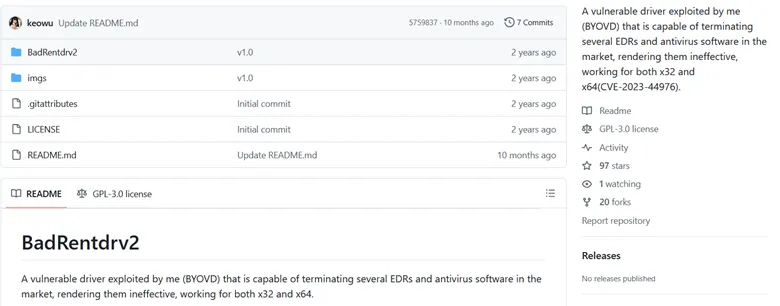
A standout feature of DragonForce’s latest variant is its use of bring-your-own-vulnerable-driver (BYOVD) techniques.
By exploiting signed but vulnerable drivers, notably truesight.sys and rentdrv2. sys, the ransomware terminates endpoint protection processes by sending system-level control codes via DeviceIoControl APIs. This enables privilege escalation and defense evasion beyond traditional methods.
The group has also improved the reliability of its encryption after an article on Habr exposed flaws in Akira’s cipher implementation.
DragonForce rectified similar weaknesses, ensuring stronger encryption of file headers and content. Files are still encrypted using a ChaCha20 key, which is then RSA-encrypted and appended to the file header, mimicking Conti’s structure.
DragonForce’s rise from Conti’s remnants underscores a larger industry shift from singular ransomware groups to collaborative cybercriminal cartels.
Through technical innovations, recruitment-centric operations, and partnerships with groups like Scattered Spider and DragonForce, DragonForce has positioned itself as one of the most active and dangerous ransomware ecosystems currently operating.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates