Security researchers at ANY.RUN have uncovered a new sample of the notorious Triada Android trojan, embedded inside a counterfeit Telegram app, showcasing a particularly sophisticated packer dubbed “Ducex”.
Nearly a decade after Triada’s emergence, its developers continue to push technical boundaries with evasion and anti-analysis techniques that challenge even seasoned analysts.
Obfuscation by Design
Ducex’s architecture is centered on rendering reverse engineering exceedingly difficult while camouflaging Triada’s malicious payload.
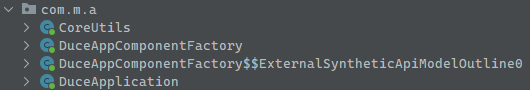
Upon decompiling the infected APK, analysts observed that the application’s entry point immediately invokes a custom DuceApplication class, which routes control through native code largely implemented in a library named “libducex.so”.
Most strikingly, functions within this library are not just obfuscated they are fully encrypted using a custom-modified RC4 algorithm with additional shuffling, disabling conventional static or dynamic code analysis.
Only an early initialization routine, .init_proc, is left readable, which subsequently decrypts the rest of the library’s functions in memory using configuration data and a 16-byte key.
The threat actors applied similar rigor to string obfuscation. All strings within the packer are encrypted with a simple, variant XOR method, making identification and signature generation for detection tools much more challenging.
Compounding these efforts, the control flow throughout the unpacked code is heavily convoluted with redundant loops and conditions, further frustrating attempts at decompilation or debugging.
Analysis Tool Detection
Ducex is engineered to thwart both on-device and off-device analysis. It implements APK signature verification, causing the app to crash if it has been resigned an immediate obstacle to most standard dynamic analysis workflows.
The packer employs a self-debugging routine that forks a child process, using ptrace to ensure only the app itself can trace or debug its execution, preventing external debuggers from attaching.
Furthermore, Ducex actively scans its process memory for signs of analysis frameworks such as Frida, Xposed, and Substrate.
If any of these are detected, the process terminates, stymying dynamic instrumentation and hook-based investigation.
These aggressive countermeasures leave analysts with only labor-intensive static reverse engineering as a viable path for investigation.
Rather than storing Triada’s payload as a discrete file, Ducex embeds the trojan’s code within an extended section at the end of its own classes.dex file, effectively sidestepping straightforward detection by file-based scanners.
Only the headers (and, typically, the first 2048 bytes) of the embedded DEX modules are encrypted, using a combination of custom RC4 and China’s SM4 block cipher, whose decryption routines and keys are also concealed within the packer’s code.
The unpacking sequence begins with initial decryption of each module using its own key, followed by a secondary decryption round with a shared key for all modules.
Once unpacked, the Java layer invokes Triada’s main loader, at which point the trojan’s capabilities are activated within the compromised app environment.
According to the Report, The discovery and analysis of Ducex reaffirm Triada’s reputation as an emblem of Android malware sophistication.
Its ability to evade both detection and forensic scrutiny is a testament to ongoing advancements in malicious Android tooling, and a warning to the cybersecurity community of the persistent threat posed by well-resourced and technically adept adversaries.
Indicators of Compromise (IOCs)
| Name | MD5 | SHA1 | SHA256 |
|---|---|---|---|
| 131eaf37b939f2be9f3e250bc2ae8ba44546801b5ca6268f3a2514e6a9cb8b5c.apk | 25faee9bbf214d975415ae4bd2bcd7b9 | 06f8ca016b2bf006702501263818b7606851f106 | 131eaf37b939f2be9f3e250bc2ae8ba44546801b5ca6268f3a2514e6a9cb8b5c |
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates