A severe vulnerability in Erlang/OTP’s SSH implementation has emerged as a critical threat to operational technology (OT) networks worldwide, with researchers documenting a massive surge in exploitation attempts targeting industrial control systems across healthcare, education, and high-tech sectors.
Vulnerability Details and Technical Impact
CVE-2025-32433, disclosed on April 16, 2025, represents one of the most severe security flaws discovered this year, earning the maximum CVSS score of 10.0.
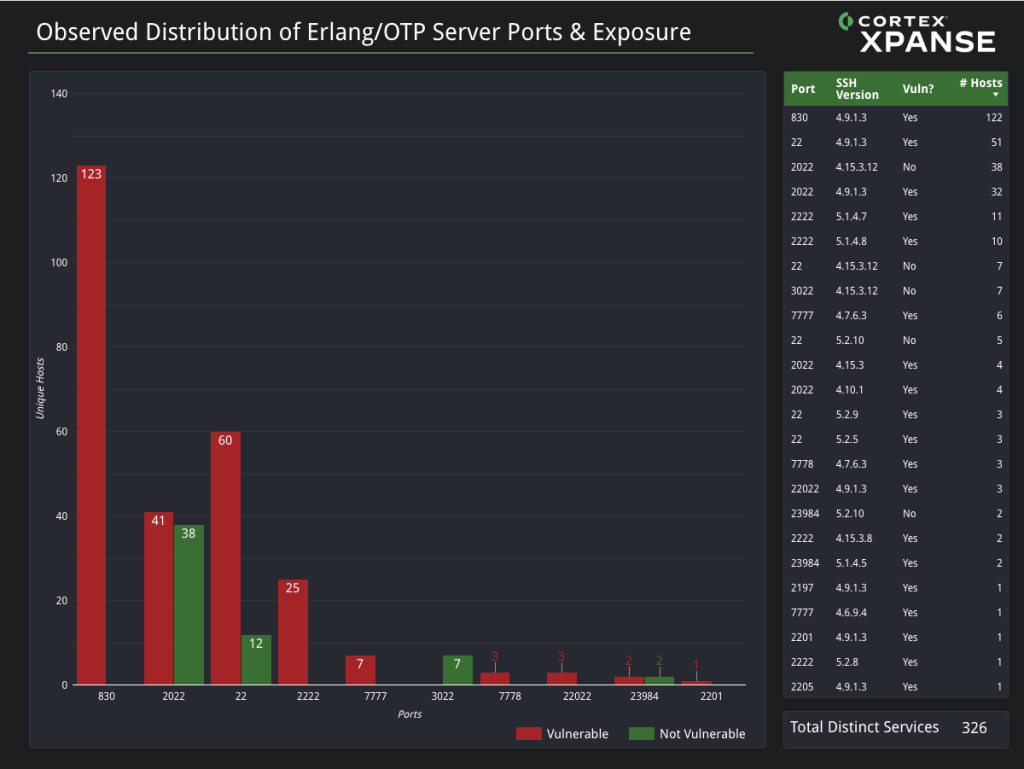
The vulnerability affects Erlang/OTP versions before OTP-27.3.3, OTP-26.2.5.11, and OTP-25.3.2.20, allowing unauthenticated attackers to execute arbitrary code by exploiting improper SSH protocol message handling.
The flaw stems from the SSH server’s failure to reject connection protocol messages sent before authentication completion properly.
Attackers can send specially crafted SSH_MSG_CHANNEL_OPEN and SSH_MSG_CHANNEL_REQUEST messages during the transport layer handshake, bypassing authentication requirements entirely when the SSH daemon runs with elevated privileges.
In a standard configuration, successful exploitation grants complete system control.
Security researchers from Ruhr University Bochum discovered the vulnerability using state machine learning techniques to analyze the Erlang/OTP SSH server’s protocol handling. Within 24 hours of disclosure, proof-of-concept exploits became publicly available, dramatically accelerating the threat landscape.
Widespread Exploitation Targeting OT Networks
Analysis by Palo Alto Networks reveals alarming exploitation patterns, with 70% of detected attacks originating from firewalls protecting operational technology networks.
Between May 1-9, 2025, researchers observed over 3,376 signature triggers globally, with 2,363 specifically targeting OT environments.
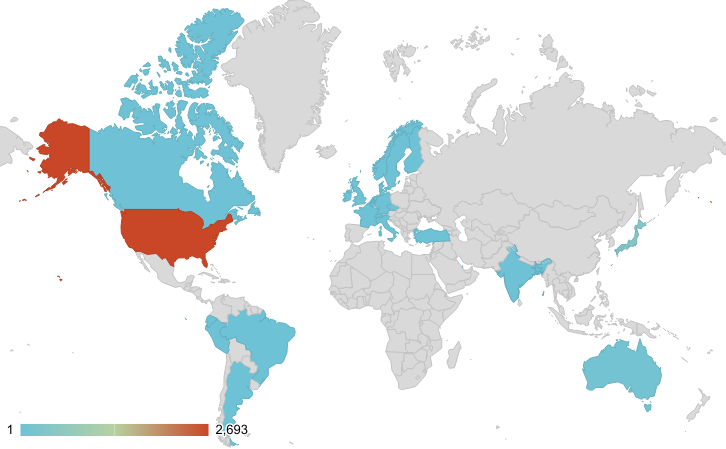
The geographic distribution shows concerning concentrations in industrialized nations. Japan experienced 99.74% of exploit attempts within OT networks, while the United States, Netherlands, Ireland, Brazil, and Ecuador saw 100% of signature triggers occurring in operational environments.
This pattern suggests deliberate targeting of critical infrastructure rather than opportunistic scanning.
Industry analysis reveals disproportionate impact on sectors not traditionally considered high-risk OT targets.
The education sector accounted for 72.7% of total exploit attempts, with healthcare, agriculture, media, and high technology experiencing over 85% of attacks directly on their OT firewalls.
Notably, utilities, energy, mining, and aerospace sectors showed minimal detection activity, potentially indicating surveillance gaps or delayed targeting strategies.
Advanced Attack Techniques and Threat Infrastructure
Researchers have identified sophisticated attack payloads deployed through CVE-2025-32433 exploits. Standard techniques include reverse shell implementations using file descriptors to establish TCP connections, enabling remote command execution.
One observed payload redirected shell input/output to IP address 146.103.40[.]203:6667, a port typically associated with botnet command infrastructure.
More concerning are DNS-based Out-of-Band Application Security Testing (OAST) techniques discovered in exploitation attempts.
Attackers use randomized subdomain lookups under domains like dns.outbound.watchtowr[.]com to validate successful code execution without returning direct results.
This approach, commonly employed in advanced persistent threat campaigns, demonstrates the sophisticated nature of current exploitation efforts.
The vulnerability’s exploitation follows concentrated burst patterns rather than continuous attacks, with peak activity days showing over 80% OT-specific triggers.
This pattern suggests coordinated campaigns specifically targeting operational infrastructure during optimal timeframes for maximum impact.
Organizations must immediately upgrade to patched Erlang/OTP versions: OTP-27.3.3, OTP-26.2.5.11, or OTP-25.3.2.20.
Critical temporary measures include disabling SSH servers where possible and implementing strict firewall rules restricting access to trusted sources only.
The vulnerability’s addition to CISA’s Known Exploited Vulnerabilities catalog on June 9, 2025, underscores the urgent need for comprehensive remediation across all affected systems.
Indicators of Compromise
- .dns.outbound.watchtowr[.]com
- 194.165.16[.]71
- 146.103.40[.]203
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates