Cybersecurity researchers at Raven AI have uncovered a sophisticated phishing campaign that exploits Cisco’s Safe Links technology, turning a trusted security mechanism into an attack vector.
The campaign demonstrates how attackers leverage legitimate security infrastructure to bypass traditional email filtering systems and exploit user trust in established cybersecurity brands.
Attack Methodology and Technical Implementation
The attack leverages Cisco’s Safe Links URL rewriting functionality, which is designed to protect users by routing suspicious links through Cisco’s threat analysis infrastructure.
Attackers have discovered multiple methods to generate legitimate Cisco Safe Links that redirect to malicious destinations, effectively weaponizing the protective technology against its intended beneficiaries.
The attack vector exploits the inherent trust users place in URLs beginning with “secure-web.cisco.com,” creating a psychological security bypass that complements the technical evasion techniques.
Traditional email security gateways often whitelist Cisco domains, allowing these malicious communications to reach user inboxes without proper scrutiny.
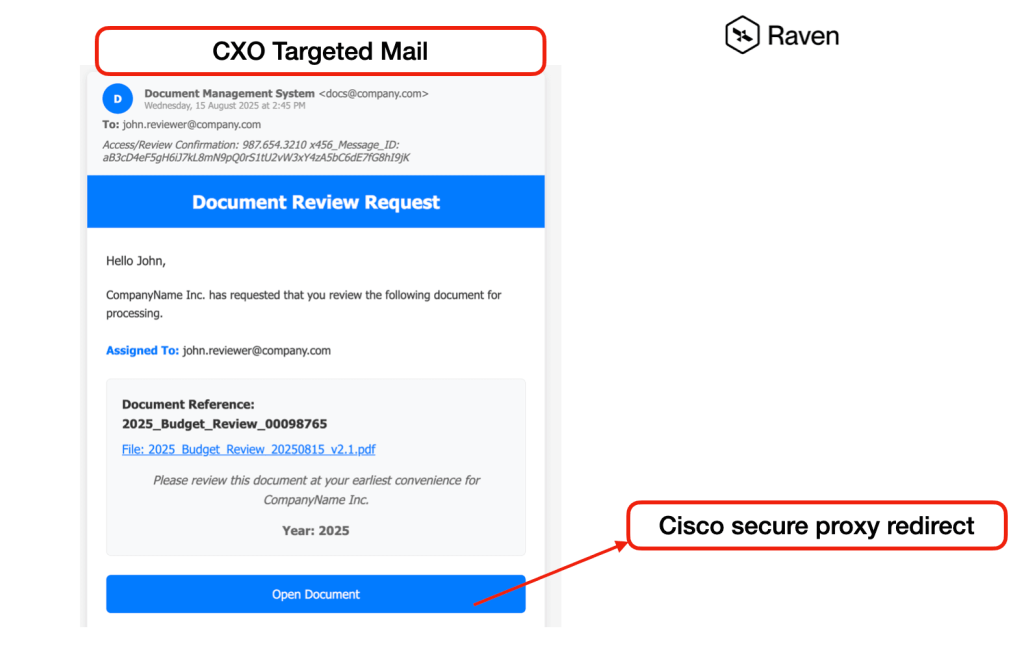
Attack Vector Generation Methods
Researchers identified four primary techniques cybercriminals use to obtain legitimate Cisco Safe Links:
| Method | Technical Process | Success Rate | Detection Difficulty |
|---|---|---|---|
| Insider Compromise | Utilize compromised accounts within Cisco-protected organizations | High | Moderate |
| SaaS Integration Abuse | Exploit cloud services that route emails through Cisco infrastructure | Medium | High |
| Trojan Horse Technique | Use legitimate business accounts to self-generate malicious Safe Links | High | Low |
| Link Recycling | Reuse previously generated Safe Links from successful campaigns | Variable | High |
Advanced Detection Through Context-Aware Analysis
Raven AI’s detection engine identified the campaign through contextual analysis rather than traditional signature-based methods.

The system analyzed business process workflows, sender behavior patterns, and multi-layered deception techniques that would typically bypass conventional security solutions.
The detected phishing campaign employed professional formatting and legitimate business terminology, specifically targeting document review processes with “2025_Remittance_Adjustment” themed communications.
The attackers utilized Swiss domain registration and professional branding to enhance credibility while maintaining multiple attack vectors through primary and alternative access methods.
Security Implications and Defense Evolution
This campaign represents a fundamental shift in attack methodology, where cybercriminals exploit trusted security infrastructure rather than circumventing it entirely.
Traditional security solutions struggle against these attacks because they appear legitimate at every technical checkpoint, with malicious intent concealed within contextual behavioral patterns.
The exploitation of Cisco Safe Links demonstrates how attackers are weaponizing the time gap between threat emergence and threat intelligence classification.
Even robust security systems require processing time to identify and categorize new threats, creating exploitable windows for sophisticated campaigns.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates