Security researchers at MailMarshal SpiderLabs have uncovered a sophisticated phishing campaign that exploits Facebook’s external URL warning system to bypass user suspicion and harvest login credentials.
By abusing the platform’s redirect mechanism, attackers craft seemingly legitimate links that lead to fraudulent login portals, luring victims into divulging their usernames and passwords.
Abuse of Facebook’s URL Warning System
The campaign uses Facebook’s built-in redirect service, which warns users when they are about to leave the platform.
Instead of alerting to a known malicious destination, the attackers register benign domains such as thebeachvilla.co.za and omniotech. Co. UK, then host a dynamic redirect script that points to the real phishing page.
When a user clicks the link from a Facebook post or message, the warning dialog still displays the registered domain, fostering a false sense of trust.
Once confirmed, the redirect script pushes the victim to a look-alike Facebook login page, where the entered credentials are captured in real time and sent to the attacker’s command-and-control server.
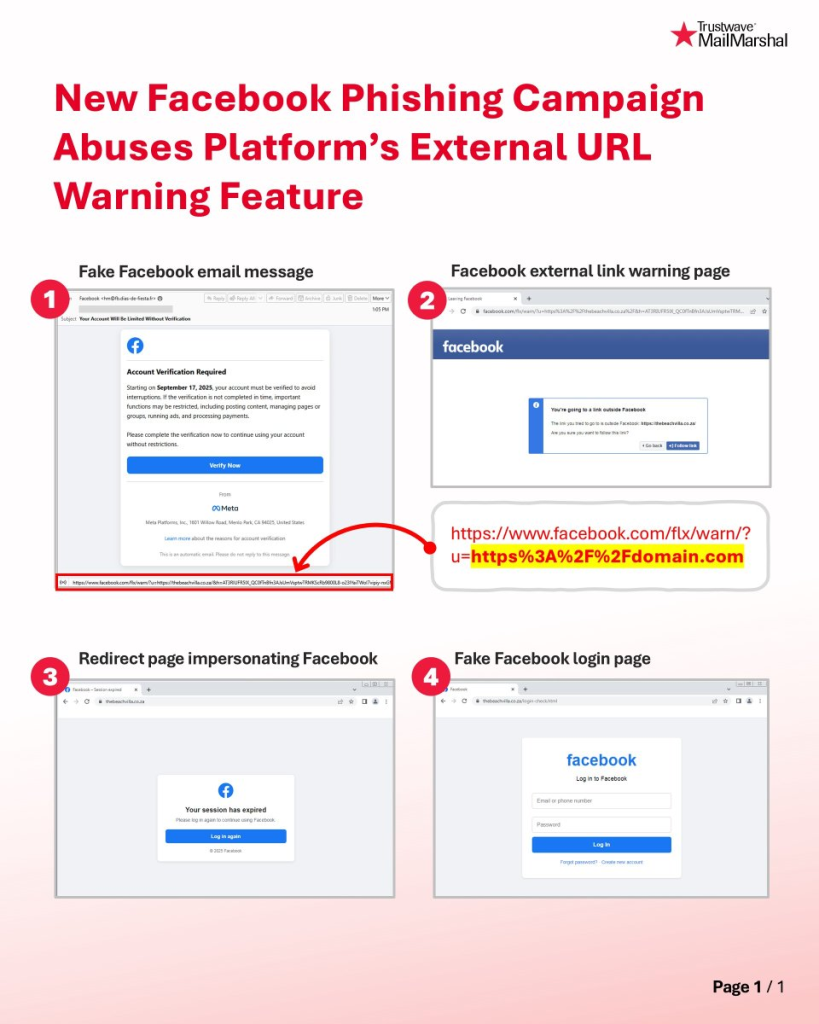
To further evade detection, each redirect URL is unique per recipient. The phishing emails localized in English, German, Spanish, and Korean contain personalized parameters that embed language codes and urgency tokens.
For example, the URL https://alehclair[.]com/?lang=de&alert=security triggers a German-language login lure stating that “Ihr Konto wurde ungewöhnliche Aktivitäten festgestellt” (unusual activity detected).
Similar templates exist for Spanish (“Se han detectado actividades inusuales”) and Korean (“비정상적 활동이 감지되었습니다”). These localization tactics elevate the perceived legitimacy of the message and increase victim engagement.
Credential Harvesting and Exfiltration
Upon submitting credentials, victims are immediately redirected to the genuine Facebook login page, minimizing suspicion by presenting a successful login experience.
Meanwhile, the harvested data is transmitted via HTTP POST to hidden endpoints such as hxxps://phandoriloxquebrantavixomuldranitho.vercel.app/900nlm.html.
SpiderLabs analysts note that the attacker’s infrastructure resides across at least seven domains, including timmermansgww.nl and bikewelt-frankenwald.de, all registered within the past month.
Each domain hosts identical phishing templates but uses unique redirector scripts to isolate tracking and prevent widespread blacklisting.
Analysis of email headers reveals the use of compromised MailMarshal servers to relay messages, bypassing standard anti-spam filters by matching legitimate MailMarshal IP ranges.
The emails carry subject lines like “Facebook Security Alert” and “Account Verification Needed,” and include forged DKIM signatures that align with Facebook’s sending domains, further complicating detection by email security gateways.
Attackers also employ URL shorteners sparingly, preferring direct domain references to reduce additional redirection steps that might alert security tools.
Victims are advised to scrutinize external-link warnings closely and verify the domain names in warning dialogs. Facebook account holders should enable two-factor authentication (2FA) and consider using a password manager to auto-fill credentials only on verified origins.
Organizations running MailMarshal should audit recent email logs for messages referencing the identified domains and apply domain-based message authentication, reporting, and conformance (DMARC) policies to block similar spoofing attempts.
By blending social-engineering urgency with technical manipulations of trusted platforms, this phishing campaign highlights the evolving threat landscape and the need for layered defenses that combine user education, robust email filtering, and strict domain validation.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates