Sophisticated cybercriminals are leveraging increasingly complex fake trading platforms to steal funds from unsuspecting investors across Asia, with organized fraud networks operating with military-like precision and transnational reach.
Group-IB’s latest technical investigation reveals that fraudulent websites impersonating cryptocurrency and forex exchanges have become the dominant vector for financially motivated threat actors, employing advanced social engineering tactics combined with shared backend infrastructure to systematize mass victimization.
The sophistication of these operations extends far beyond basic phishing attempts. According to Group-IB’s research, threat actors maintain centralized infrastructure supporting multiple scam domains simultaneously, evidenced by recurring API endpoints, shared SSL certificates, and exposed admin panels written in Simplified Chinese.
These technical artifacts serve as critical indicators for investigators attempting to correlate and dismantle interconnected operations.
Analysis of HTTP traffic between related domains revealed protected API endpoints returning 401 Unauthorized responses, indicating that authenticated backend connections are shared across multiple scam sites.
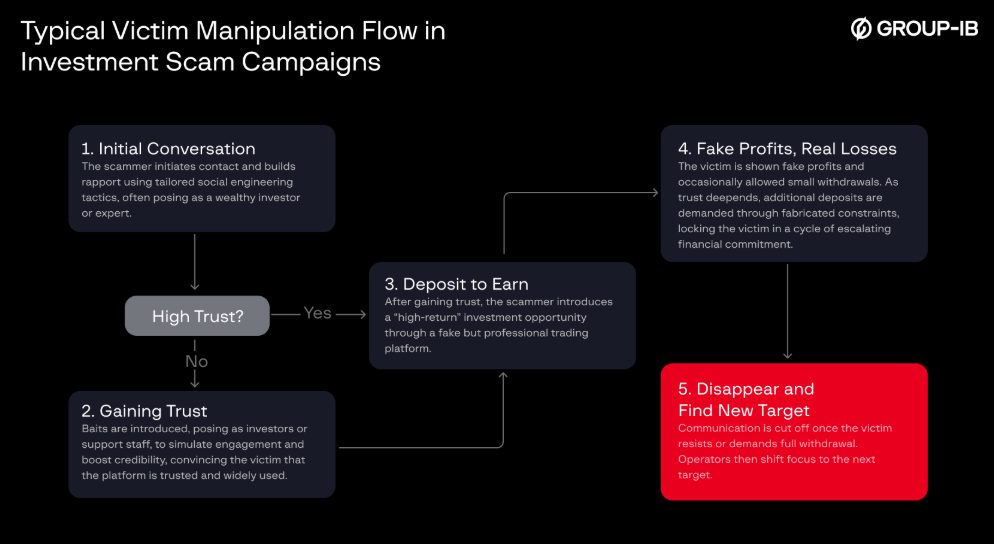
This pattern distinguishes organized criminal infrastructure from isolated fraud attempts. The operational structure behind these campaigns mirrors legitimate corporate hierarchies.
A mastermind operator oversees the entire ecosystem, delegating responsibilities to specialized teams: Target Intelligence personnel acquire stolen personal data from dark web markets; Promoters pose as successful investors on social media platforms like Facebook, Zalo, and TikTok; Payment Handlers exploit weakening Know Your Customer controls by utilizing stolen identity documents and mule accounts; and Backend Operators construct the technical framework sustaining the entire operation.
This distributed model enables rapid scaling and compartmentalization, complicating law enforcement investigations.
Technical Infrastructure Reveals Industrialized Fraud
Victims encounter layered access controls designed to restrict reconnaissance while binding new accounts to specific Promoters through referral codes.
Initial interfaces present chatbot-powered onboarding processes, often powered by third-party services like Meiqia, that screen pre-targeted victims before granting dashboard access.
More critically, analysis of chatbot payloads reveals backend configuration data, registered service emails, and system-level parameters in Simplified Chinese, providing forensic leads while indicating operator geography and reliance on outsourced services.
Auxiliary infrastructure components further demonstrate industrialization. Subdomain enumeration frequently uncovers chat simulation tools enabling bulk fabrication of fake success stories and testimony screenshots.
Archived scans via URLScan and the Wayback Machine preserve HTML comments in Chinese that contain developer update logs, providing linguistic fingerprints for attribution.
Discovery of identical admin panels across multiple domains resolving to shared hosting infrastructure confirms centralized backend deployment a hallmark distinguishing organized operations from opportunistic scammers.
Vietnam’s implementation of Circular 17/2024 in July 2025 enforced stricter biometric verification for corporate accounts. Yet, black markets are now responding predictably, advertising stolen identity data, forged business licenses, and face-swap technology that enables fraudsters to bypass enhanced controls.
The August 2025 arrest of 20 individuals linked to the billion-dollar Paynet Coin scam underscores enforcement efforts, yet the documented scale and transnational sophistication suggest substantially larger networks remain operational.
Group-IB warns that integrating generative AI into fraud infrastructure represents an emerging threat trajectory, potentially automating large-scale, personalized lures and interaction systems to create more convincing fabricated engagement at unprecedented scale.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates