Cybersecurity researchers at Proofpoint have uncovered a significant vulnerability in FIDO-based authentication systems that could potentially undermine one of the most trusted “phishing-resistant” security methods.
Despite FIDO passkeys being widely recommended to protect against credential phishing and account takeover threats, the research reveals that attackers can use specialized “phishlet” configurations to force users into less secure authentication methods, exposing them to adversary-in-the-middle (AiTM) attacks.
FIDO (Fast Identity Online) authentication has gained widespread adoption as organizations seek to combat increasingly sophisticated phishing campaigns.
The technology eliminates traditional password vulnerabilities by using hardware security keys combined with biometrics or PINs. However, Proofpoint’s findings demonstrate that even these advanced security measures have potential weaknesses when faced with determined attackers.
Technical Exploitation Through User Agent Spoofing
The attack leverages a critical gap in browser support for FIDO2 authentication with Microsoft Entra ID. Not all web browsers support passkey authentication; notably, Safari on Windows lacks this capability.
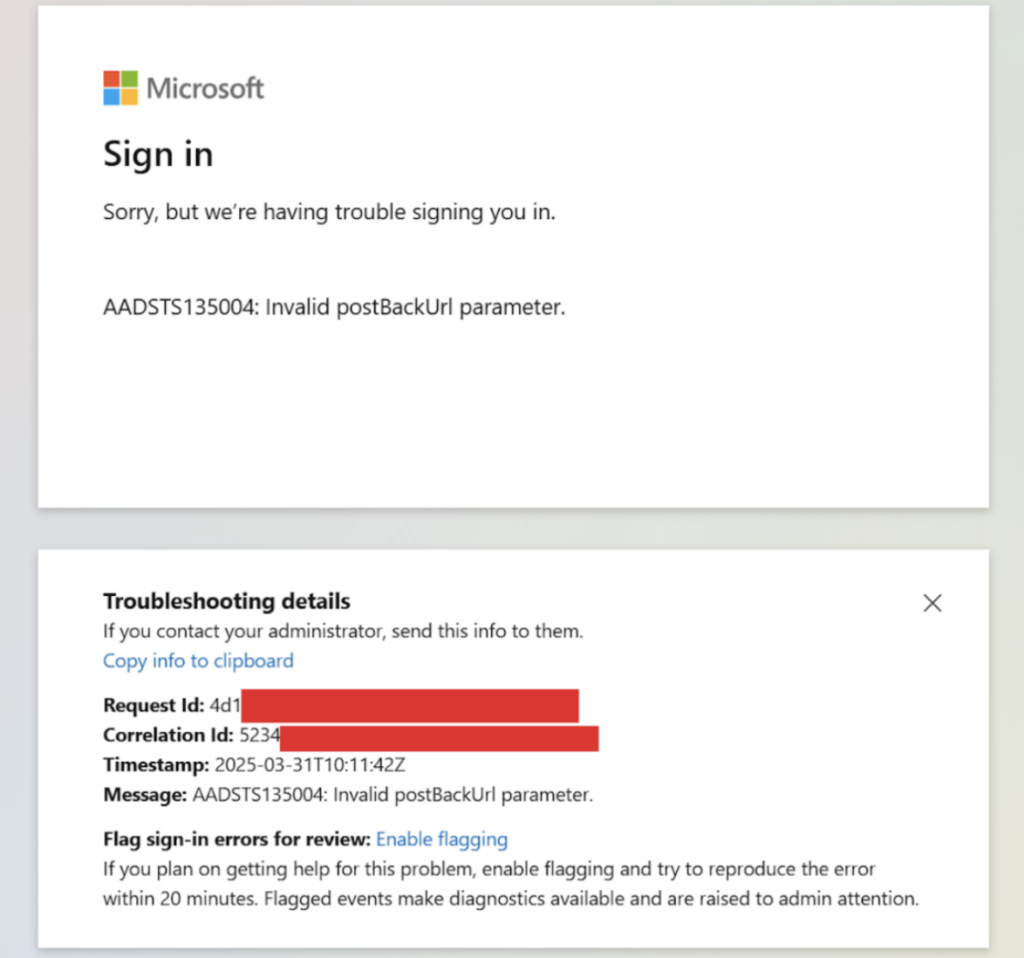
Attackers exploit this limitation by creating modified phishlets for AiTM attack frameworks like Evilginx that spoof unsupported user agents, essentially tricking the authentication system into believing the user’s browser cannot support FIDO.
When targets click on malicious links, they encounter authentication error messages prompting them to select alternative sign-in methods.
This forces users to downgrade to traditional multi-factor authentication methods, such as Microsoft Authenticator app verification codes.
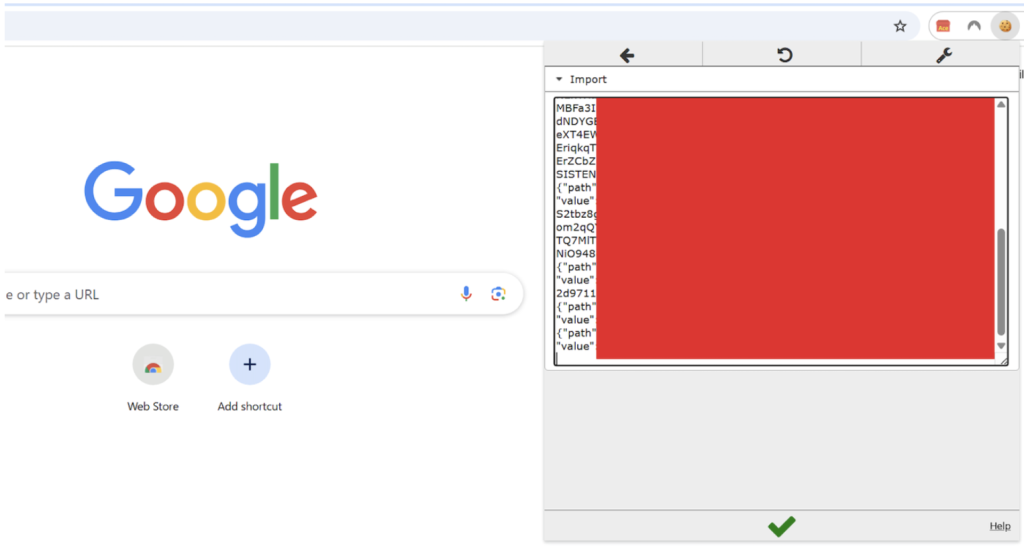
Once victims authenticate through these spoofed interfaces, attackers can intercept login credentials and session cookies, ultimately enabling complete account takeover.
The attack sequence requires the existence of alternative authentication methods besides FIDO, which most administrators maintain for practical account recovery purposes.
This creates the vulnerability window that sophisticated attackers can exploit through carefully crafted phishlets designed specifically for FIDO downgrade scenarios.
Current Threat Landscape and Future Implications
Despite the technical feasibility demonstrated by Proofpoint researchers, no FIDO authentication downgrade attacks have been observed in the wild.
Security experts attribute this to attackers currently focusing on “lower effort alternatives,” targeting users with weak single-factor authentication or vulnerable MFA methods that require less technical sophistication.
However, the research warns that as more organizations adopt phishing-resistant authentication methods, attackers may evolve their tactics.
“Authentication downgrade remains a key method for challenging ‘phishing-resistant’ authentication methods,” the researchers noted, suggesting that sophisticated adversaries and state-sponsored actors could eventually incorporate these techniques into their attack chains.
The findings underscore the ongoing cat-and-mouse game between cybersecurity defenses and threat actors, highlighting that even the most advanced authentication methods require careful implementation and continuous monitoring to maintain their effectiveness against evolving attack vectors.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates