Security researchers have identified a critical pre-authentication SQL injection vulnerability in Fortinet’s FortiWeb Fabric Connector, designated as CVE-2025-25257, that allows unauthenticated attackers to achieve remote code execution on affected systems.
This vulnerability affects multiple versions of FortiWeb across several major releases, potentially exposing organizations to significant security risks through their web application firewall infrastructure.
The vulnerability stems from improper input sanitization in the FortiWeb Fabric Connector’s authentication mechanism, where user-controlled data is directly embedded into SQL queries without proper validation.
FortiWeb Fabric Connector serves as an integration component that connects FortiWeb web application firewalls with other Fortinet ecosystem products, enabling dynamic policy updates based on real-time infrastructure changes.
The flaw allows attackers to manipulate SQL queries through crafted HTTP requests to the /api/fabric/device/status endpoint, completely bypassing authentication controls.
Vulnerability Details and Attack Vector
The vulnerability resides in the get_fabric_user_by_tokenfunction within FortiWeb’s httpsd binary, where the application constructs SQL queries using unsanitized user input.
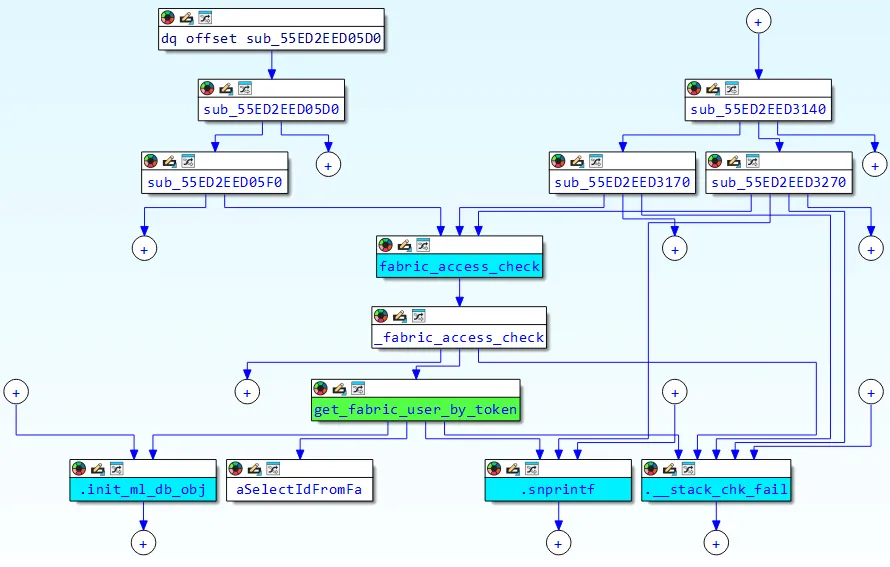
Researchers discovered that the function accepts bearer tokens through the Authorization header and directly incorporates them into SQL queries using the format: select id from fabric_user.user_table where token='%s'.
The vulnerable code affects multiple FortiWeb versions across several major releases:
- FortiWeb 7.6: versions 7.6.0 through 7.6.3
- FortiWeb 7.4: versions 7.4.0 through 7.4.7
- FortiWeb 7.2: versions 7.2.0 through 7.2.10
- FortiWeb 7.0: versions 7.0.0 through 7.0.10
Attackers can exploit this vulnerability by sending specially crafted HTTP requests with malicious SQL payloads in the Authorization header, such asBearer AAAAAA'or'1'='1, which bypasses token validation entirely.
The exploitation process involves overcoming several constraints, including space character limitations in the input parsing mechanism.
Attackers can circumvent these restrictions using MySQL comment syntax (/**/) to replace spaces, enabling complex SQL injection attacks.
A successful exploit returns detailed system information, including device serial numbers, version information, and supported API versions, confirming unauthorized access to the FortiWeb system.
Escalation to Remote Code Execution
Beyond simple SQL injection, researchers demonstrated how this vulnerability can be escalated to achieve remote code execution through MySQL’s INTO OUTFILEfunctionality.
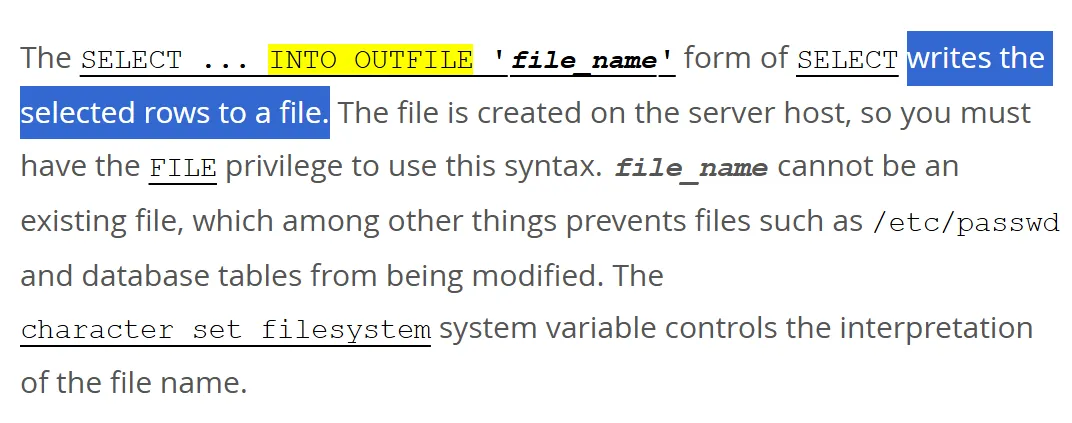
The FortiWeb system runs MySQL with root privileges, allowing attackers to write arbitrary files to the filesystem through SQL injection payloads.
The exploitation technique leverages Python’s site-specific configuration hooks by writing malicious .pthfiles to the Python site-packages directory.
These files contain Python code that executes automatically when the system’s existing CGI scripts are accessed.
By crafting payloads that write to paths like ../../lib/python3.10/site-packages/x.pth, attackers can achieve persistent code execution without requiring executable file permissions.
The attack chain involves multiple steps: first, the attacker injects SQL code to write a malicious Python payload to the site-packages directory; then, when legitimate CGI scripts are executed, Python’s site.py module automatically processes the malicious .pthfile, executing the attacker’s code with system privileges.
This sophisticated exploitation technique transforms a simple SQL injection into a complete system compromise.
Fortinet’s Response and Mitigation
Fortinet has addressed this vulnerability in updated versions of FortiWeb, implementing prepared statements to replace the vulnerable string formatting approach.
The company recommends immediate upgrades to FortiWeb 7.6.4 or above, 7.4.8 or above, 7.2.11 or above, and 7.0.11 or above, depending on the currently deployed version.
The patched versions replace the vulnerable snprintffunction calls with MySQL prepared statements, effectively preventing SQL injection attacks by properly separating SQL code from user data.
Organizations can verify successful patching by testing the same exploitation payloads, which should return HTTP 401 Unauthorized responses on patched systems instead of the detailed device information returned by vulnerable versions.
This vulnerability highlights the critical importance of secure coding practices in network security appliances, particularly around input validation and SQL query construction.
Organizations using affected FortiWeb versions should prioritize immediate patching to prevent potential compromise of their web application firewall infrastructure.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates