Free video game cheats are increasingly being used as a delivery mechanism for infostealer malware, exposing unsuspecting gamers to serious cybersecurity risks.
Cheating scandals are well-known in both traditional sports and competitive eSports. Still, malicious actors have now weaponized the demand for cheats, turning platforms like YouTube and Discord into hubs for cybercrime.
The Hidden Danger of Free Video Game Cheats
The gaming industry is a multi-billion-dollar market, with eSports tournaments such as last year’s CS2 PGL Major in Copenhagen boasting prize pools up to $1.25 million.

This competitive environment drives demand for game cheats, which are often subscription-based products offered by underground developers and resellers.
Most gamers are unwilling to pay for premium access, leading them to search for free or “cracked” cheats on questionable forums, YouTube, and even GitHub.
While some free cheats work, they are usually less sophisticated and more likely to be flagged by game anti-cheat systems, resulting in bans.
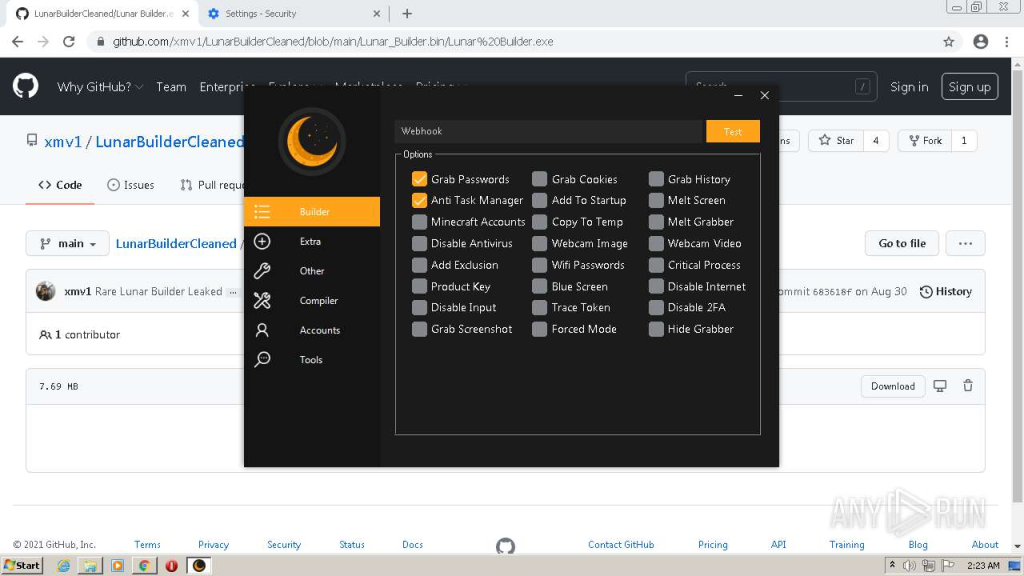
More concerning, however, is that many so-called “free” cheats are fronts for malware campaigns. Cybercriminals deploy info stealers, Discord token grabbers, and Remote Access Trojans (RATs) hidden within cheat downloads, often operating invisibly in the background.
Traffer Teams and the Resale Ecosystem
Threat actors operate organized groups known as “Traffer Teams” that manage malware distribution and monetization.
These teams recruit affiliates (traffers) who spread malware-laden files via popular social platforms, primarily through YouTube videos advertising fake or cracked cheats for titles like Fortnite and Roblox.
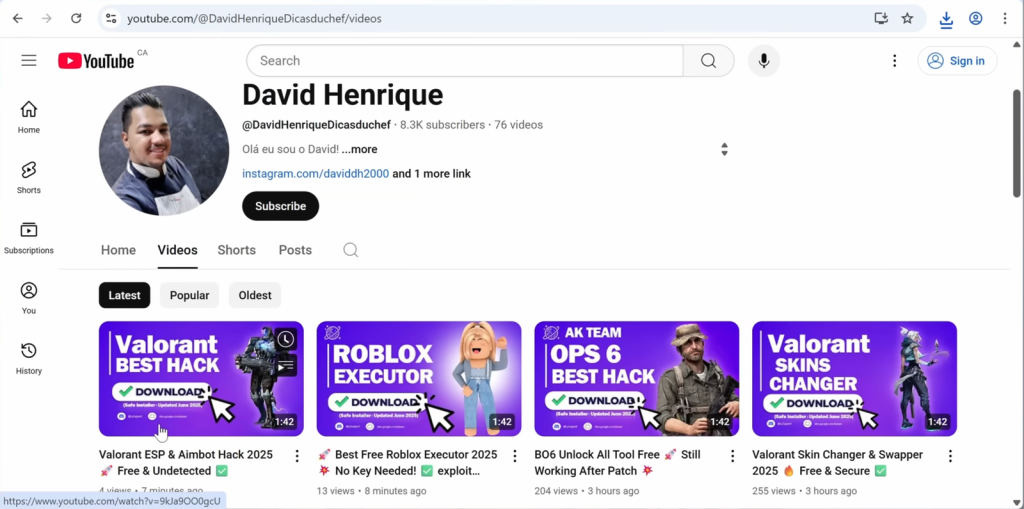
YouTube serves as the initial lure, with videos leading viewers through ad-heavy intermediary services such as Linkvertise before landing them on download sites like MediaFire or Meganz. Each step is designed to both obscure the real source and generate revenue for the trafficker network.
A recent investigation by cybersecurity researcher Eric Parker uncovered the LyTeam, one such trafficker operation distributing malware through Google Sites pages disguised as “Roblox executors” and “Valorant skins changers.”
VirusTotal flagged samples from these schemes as Lumma Stealer, a notorious infostealer malware known for harvesting browser credentials, cryptocurrency wallets, and Discord tokens.
Once executed, these malicious programs silently siphon sensitive data to remote servers, with victims often unaware until their accounts are compromised or funds are missing.
To mitigate the risk, users should avoid running random files from untrusted sources. Antivirus tools, virtual machines, and sandboxes provide additional protection.
Tools like VirusTotal are handy for scanning suspicious files before execution. Staying safe isn’t about paranoia; it’s about digital awareness and caution when downloading or running unofficial software.
Free game cheats may seem tempting, but they often serve as gateways for sophisticated infostealer malware, benefiting cybercriminals while jeopardizing gamers’ accounts, finances, and privacy.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates