The rise of generative AI has transformed the digital landscape, accelerating productivity and creativity for millions. But according to a new technical analysis from Zscaler ThreatLabz, these same AI advancements are arming cybercriminals with unprecedented tools to engineer convincing and dangerous phishing scams.
Recent campaigns in Brazil have demonstrated how threat actors are using GenAI tools like DeepSite AI and BlackBox AI to build replica government websites and siphon money via payment systems such as Pix.
How AI Powers Next-Generation Phishing
ThreatLabz discovered two major phishing templates targeting Brazilians: one impersonating the State Department of Traffic, luring citizens with offers of free driver’s licenses, and another masquerading as the Ministry of Education’s job board with fictitious employment opportunities.
What sets these campaigns apart from traditional phishing is the technical sophistication driven by generative AI. Here’s how these attacks manifest:
1. Hyper-Realistic Website Replicas:
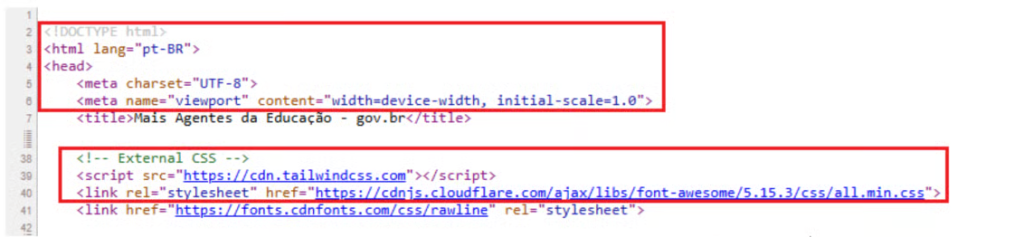
Using GenAI, attackers can quickly clone a government website’s look and feel. Tools like DeepSite AI generate HTML, CSS (notably TailwindCSS styling), and even code with detailed, tutorial-like comments — a signature of AI-generated content. These sites often include non-functional interface elements, such as unresponsive buttons, further hinting at their automated origins.
2. Boosted by SEO Poisoning:
To maximize reach, cybercriminals engage in SEO poisoning, manipulating search engine algorithms so these fraudulent sites appear among the first search results for targeted queries. This increases the likelihood that victims will trust and click these links over legitimate sources.

3. Staged Data Harvesting and API Validation:
Once on the site, visitors are guided through form stages, mimicking genuine processes. Users are asked for the Brazilian tax ID (CPF), address, and other personal details.
Remarkably, the sites employ backend API validation, verifying data in real time to enhance credibility. In some cases, previously stolen data from breaches is used to auto-populate information, further gaining the victim’s trust.
4. Payment Extraction via Pix:
The final step demands a “registration fee” via Pix, Brazil’s instant payment system. Unaware, victims transfer funds directly to the attackers, believing they are completing an official government process.

Technical Hallmarks of GenAI-Generated Phishing
The investigation revealed several technical clues indicating the use of generative AI in these attacks:
- Distinct code structure: Overly detailed code comments, hyper-organized formatting, and visible use of frameworks like TailwindCSS.
- Non-clickable UI components: Visual elements rendered for realism but lacking backend functionality.
- Suspicious domains: Slight misspellings or added hyphens, such as “govbrs[.]com”.
ThreatLabz’s findings highlight the urgent need for updated defense strategies. With GenAI enabling rapid, convincing site replication, phishing attacks are not only more plausible but also easier to scale.
Security experts recommend stringent data validation for organizations and public education for users to distinguish genuine sites from AI-generated fakes.
Fundamentally, the shift to zero trust architectures and AI-powered threat detection solutions is essential, ensuring criminals cannot exploit AI faster than defenders can adapt.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates