Threat actor zeta88 is actively advertising The Gentlemen’s affiliate program across underground forums, promoting a sophisticated cross-platform ransomware-as-a-service (RaaS) operation targeting enterprise environments.
The operation represents a growing trend toward highly modular, platform-agnostic ransomware frameworks that leverage Go and C for maximum compatibility and performance.
Technical Architecture and Capabilities
The Gentlemen’s RaaS boasts an impressive technical arsenal, including multiple specialized lockers for different operating systems.
The Windows and Linux variants are developed in Go, providing efficient resource utilization and cross-compilation advantages.
The ESXi-specific locker, developed in C, maintains a remarkably compact footprint at approximately 32 kilobytes, suggesting significant optimization for virtualized environments a critical target for enterprise ransomware operations seeking maximum impact.
Cryptographic implementation employs industry-standard primitives, including XChaCha20 for stream encryption and Curve25519 for asymmetric operations.
Notably, the framework implements per-file ephemeral keys, meaning each encrypted file receives a unique derived key, significantly complicating decryption attempts and preventing bulk recovery. This architecture demonstrates a sophisticated understanding of cryptographic best practices.
The malware incorporates advanced operational security features, including silent execution modes and timestamp-preservation capabilities, as well as anti-forensic techniques designed to evade detection and complicate incident response investigations.
Persistence mechanisms leverage multiple Windows administration tools, including WMI, WMIC, SCHTASKS, SC, and PowerShell Remoting for both lateral movement and run-on-boot execution, providing multiple infection vectors and redundancy.
Affiliate Economics and Operational Model
The program structure reflects modern RaaS economics: affiliates receive 90 percent of ransom payments while operators retain 10 percent.
Partners maintain direct control over ransom negotiations, reducing operator overhead and allowing specialized criminal groups to leverage their existing victim access and negotiation expertise. This model has proven highly successful against operations such as LockBit and BlackCat.
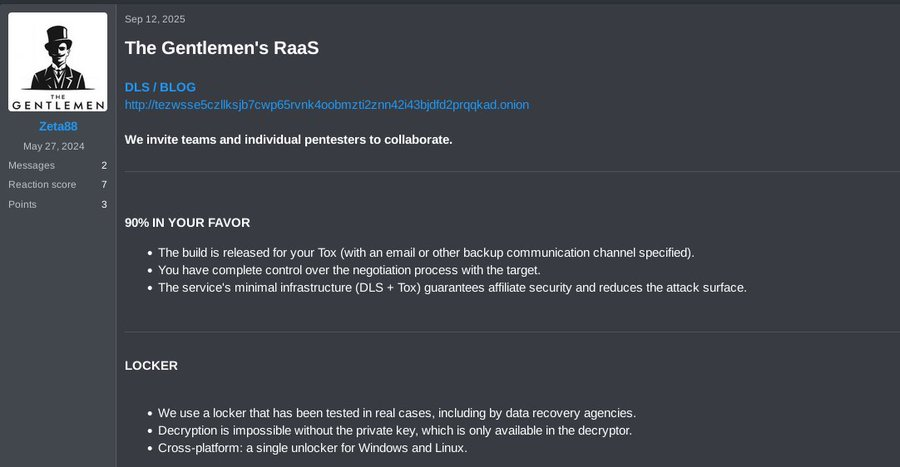
The framework includes critical infrastructure components: a data-leak site for exfiltrated files, password-protected custom builds that prevent law enforcement analysis, and a universal decryptor that supports all platform variants.
Network reconnaissance capabilities include automated discovery of shared resources and encryption, enabling worm-like propagation across connected systems.
Threat Scope and Geographical Restrictions
The operation explicitly excludes targeting within Russia and Commonwealth of Independent States (CIS) nations, a consistent pattern among Russian-affiliated cybercriminal operations, likely reflecting implicit agreements with regional authorities or state actors.
This geographical restriction effectively targets North American, European, and APAC enterprises. The claimed technical specifications remain unverified independent assertions from threat actor marketing materials.
However, the sophisticated design principles, modular architecture, and emphasis on multiple platform support align with established trends in professional ransomware development.
Organizations should prioritize EDR deployment, network segmentation, and backup infrastructure hardening to defend against this emerging threat.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates