A sophisticated Android malware family called GhostGrab has emerged as a significant threat to mobile users, combining credential theft with covert cryptocurrency mining to create a dual-monetization attack against financial institutions and individual victims.
Security researchers at CYFIRMA have documented the malware’s extensive capabilities, revealing a professionally managed operation that leverages Firebase infrastructure for command-and-control operations and targets sensitive financial data across multiple authentication channels.
GhostGrab operates through a two-stage infection mechanism. The initial dropper, distributed via the malicious domain kychelp[.]live, presents users with a fake banking application disguised as a legitimate software update.
Upon installation, the malware exploits the REQUEST_INSTALL_PACKAGES permission to deploy a banking stealer payload without user awareness.
This modular approach enables threat actors to maintain operational flexibility while complicating detection efforts through separate execution stages.
Technical Capabilities and Financial Targeting
The banking stealer module exhibits sophisticated credential-harvesting capabilities that span multiple authentication factors.
The malware intercepts incoming SMS messages containing one-time passwords and banking alerts by registering as an SMS receiver, enabling unauthorized account access and transaction fraud.
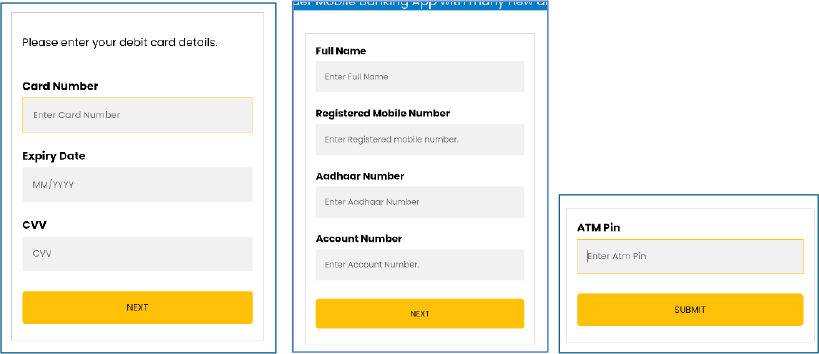
Its WebView phishing infrastructure mimics legitimate banking processes through localized HTML pages that progressively request sensitive information, beginning with KYC details, including Aadhaar numbers, then escalating to debit card information, internet banking credentials, transaction passwords, and ATM PINs.
Analysis of the attacker’s Firebase backend revealed an active operation managing 32 infected devices with over 1,519 captured messages.
Each compromised device’s data includes harvested SMS histories, debit card numbers, CVVs, expiration dates, internet banking credentials, and comprehensive device fingerprints containing Android version, CPU architecture, SIM information per slot, and carrier details.
The malware abuses extensive permissions—READ_SMS, RECEIVE_SMS, SEND_SMS, CALL_PHONE, BIND_NOTIFICATION_LISTENER_SERVICE, and MANAGE_EXTERNAL_STORAGE to enable real-time notification interception and silent message forwarding.
Its command-and-control capabilities allow remote operators to enable call forwarding through USSD sequences, send SMS messages from the compromised device, and configure continuous SMS forwarding to attacker-controlled numbers without user consent.
Persistence and Resource Exploitation
GhostGrab employs advanced persistence techniques through foreground services, combined with silent media playback and alarm receivers that automatically restart the service after system events, including device boot, screen state changes, and connectivity changes.
This multi-layered approach ensures the malware survives OS termination attempts and device reboots.
Simultaneously, the malware executes background cryptocurrency mining operations using a hardcoded Monero wallet address and mining pool endpoints, degrading device performance and battery life while generating direct revenue for threat actors.
Infrastructure analysis linked the campaign to domains including access[.]uasecurity[.]org and accessor[.]pages[.]dev, both recently registered and actively maintained for distribution and C2 operations.
Security researchers recommend users download applications exclusively from the Google Play Store, carefully review app permissions, and monitor devices for unusual battery drain or data consumption.
Organizations should implement mobile device management solutions, block identified malicious domains, and conduct regular employee security awareness training to mitigate exposure to similar multi-purpose malware campaigns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates