Cybersecurity researchers have uncovered a sophisticated malvertising campaign that exploits official GitHub repositories to distribute malware through fake GitHub Desktop client downloads.
This novel attack vector leverages dangling commits within legitimate GitHub repositories to trick users into downloading malicious software disguised as the official GitHub Desktop application.
Attack Chain Exploits Repository Structure
The campaign begins when threat actors fork official GitHub repositories and commit malicious content to README.md files within these forks.
The attack relies on a carefully orchestrated social engineering approach where malvertising campaigns push crafted links directing users to these compromised repository forks.
The malicious links typically follow the pattern https://www.github[.]com/desktop/desktop/tree/1[randomstring]-download-github-client, designed to appear legitimate while hosting malware payloads.
Once users access these fraudulent repository pages, they encounter what appears to be an official GitHub Desktop download page. However, the download link serves a weaponized installer instead of the legitimate GitHub Desktop client.
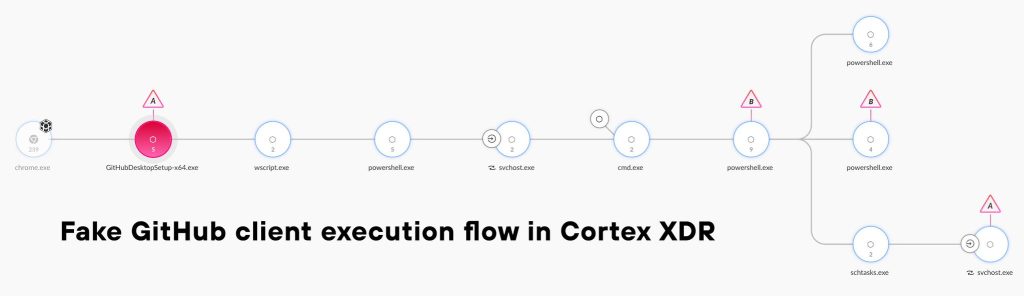
The fake installer, identified as GitHubDesktopSetup-x64.exe, initiates a complex execution chain that begins with chrome.exe as the parent process, followed by wscript.exe, powershell.exe, and multiple instances of malicious PowerShell scripts.
Analysis of the execution flow reveals that the malware employs multi-stage payload delivery through PowerShell scripts and Windows command line utilities.
The initial dropper executes svchost.exe and cmd.exe processes, eventually leading to the deployment of additional malicious executables, including schtasks.exe persistence mechanisms.
The attack chain demonstrates sophisticated evasion techniques, utilizing legitimate Windows processes to mask malicious activities and avoid detection by security solutions.
Technical Implementation and Payload Delivery
The malware distribution mechanism involves embedding encoded payloads within commit messages of the forked repositories. Researchers discovered that the threat actors use base64-encoded strings hidden in commit metadata, which are subsequently decoded and executed by the malicious installer.
This technique allows attackers to store malware payloads directly within GitHub’s infrastructure while maintaining an appearance of legitimacy.
The fake GitHub Desktop client serves as a dropper that establishes persistence on infected systems and downloads secondary payloads. Security telemetry shows the malware creates scheduled tasks and modifies system configurations to ensure continued access.
The campaign targets Windows systems specifically, with the malware performing system discovery operations before exfiltrating collected data to command and control servers.
This attack represents a significant evolution in malvertising tactics, demonstrating how threat actors can abuse trusted platforms like GitHub to distribute malware while bypassing traditional security measures.
Organizations should implement comprehensive endpoint detection and response solutions, educate users about verifying software download sources, and maintain updated security policies regarding software installation from external repositories.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates