An unexpected Zoom document notification recently enticed job seekers into a sophisticated phishing operation, leveraging legitimate Zoom features to bypass suspicion and harvest Gmail credentials in real time.
The attack, cloaked under the guise of “HR Departments” sharing vital documents, showcases the evolving tactics of threat actors who exploit trusted platforms as unwitting accomplices.
From Legitimate Zoom Notification to Credential Theft
The attack began with an email that passed SPF, DKIM, and DMARC checks, appearing to originate from [email protected]. Recipients saw a familiar Zoom Docs UI announcing an “HR Departments invited you to view ‘VIEW DOCUMENTS’” link.
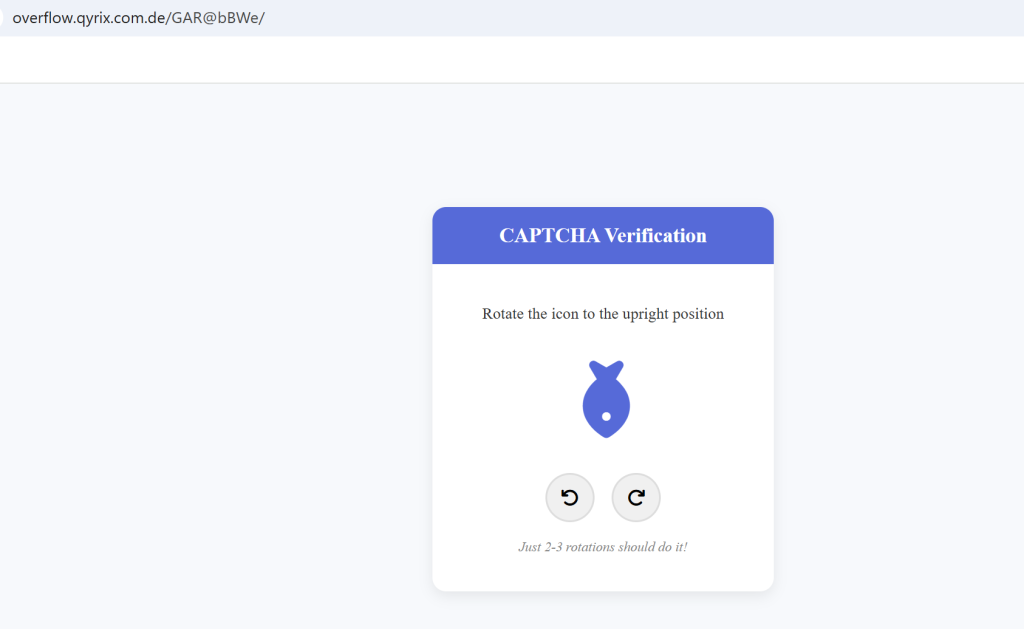
Clicking the link directed victims to an off-Zoom domain overflow.qyrix.com.de where a deceptive “bot protection” gate awaited.
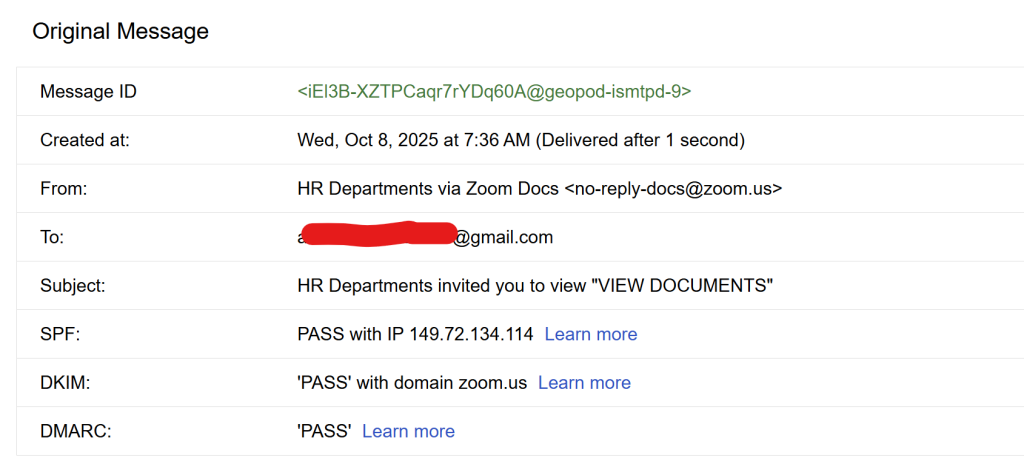
This gate, styled with a press-and-hold button, claimed to verify humanity but in reality served two malicious purposes: thwarting automated analysis and bolstering authenticity for human targets.
After holding the button for a randomized duration, users were redirected to a phishing page mimicking Gmail’s login interface. The URL, however, remained clearly inconsistent with any Google domain.
As victims entered their Gmail address and password, a WebSocket connection instantly relayed the credentials to the attacker’s command-and-control server. Victims reported perceiving a slower response than a static phishing page, hinting at backend validation.
Indeed, the attackers appeared to verify credentials on the fly, allowing them to triage live hits and separate invalid submissions from successful logins.
Technical Red Flags and Defensive Measures
Several indicators can help users and SOC analysts detect similar campaigns:
Suspicious Domain. Any Zoom-originated link pointing to a non-Zoom or non-Google domain should be treated with skepticism.
Unusual Pre-login Gate. A legitimate Gmail login sequence never requires a “bot protection” quiz; its presence signifies an illicit page.
Live WebSocket Exfiltration. Monitoring browser traffic for unrecognized ws:// or wss:// connections can reveal real-time credential siphoning.
To mitigate risk, users who suspect they’ve encountered this scheme should immediately change their passwords via the genuine Google site and enable two-factor authentication.
Analysts should inspect the full email headers, including Received, DKIM, SPF, and DMARC fields, to confirm legitimacy. Organizations can block malicious domains like overflow.qyrix.com.de at the DNS or proxy levels and alert employees about the abuse of trusted communication channels.
Attackers continue to innovate by co-opting familiar services, knowing that users often click links from recognized brands without a second thought. This campaign underscores the imperative for vigilant email inspection, disciplined URL verification, and proactive network monitoring.
When encountering any login prompt outside the official provider domain, users should pause and reassess before submitting credentials. By doing so, they can avoid turning a trusted collaboration tool into an unwitting accomplice in identity theft.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates