Cybercriminals are exploiting Gmail users by posing as recruiters from Google Careers, leveraging phishing campaigns that redirect victims to websites that harvest credentials.
The campaign, which has been active since September 2025, utilizes deceptive email headers and infrastructure tied to legitimate services, such as Salesforce and Cloudflare, to enhance trust and evade detection.
Technical Details of the Campaign
The phishing email arrives with the sender ID reply-ff2913777d64-449_HTML-1463564-534018293-0[@]s12.y.mc.salesforce.com, suggesting links to Salesforce’s marketing automation domain.
Within the message, recipients find a “View the role” button that embeds a redirect through cl.s12.exct.net (hosted on Salesforce ASN). This link leads to a fake Google Careers portal hosted at apply.grecruitingwise.com, a domain fronted by Cloudflare (104.21.47.163).
The spoofed portal mimics a legitimate Google Careers page, complete with captchas, to instill confidence in the user. Victims are initially asked to provide personal details, followed by credentials to their Google account.
The data exfiltration component is visible in the page’s JavaScript (main.js), which routes stolen login data to a command-and-control server at satoshicommands.com.
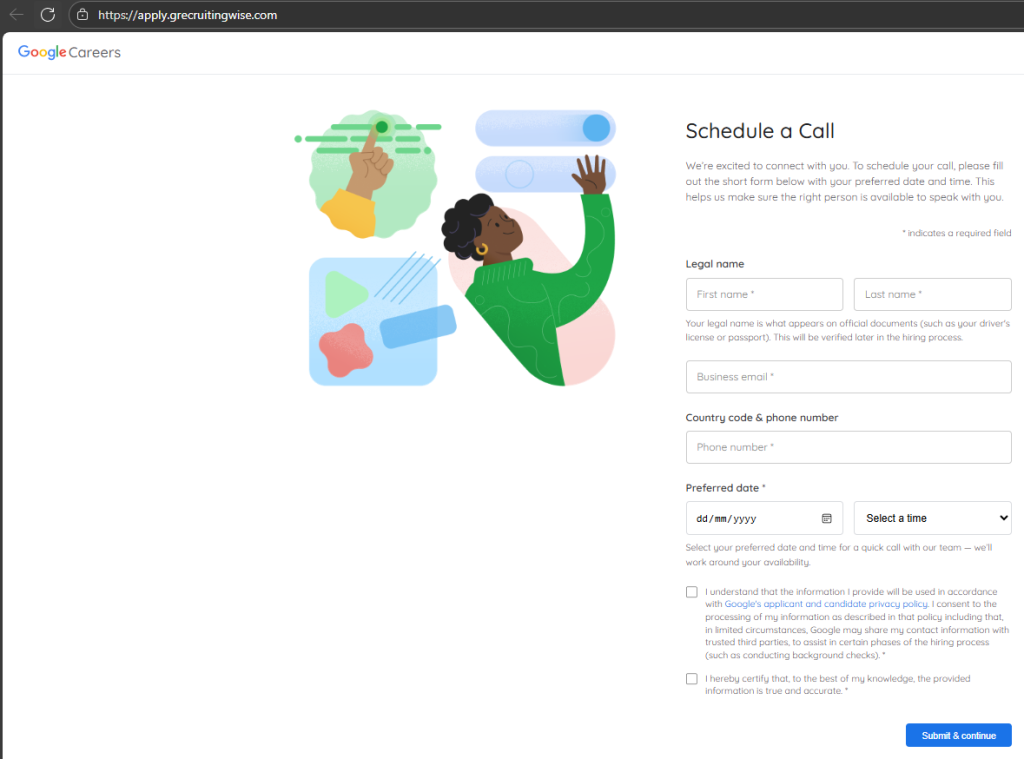
The JavaScript includes logic for handling multiple credential-stealing workflows, such as OTP prompts, re-entering email addresses, and handling incorrect passwords.
For example, if a victim mistypes their credentials, the script loops them back into the phishing flow until accurate information is harvested. The attacker employs WebSocket connections and scheduled HTTP POST requests (/gw.php) to exfiltrate sensitive session data in real time.
Infrastructure and Broader Targeting
Researchers have identified multiple related domains associated with this campaign, suggesting a larger infrastructure designed to impersonate not only Google but also other well-known brands.
Additional domains include apply.grecruitdigital.com, hire.gteamhirehub.com, apply.gcareercandidates.com, and others targeting companies in sectors ranging from PUMA (puma-remotejobcenter.vercel.app) to Robert Half (robert-half-hiring-marketing-remotl.vercel.app) and Moburst (moburst-check.vercel.app).
Samples captured on sandbox platforms like ANY.RUN reveals that these phishing kits are modular and adaptive, using the same backend server (satoshicommands.com) across different brand lures.
VirusTotal collections and graph analysis confirm the interconnection of these domains and their shared infrastructure, highlighting a coordinated phishing-as-a-service operation.
Indicators of Compromise (IOCs) highlight the scope of the campaign:
- Email source:
s12.y.mc.salesforce.com - Malicious redirect:
cl.s12.exct.net(13.110.204.9) - Fake portal:
apply.grecruitingwise.com(104.21.47.163) - Data exfiltration:
satoshicommands.com
Mitigation
Security analysts recommend heightened awareness of unsolicited recruitment emails, especially those requesting account verification or login credentials.
Organizations should apply email filtering policies, DNS blocking for malicious domains, and user awareness training. End-users are advised to verify job communications through official Google Careers portals and never enter credentials into unfamiliar websites.
This latest phishing wave highlights attackers’ growing sophistication in combining trusted SaaS delivery infrastructure, brand impersonation, and modular phishing kits to compromise business and personal accounts at scale.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates