Security researchers have uncovered a sophisticated social engineering attack that uses a fake Google Meet interface to trick users into manually executing malicious PowerShell commands on their systems.
The attack, discovered after a WordPress site owner reported suspicious URLs, represents a dangerous evolution in malware delivery tactics that bypasses traditional security measures by exploiting human behavior rather than technical vulnerabilities.
The malicious HTML page meticulously mimics Google Meet’s authentic interface, complete with embedded styles, logos, and layouts that require no external resources to load.
When users attempt to join a meeting by clicking the “Join now” button, they encounter a fabricated “Microphone Permission Denied” error message designed to create urgency and concern.
The social engineering mechanism operates through a carefully orchestrated sequence of fake error modals.
After the initial join attempt fails, users are presented with a “Can’t join the meeting” dialog that offers a “Try Fix” button as the apparent solution.
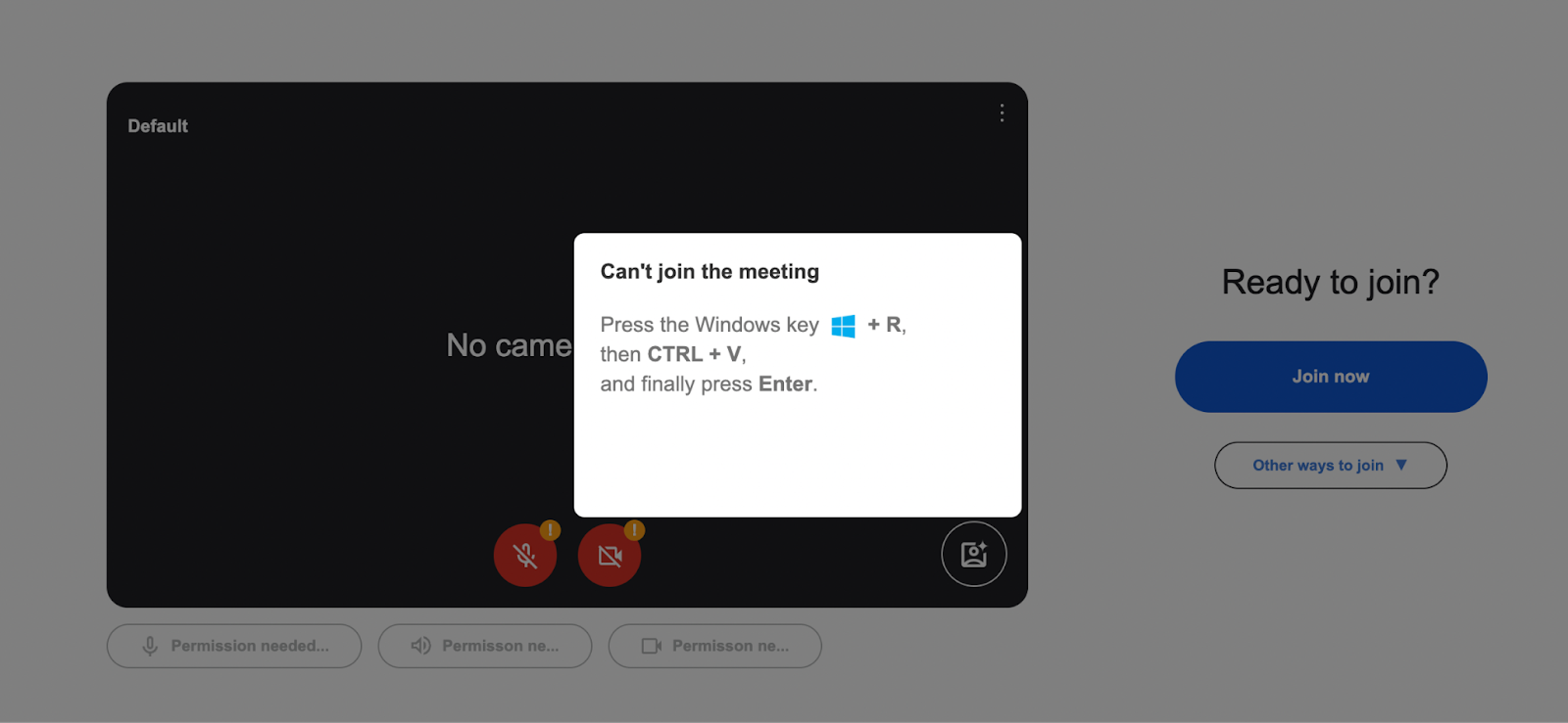
This button triggers a JavaScript function that silently copies a malicious PowerShell command to the user’s clipboard while simultaneously displaying detailed instructions on how to open PowerShell and execute the copied command.
The attack’s effectiveness lies in its exploitation of users’ natural troubleshooting instincts and their trust in familiar interfaces.
The fake error messages create a plausible technical scenario that most users would attempt to resolve quickly, especially in professional contexts where joining meetings promptly is important.
Trojan Through Obfuscated Code
The PowerShell command copied to users’ clipboards contains a heavily obfuscated script that downloads and executes additional malware components from the compromised website itself.
The primary payload, hosted in a file called “XR.txt,” uses XOR encoding and string manipulation techniques to hide its true purpose from security scanners.
Upon execution, the script displays a “Verification complete!” message box to reassure victims that their troubleshooting action was successful, while malicious operations continue silently in the background.
The malware then downloads and installs a Remote Access Trojan (RAT) called “noanti-vm.bat” into the user’s AppData directory.
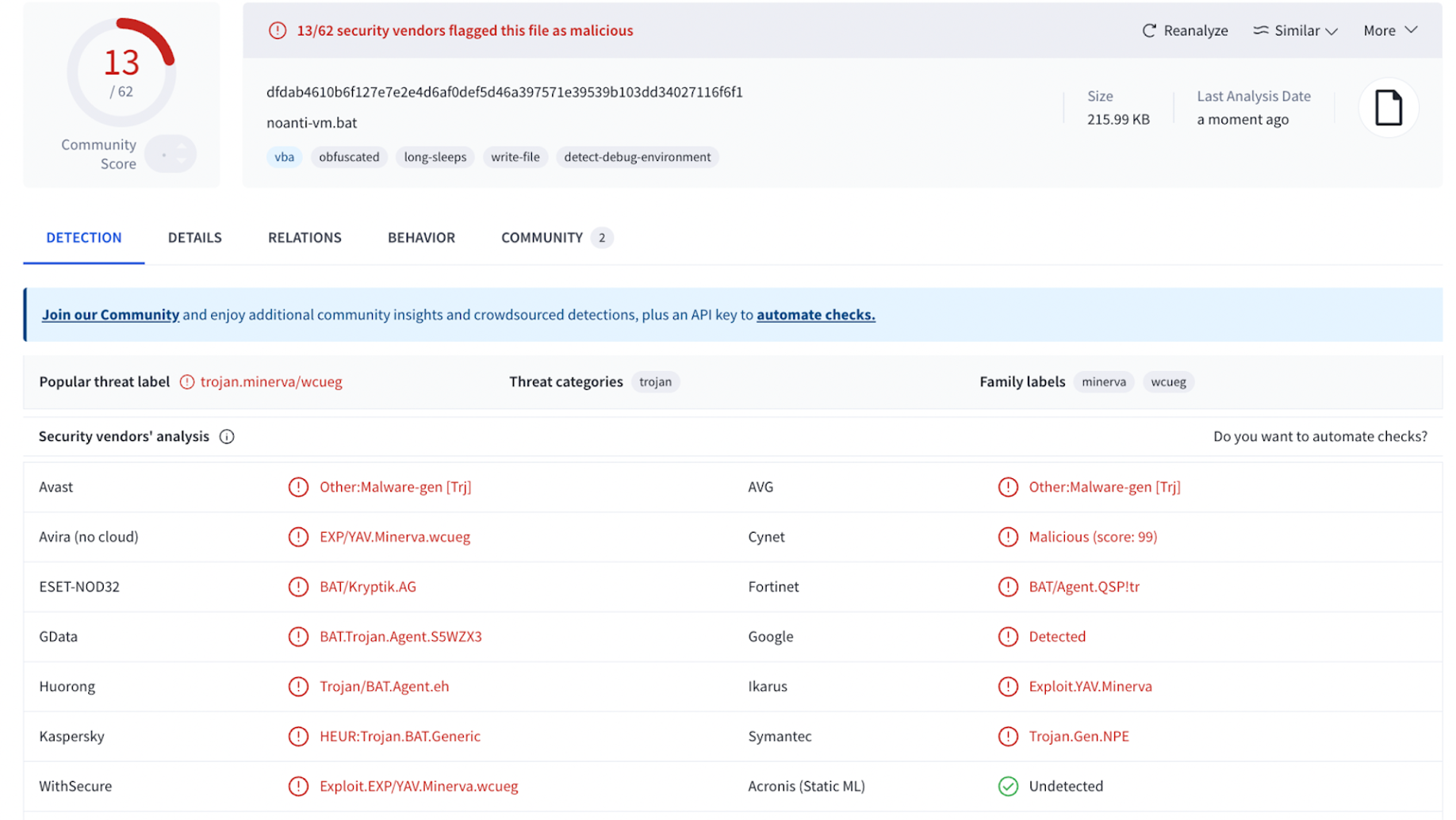
This RAT file employs advanced evasion techniques, including string slicing and environment variable manipulation to construct commands character by character from seemingly random values.
Security analysis on VirusTotal confirms the file’s malicious nature, with multiple antivirus engines detecting it as a Trojan or RAT.
Enhanced User Awareness
The successful execution of this attack can lead to devastating consequences, including complete system compromise, data theft, and the installation of additional malware such as ransomware or keyloggers.
The attack’s self-contained nature makes it particularly dangerous, as it leaves minimal forensic traces and doesn’t rely on external resources that security systems might detect.
Security experts recommend implementing comprehensive defense strategies including regular malware scans, software updates, strong access controls, and web application firewalls.
However, they emphasize that user education remains the most critical defense against such social engineering attacks, as technical solutions alone cannot prevent users from voluntarily executing malicious commands.
The incident underscores the evolving threat landscape where attackers increasingly target human psychology rather than technical vulnerabilities, making security awareness training essential for organizations and individuals alike.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.