A sophisticated threat group designated UNC6040 has successfully compromised multiple organizations through elaborate voice phishing campaigns, specifically targeting Salesforce instances to steal sensitive data and demand bitcoin ransoms.
The Google Threat Intelligence Group has documented the evolution of this financially motivated cluster from simple social engineering to advanced data exfiltration operations, which have impacted businesses globally, including a recent incident involving Google’s own corporate Salesforce environment.
Advanced Vishing Tactics Target Salesforce Infrastructure
UNC6040 employs highly convincing voice phishing (vishing) techniques where operators impersonate IT support personnel during telephone calls to English-speaking employees at multinational corporations.
The attackers guide victims to authorize malicious connected apps within their organization’s Salesforce portal, often using modified versions of Salesforce’s legitimate Data Loader application.
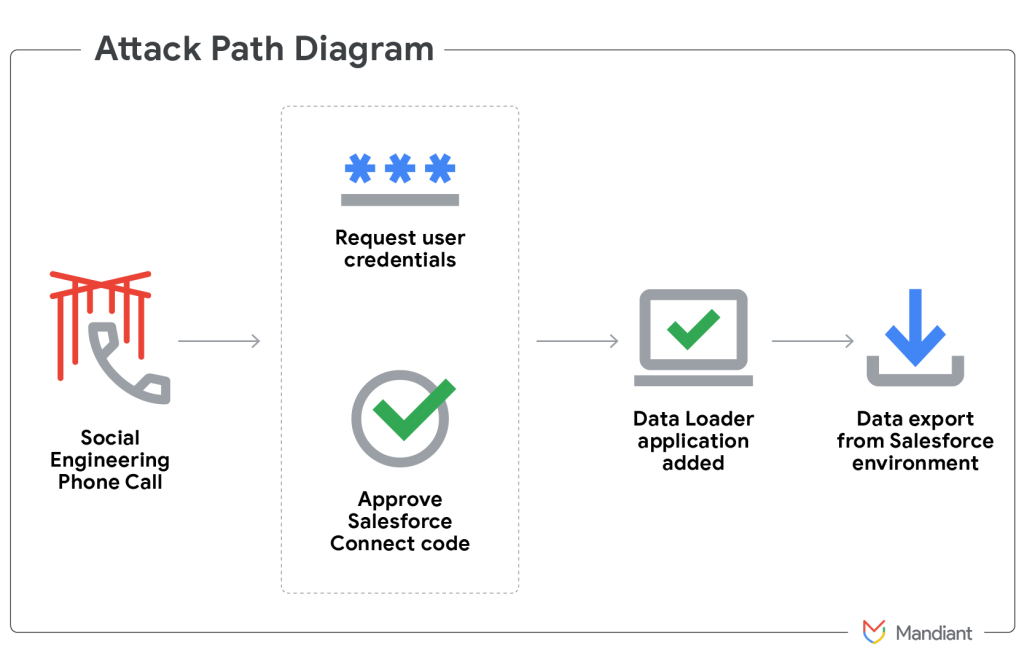
This OAuth-enabled tool grants threat actors extensive capabilities to access, query, and exfiltrate sensitive information directly from compromised Salesforce environments.
The group’s tactics, techniques, and procedures (TTPs) have evolved significantly, shifting from standard Data Loader applications to custom Python scripts that automate data collection.
Attackers now utilize Mullvad VPN and TOR networks to obscure their digital footprints, while registering malicious applications using compromised accounts from unrelated organizations.
During social engineering calls, victims are directed to Okta phishing panels hosted on attacker infrastructure, where they unwittingly provide credentials and multi-factor authentication (MFA) codes that facilitate further network penetration.
Extortion Operations and Defense Strategies
Following the successful data theft, a related group, tracked as UNC6240, initiates extortion activities, sometimes waiting several months before demanding bitcoin payments within 72-hour deadlines.
These threat actors consistently claim affiliation with the notorious ShinyHunters hacking collective and appear to be preparing a data leak site (DLS) to increase pressure on victims who refuse payment.
Organizations can implement several critical defenses against these sophisticated attacks.
Security teams should enforce the principle of least privilege for data access tools, particularly restricting the “API Enabled” permission required for Data Loader functionality.
Implementing IP-based access restrictions can counter unauthorized access attempts from commercial VPNs, while rigorous management of connected applications prevents installation of malicious tools.
Salesforce Shield’s Transaction Security Policies enable automated monitoring of large data downloads and suspicious API usage patterns.
The campaign demonstrates the continued effectiveness of social engineering against enterprise defenses, emphasizing the shared responsibility model for cloud security where robust platform controls must be complemented by proper configuration, access management, and comprehensive user training programs.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates