In August 2025, cybersecurity researchers at Arctic Wolf® uncovered a sophisticated campaign leveraging Google Ads and GitHub infrastructure to deploy the novel “GPUGate” malware, uniquely engineered to evade standard analysis and compromise high-value IT targets.
The attackers manipulate Google’s sponsored search results for keywords like “GitHub Desktop,” enticing users with what appears to be an official download link.
However, these ads redirect to a single GitHub commit boasting legitimate repository details, yet bearing a hidden malicious link that whisks victims to a trojanized application hosted on the lookalike domain gitpage[.]app.
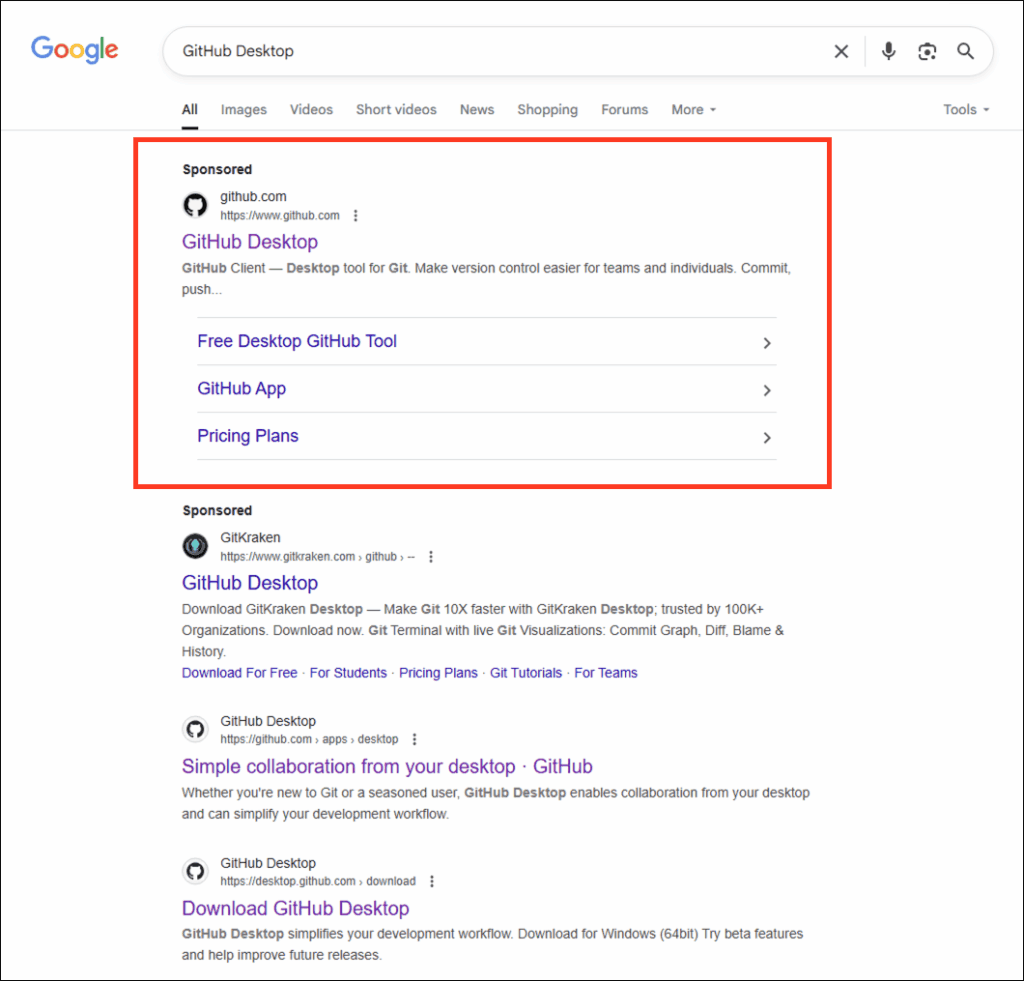
Once users download the decoy installer, “GitHubDesktopSetup-x64.exe”—a bloated 128 MB Microsoft Software Installer—the infection chain commences.
The oversized file mimics the real GitHub Desktop installer to avoid easy detection and includes more than 100 dummy executables intended to thwart security sandboxes.
Crucially, the malware contains tightly woven routines that only execute on systems with genuine GPUs, exploiting the OpenCL API for a hardware-gated decryption sequence.
Technical Insights: GPU-Gated Evasion and Payload Deployment
GPUGate distinguishes itself with a two-stage decryption process hinging on the victim’s GPU details. An OpenCL kernel within the installer checks for a GPU device name of at least ten characters.
If the name falls short or if no GPU is present, the payload remains encrypted and inactive, effectively bypassing most virtualized analysis environments commonly used by security professionals.
The kernel generates either a “good” AES key (for real hardware) or a fake key (for suspected analysis systems) using the device name as a condition. Only systems with the proper hardware receive the real, decrypted malicious payload.
Once activated, the malware’s PowerShell scripts establish persistence via scheduled tasks, evade antivirus detection by disabling Microsoft Defender scans on key folders, and elevate privileges using legitimate Windows mechanisms.
They may then download secondary payloads—including ransomware modules, info-stealers, and credential harvesters by extracting ZIP archives and sideloading DLLs.
The campaign has primarily targeted IT sector professionals across Western Europe, leveraging “Computers and Consumer Electronics” ad labels for maximum reach.
With native Russian language proficiency evident in code comments and multi-layered evasion, researchers suspect involvement of advanced threat actors focused on supply chain compromise, credential theft, and ransomware deployment.
GPUGate’s innovative use of hardware-based decryption represents a significant escalation in malware design, upending traditional analysis and requiring defenders to develop novel approaches in endpoint detection and process monitoring.
Security experts urge organizations to review exclusion lists, monitor PowerShell activity, and avoid clicking sponsored downloads for critical software—even when links appear legitimate.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates